eNSP防火墙实现GRE over IPSec
1.实验拓扑
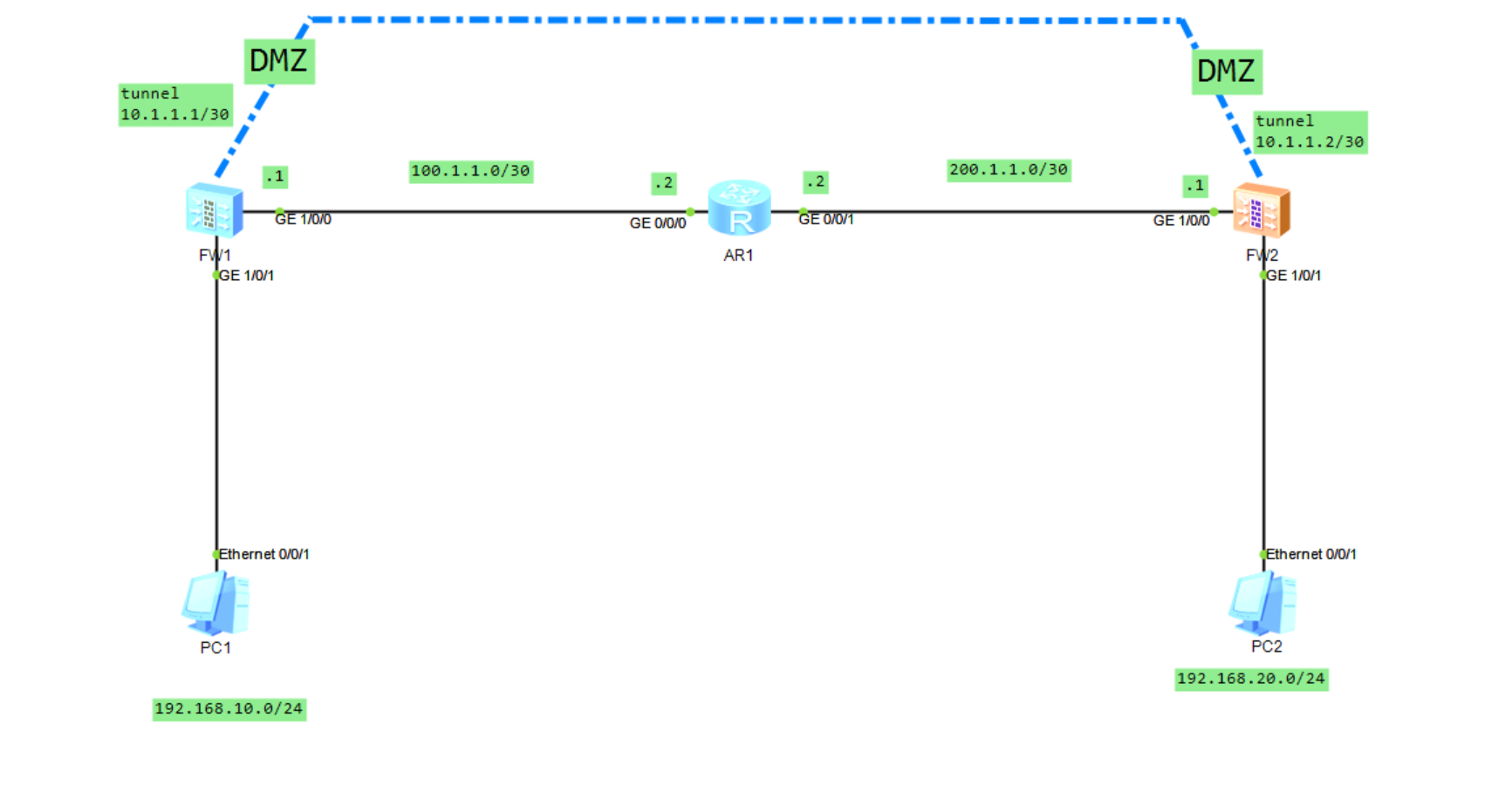
2.GRE配置(安全策略)
2.1 PC1访问PC2配置
[FW1-policy-security]di th
2025-05-22 10:53:20.930
#
security-policy
rule name trust->dmz
source-zone trust
destination-zone dmz
source-address 192.168.10.0 mask 255.255.255.0
action permit
rule name local->untrust
source-zone local
destination-zone untrust
action permit
rule name untrust->local
source-zone untrust
destination-zone local
service gre
action permit
#
[FW2-policy-security]di th
2025-05-22 10:53:35.090
#
security-policy
rule name untrust->local
source-zone untrust
destination-zone local
service gre
action permit
rule name dmz->trust
source-zone dmz
destination-zone trust
action permit
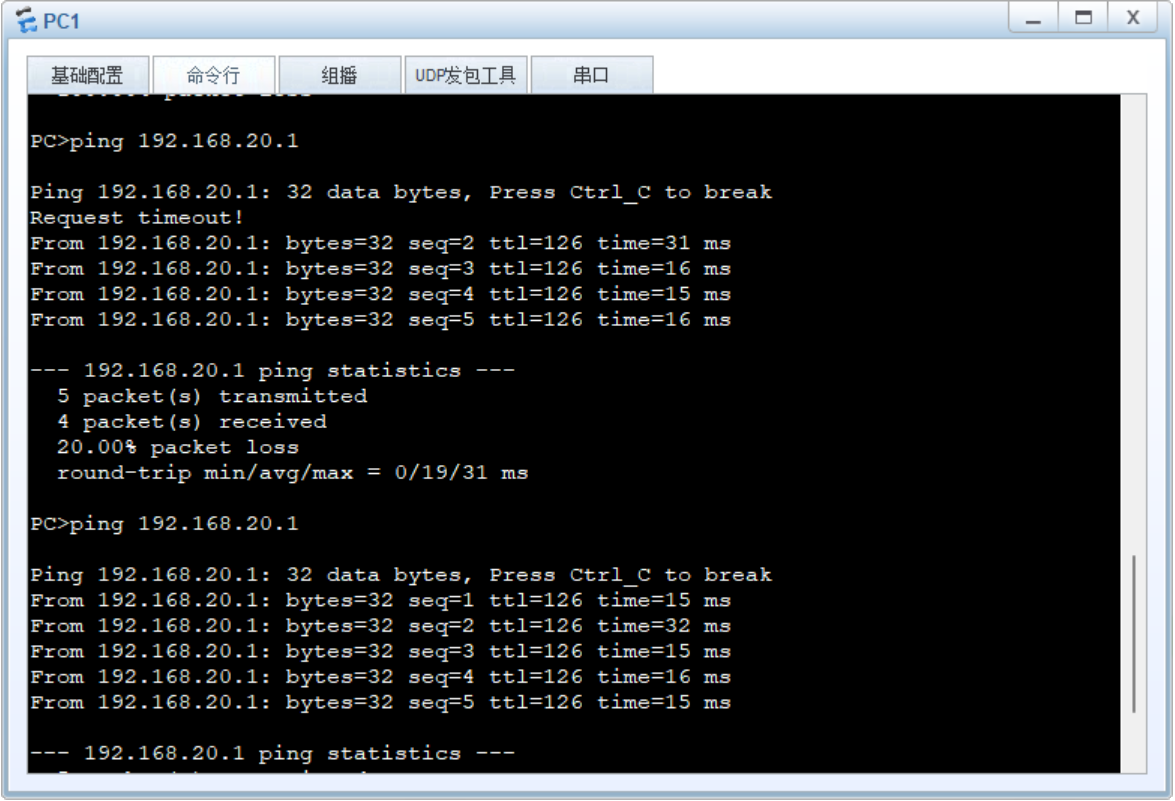
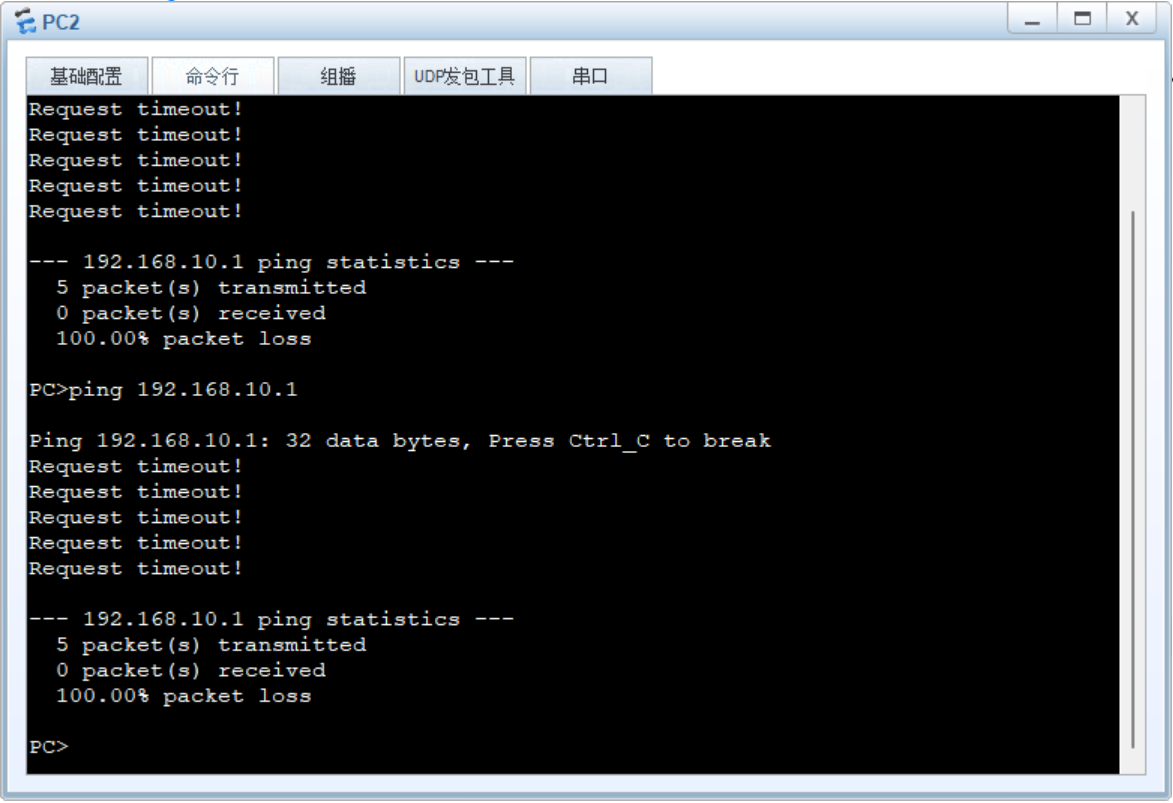
2.2PC2访问PC1
[FW1-policy-security]di th
2025-05-22 11:00:28.520
#
security-policy
rule name trust->dmz
source-zone trust
destination-zone dmz
source-address 192.168.10.0 mask 255.255.255.0
action permit
rule name local->untrust
source-zone local
destination-zone untrust
action permit
rule name untrust->local
source-zone untrust
destination-zone local
service gre
action permit
rule name dmz->trust
source-zone dmz
destination-zone trust
destination-address 192.168.10.0 mask 255.255.255.0
action permit
[FW2-policy-security]di th
2025-05-22 11:02:45.960
#
security-policy
rule name untrust->local
source-zone untrust
destination-zone local
service gre
action permit
rule name dmz->trust
source-zone dmz
destination-zone trust
action permit
rule name trust->dmz
source-zone trust
destination-zone dmz
source-address 192.168.20.0 mask 255.255.255.0
action permit
rule name local->untrust
source-zone local
destination-zone untrust
source-address 10.1.1.0 mask 255.255.255.252
action permit
#
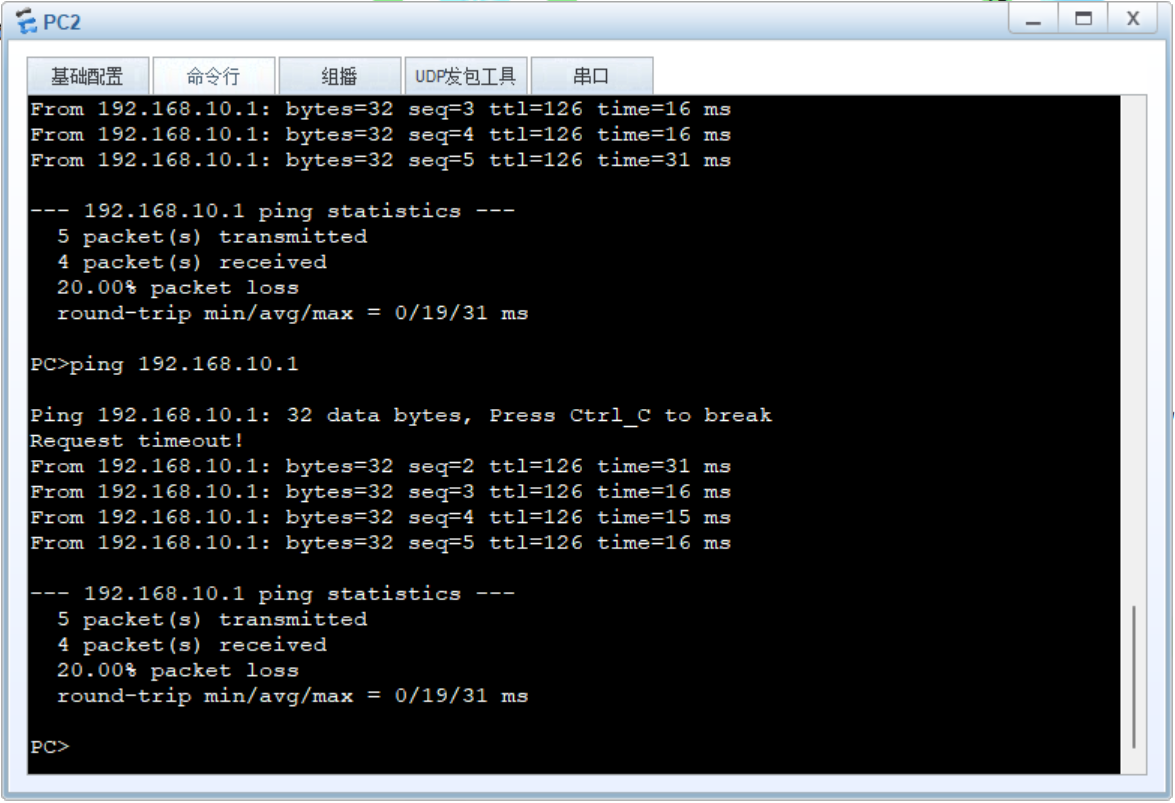
但是该报文未加密
3.IPSec 配置
3.1配置感兴趣流
[FW1-acl-adv-3000]di th
2025-05-22 11:06:40.120
#
acl number 3000
rule 5 permit ip source 100.1.1.1 0 destination 200.1.1.1 0
#
[FW2-acl-adv-3000]di th
2025-05-22 11:07:15.920
#
acl number 3000
rule 5 permit ip source 200.1.1.1 0 destination 100.1.1.1 0
#
3.2配置IKE提议
[FW1]ike proposal 1
[FW1-ike-proposal-1]authentication-method pre-share
[FW1-ike-proposal-1]encryption-algorithm 3des
[FW1-ike-proposal-1]authentication-algorithm sha2-256
[FW1-ike-proposal-1]dh group14
FW2同上
[FW2-ike-proposal-1]di th
2025-05-22 12:22:18.030
#
ike proposal 1
encryption-algorithm 3des
dh group14
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
#
3.3配置IKE对等体
[FW1]ike peer huawei
[FW1-ike-peer-huawei]remote-address 200.1.1.1
[FW1-ike-peer-huawei]pre-shared-key huawei@123
[FW1-ike-peer-huawei]ike-proposal 1
FW2同上
[FW2-ike-peer-huawei]di th
2025-05-22 11:13:49.870
#
ike peer huawei
pre-shared-key %^%#y9T]7O]t=%J9^_%^Y%V:@K1S)}'Q,9oLrx'R5g],%^%#
ike-proposal 1
remote-address 100.1.1.1
3.4配置IPSec 提议
[FW1]ipsec proposal huawei
[FW1-ipsec-proposal-huawei]transform ah-esp
[FW1-ipsec-proposal-huawei]ah authentication-algorithm sha2-256
[FW1-ipsec-proposal-huawei]esp authentication-algorithm sha2-256
[FW1-ipsec-proposal-huawei]esp encryption-algorithm 3des
FW2同上
[FW2-ipsec-proposal-huawei]di th
2025-05-22 12:27:03.280
#
ipsec proposal huawei
transform ah-esp
ah authentication-algorithm sha2-256
esp authentication-algorithm sha2-256
esp encryption-algorithm 3des
#
3.5配置IPSec策略
[FW1]ipsec policy huawei 1 isakmp
[FW1-ipsec-policy-isakmp-huawei-1]security acl 3000
[FW1-ipsec-policy-isakmp-huawei-1]ike-peer huawei
[FW1-ipsec-policy-isakmp-huawei-1]proposal huawei
[FW2-ipsec-policy-isakmp-huawei-1]di th
2025-05-22 11:20:57.870
#
ipsec policy huawei 1 isakmp
security acl 3000
ike-peer huawei
proposal huawei
3.6出接口调用IPSec策略
[FW1]int g1/0/0
[FW1-GigabitEthernet1/0/0]ipsec policy huawei
[FW2]int g1/0/0
[FW2-GigabitEthernet1/0/0]ipsec policy huawei
4.IPSec配置(安全策略)
[FW1-policy-security]di th
rule name untrust->local
source-zone untrust
destination-zone local
service gre
service ospf
service protocol 50
service protocol 51
service protocol udp destination-port 500
action permit
[FW2-policy-security]di th
security-policy
rule name untrust->local
source-zone untrust
destination-zone local
service gre
service ospf
service protocol 50
service protocol 51
service protocol udp destination-port 500
action permit
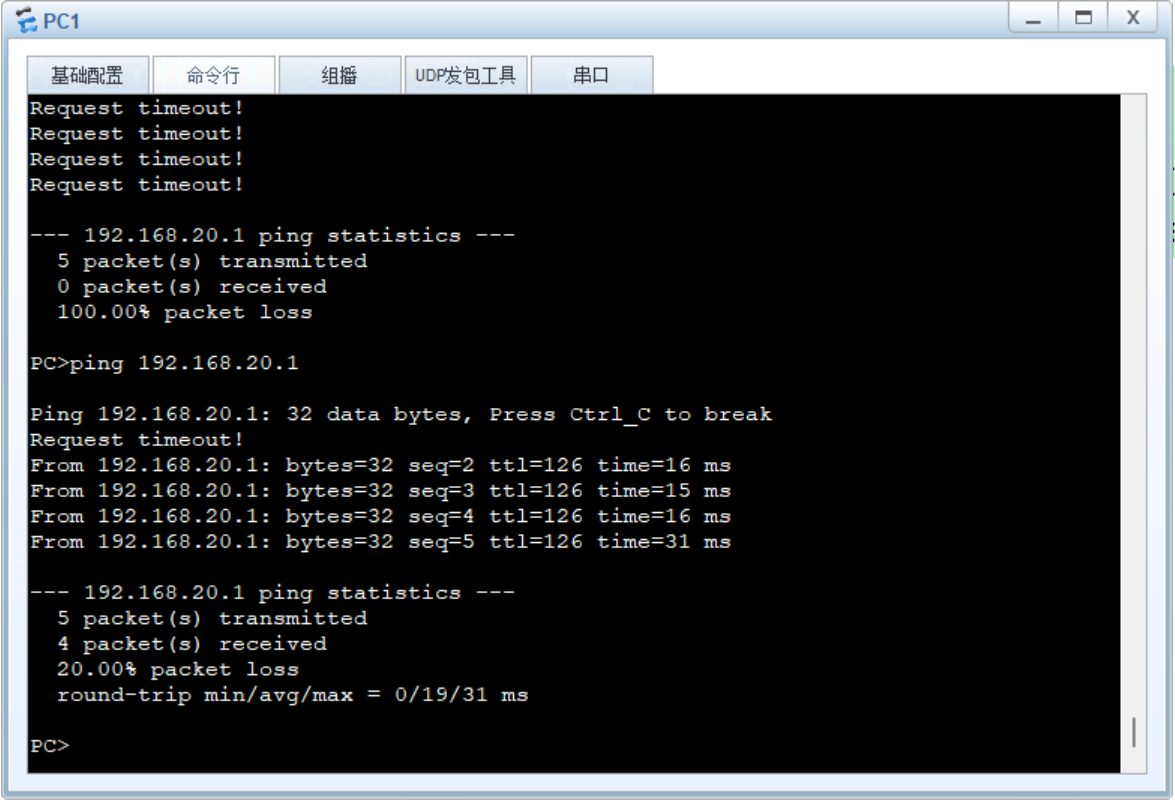
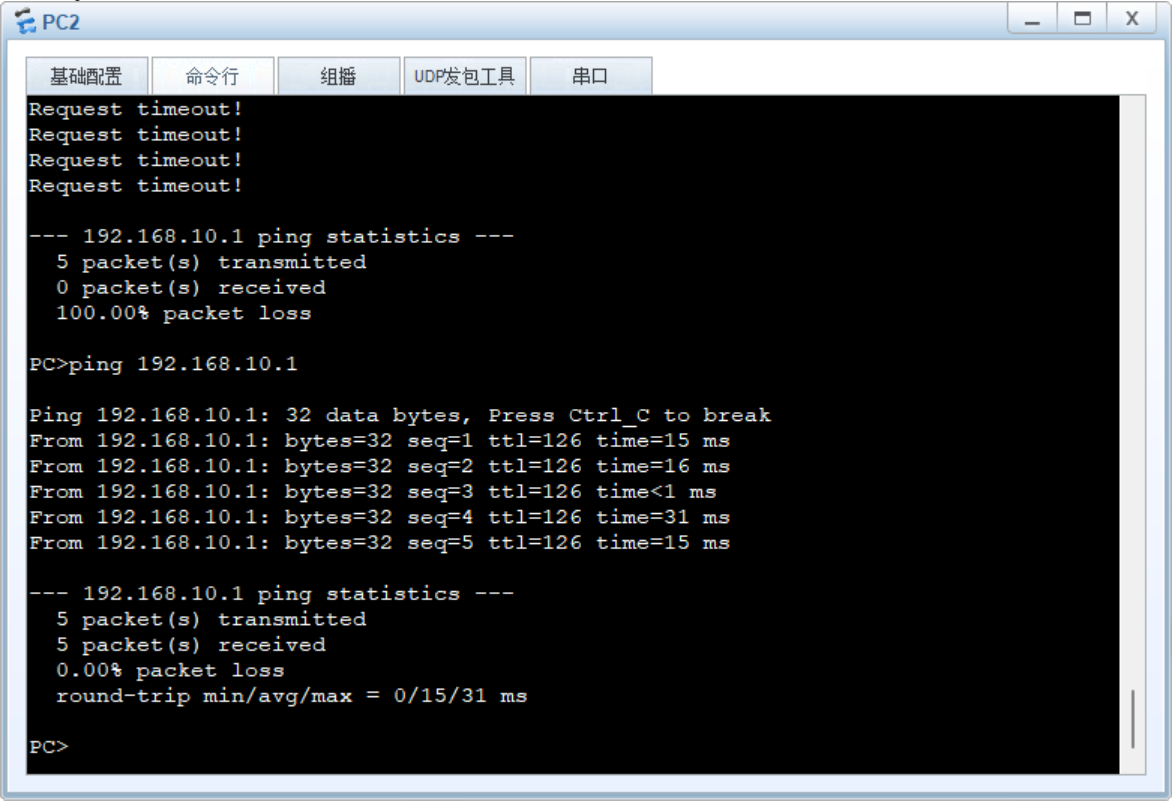
5.实验验证
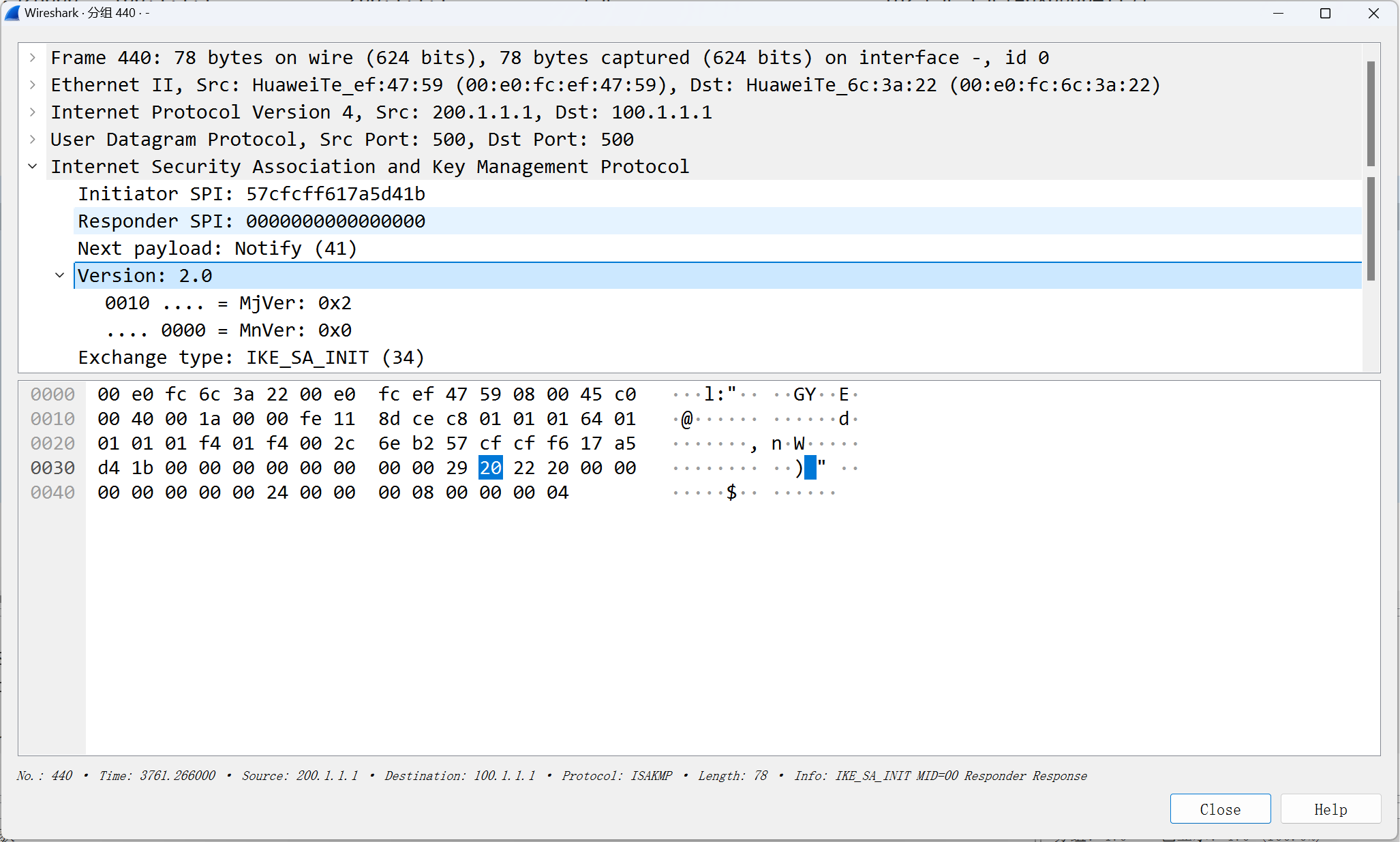
华为设备默认使用IKEv2