Linux822 shell:expect 批量
问题
[root@dns ~]# cat /etc/ssh/sshd_config
# $OpenBSD: sshd_config,v 1.100 2016/08/15 12:32:04 naddy Exp $# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.# This sshd was compiled with PATH=/usr/local/bin:/usr/bin# The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options override the
# default value.# If you want to change the port on a SELinux system, you have to tell
# SELinux about this change.
# semanage port -a -t ssh_port_t -p tcp #PORTNUMBER
#
Port 3333
#AddressFamily any
#ListenAddress 0.0.0.0
#ListenAddress ::HostKey /etc/ssh/ssh_host_rsa_key
#HostKey /etc/ssh/ssh_host_dsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_key# Ciphers and keying
#RekeyLimit default none# Logging
#SyslogFacility AUTH
SyslogFacility AUTHPRIV
#LogLevel INFO# Authentication:#LoginGraceTime 2m
PermitRootLogin yes
#StrictModes yes
#MaxAuthTries 6
#MaxSessions 10#PubkeyAuthentication yes# The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2
# but this is overridden so installations will only check .ssh/authorized_keys
AuthorizedKeysFile .ssh/authorized_keys#AuthorizedPrincipalsFile none#AuthorizedKeysCommand none
#AuthorizedKeysCommandUser nobody# For this to work you will also need host keys in /etc/ssh/ssh_known_hosts
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes# To disable tunneled clear text passwords, change to no here!
#PasswordAuthentication yes
#PermitEmptyPasswords no
PasswordAuthentication yes# Change to no to disable s/key passwords
#ChallengeResponseAuthentication yes
ChallengeResponseAuthentication no# Kerberos options
#KerberosAuthentication no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
#KerberosGetAFSToken no
#KerberosUseKuserok yes# GSSAPI options
GSSAPIAuthentication yes
GSSAPICleanupCredentials no
#GSSAPIStrictAcceptorCheck yes
#GSSAPIKeyExchange no
#GSSAPIEnablek5users no# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the ChallengeResponseAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via ChallengeResponseAuthentication may bypass
# the setting of "PermitRootLogin without-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and ChallengeResponseAuthentication to 'no'.
# WARNING: 'UsePAM no' is not supported in Red Hat Enterprise Linux and may cause several
# problems.
UsePAM yes#AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
X11Forwarding yes
#X11DisplayOffset 10
#X11UseLocalhost yes
#PermitTTY yes
#PrintMotd yes
#PrintLastLog yes
#TCPKeepAlive yes
#UseLogin no
#UsePrivilegeSeparation sandbox
#PermitUserEnvironment no
#Compression delayed
#ClientAliveInterval 0
#ClientAliveCountMax 3
#ShowPatchLevel no
#UseDNS yes
#PidFile /var/run/sshd.pid
#MaxStartups 10:30:100
#PermitTunnel no
#ChrootDirectory none
#VersionAddendum none# no default banner path
#Banner none# Accept locale-related environment variables
AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES
AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
AcceptEnv XMODIFIERS# override default of no subsystems
Subsystem sftp /usr/libexec/openssh/sftp-server# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
[root@dns ~]# vim /etc/ssh/sshd_config
[root@dns ~]# grep -v ^# /etc/ssh/sshd_configPort 22HostKey /etc/ssh/ssh_host_rsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_keySyslogFacility AUTHPRIVPermitRootLogin yesAuthorizedKeysFile .ssh/authorized_keysPasswordAuthentication yesChallengeResponseAuthentication noGSSAPIAuthentication yes
GSSAPICleanupCredentials noUsePAM yesX11Forwarding yesAcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES
AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
AcceptEnv XMODIFIERSSubsystem sftp /usr/libexec/openssh/sftp-server[root@dns ~]# systemctl status ssh
Unit ssh.service could not be found.
[root@dns ~]# systemctl status openssh
Unit openssh.service could not be found.
[root@dns ~]#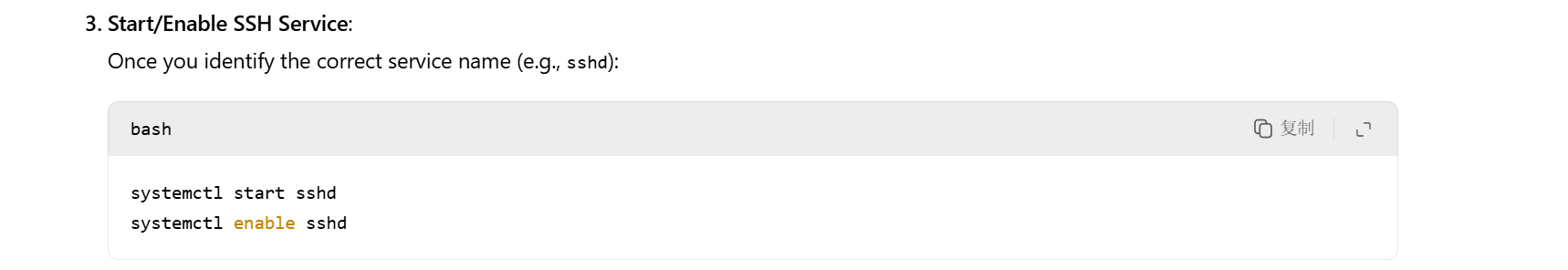
[root@web ~]# cat expect4.sh
#!/bin/bash
while read ip pass
do/usr/bin/expect << -END >/dev/null 2>&1spawn ssh root@$ipexpect {"yes/no" { send "yes\r";exp_continue }"password:" { send "$pass\r" }}expect "#" { send "useradd yy1;rm -rf /tmp/*;exit\r" }expect eofEND
done < ip.txt
[root@web ~]# chmod +x expect4.sh
您在 /var/spool/mail/root 中有邮件
[root@web ~]# ./expect4.sh
./expect4.sh:行13: 警告:立即文档在第 4 行被文件结束符分隔 (需要 `-END')
./expect4.sh:行14: 语法错误: 未预期的文件结尾
您在 /var/spool/mail/root 中有邮件
[root@web ~]#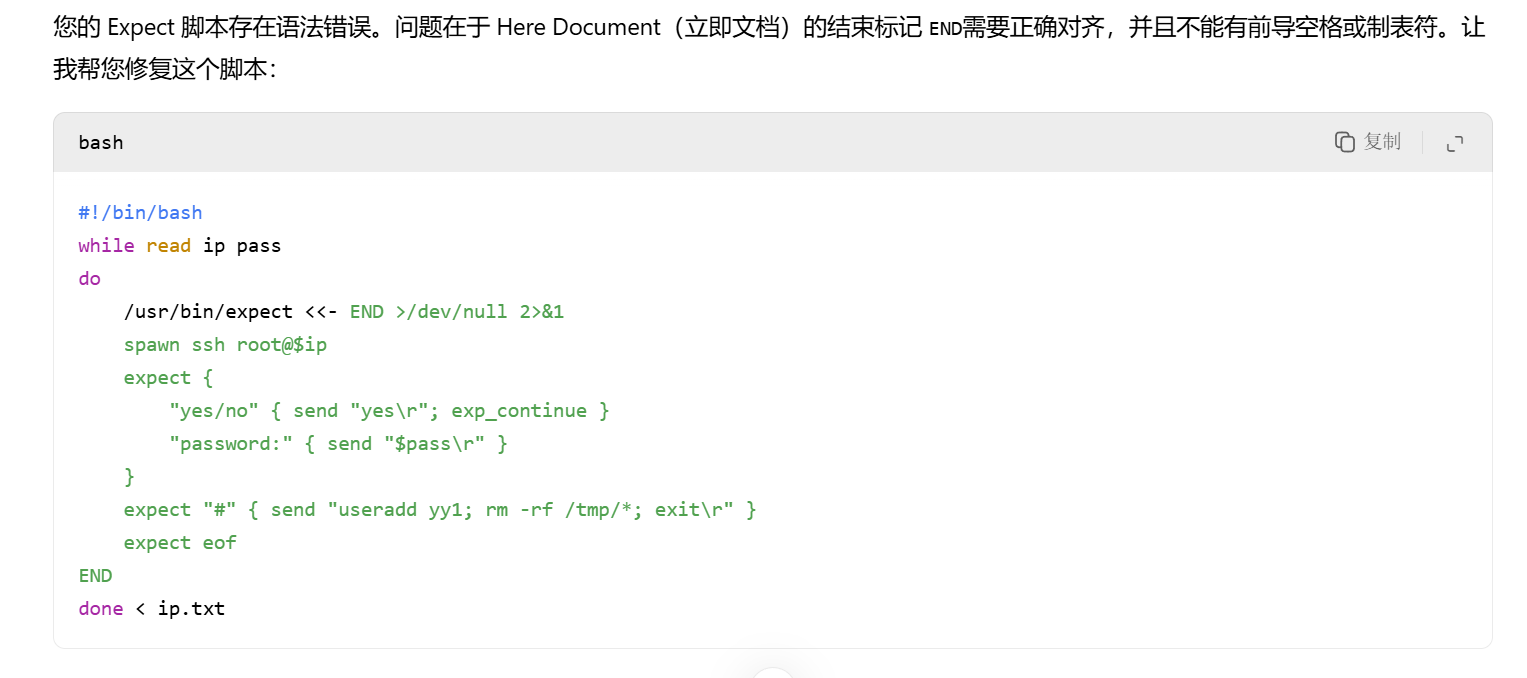
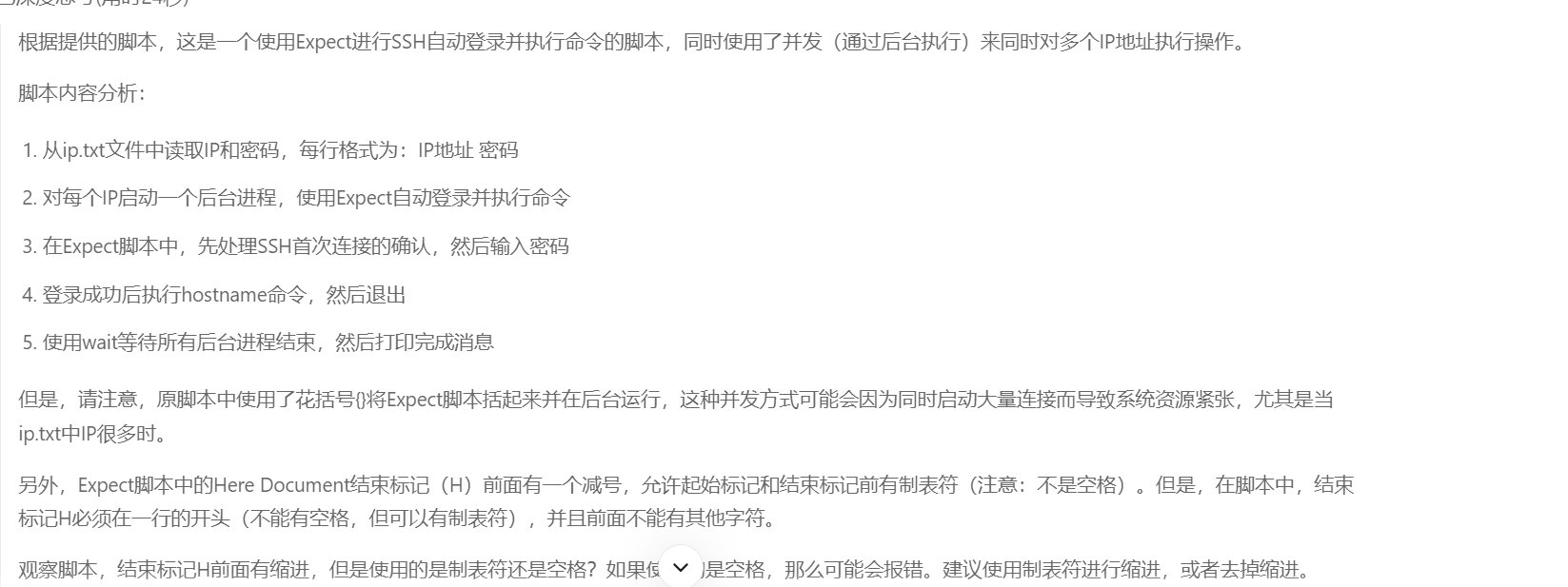
[root@web ~]# cat expect5.sh
cat ip.txt|while read ip pass
do{/usr/bin/expect <<-Hspawn ssh root@$ipexpect {"yes/no"{ send "yes\r";exp_continue }"password:"{ send "$pass\r" }}expect "#"send "hostname\r"send "exit\r"expect eofH}&
done
wait
echo "user is ok...."
[root@web ~]# ./expect5.sh
user is ok....
[root@web ~]# spawn ssh root@192.168.235.100
spawn ssh root@192.168.235.200
root@192.168.235.200's password: root@192.168.235.100's password: 123456
bash: 123456: 未找到命令...
[root@web ~]#Permission denied, please try again.
root@192.168.235.100's password: Permission denied, please try again.
root@192.168.235.200's password: 123456
bash: 123456: 未找到命令...
[root@web ~]#
shell
expect4.sh
[root@web ~]# cat expect4.sh
#!/bin/bash
while read ip pass
do/usr/bin/expect <<-END >/dev/null 2>&1spawn ssh root@$ipexpect {"yes/no" { send "yes\r";exp_continue }"password:" { send "$pass\r" }}expect "#" { send "useradd yy1;rm -rf /tmp/*;exit\r" }expect eof
END
done < ip.txt
[root@web ~]# ./expect4.shexpect5.sh
记录
root@192.168.235.20's password:┌────────────────────────────────────────────────────────────────────┐│ • MobaXterm 20.0 • ││ (SSH client, X-server and networking tools) ││ ││ ➤ SSH session to root@192.168.235.20 ││ • SSH compression : ✘ ││ • SSH-browser : ✔ ││ • X11-forwarding : ✔ (remote display is forwarded through SSH) ││ • DISPLAY : ✔ (automatically set on remote server) ││ ││ ➤ For more info, ctrl+click on help or visit our website │└────────────────────────────────────────────────────────────────────┘Last login: Thu Aug 21 20:31:58 2025 from 192.168.235.1
[root@web ~]# cat expect4.sh
cat: expect4.sh: 没有那个文件或目录
您在 /var/spool/mail/root 中有新邮件
[root@web ~]# ls
1828.txt cuser1.sh httpd-2.4.37 luvk.txt pho.sh tail5 ur.sh
1837.txt dir1 httpd-2.4.37.tar.bz2 mysql-5.6.31 php-7.2.17 tail6 user1c.sh
1.txt dn.sh id.sh mysql-5.6.31.tar.gz php-7.2.17.tar.xz tail7 useradd1.sh
2-1.java expect1.sh initial-setup-ks.cfg no.txt ping2.sh tail.txt useradd.sh
2.java expect.sh inotify-tools-3.13.tar.gz null ping.sh ta.txt userad.sh
=6 fi1.txt judgeprimeok.sh num.sh primeok.sh test1.sh user.sh
alll1 file20.java judgeprime.sh ok process1.sh testcfor.sh vsftpd1.sh
anaconda-ks.cfg file23.java lc3.txt okl process.sh testff1.sh vsftpd2.sh
app for51.sh lc4.txt pas3.txt psok.sh testff.sh vsftpdins.sh
apr-1.5.2 for5.sh lc5.txt pas4.txt readme7 testfor2.sh vsftpdok.sh
apr-1.5.2.tar.bz2 ftpok.sh lc6.txt pas5.txt readme.txt testfor3.sh vsftpd.sh
apr-util-1.5.4 ftp.sh lc7.txt pas6.txt serverOk.sh testfor4.sh vstest.sh
apr-util-1.5.4.tar.bz2 head lc.sh pas7.txt service-s.sh testforf.sh wordpress
axel-2.4 head2.txt lc.txt passwd1.txt shift.sh testfor.sh wordpress-4.7.3-zh_CN.tar.gz
axel-2.4.tar.gz head4 lk.txt paste1.txt Steam.dll uc.sh yearok.sh
bb.conf head5 luad.txt pa.txt stuc.sh uname2.sh
cc.conf head6 luck.sh ph1.txt sum.sh unameok.sh
classfi.sh head7 lucky1.txt phonenum.txt tail uname.sh
code he.txt lucky.txt phon.txt tail4 url.sh
[root@web ~]# cat expect1.sh
#!/usr/bin/expect
set ip 192.168.235.200
set pass 123456
set timeout 5
spawn ssh root@$ip
expect {"yes/no" { send "yes\r";exp_continue }"password:" { send "$pass\r" }
}
interact
[root@web ~]# cat expect2.sh
cat: expect2.sh: 没有那个文件或目录
您在 /var/spool/mail/root 中有邮件
[root@web ~]# vim expect3.sh
[root@web ~]# cat ip.txt
cat: ip.txt: 没有那个文件或目录
[root@web ~]# vim ip.txt
您在 /var/spool/mail/root 中有邮件
[root@web ~]# cat ip.txt
192.168.235.100 123456
192.
[root@web ~]# ssh root@192.168.235.200
root@192.168.235.200's password:
Permission denied, please try again.
root@192.168.235.200's password:
Last failed login: Fri Aug 22 22:21:21 CST 2025 from 192.168.235.20 on ssh:notty
There was 1 failed login attempt since the last successful login.
Last login: Thu Aug 21 22:57:49 2025 from 192.168.235.200
[root@client ~]# exit
登出
Connection to 192.168.235.200 closed.
[root@web ~]# ssh root@192.168.235.100
ssh: connect to host 192.168.235.100 port 22: Connection refused
您在 /var/spool/mail/root 中有邮件
[root@web ~]# ssh -p 3333 root@192.168.235.100
root@192.168.235.100's password:
Permission denied, please try again.
root@192.168.235.100's password:
Last failed login: Fri Aug 22 22:23:07 CST 2025 from 192.168.235.20 on ssh:notty
There was 1 failed login attempt since the last successful login.
Last login: Fri Aug 22 22:16:46 2025 from 192.168.235.1
[root@dns ~]# exit
登出
Connection to 192.168.235.100 closed.
[root@web ~]# cat ip.txt
192.168.235.100 123456
192.
您在 /var/spool/mail/root 中有邮件
[root@web ~]# vim ip.txt
您在 /var/spool/mail/root 中有邮件
[root@web ~]# cat ip.txt
192.168.235.100 123456
192.168.235.200 123456
[root@web ~]# vim expect4.sh
您在 /var/spool/mail/root 中有邮件
[root@web ~]# cat expect4.sh
#!/bin/bash
while read ip pass
do/usr/bin/expect << -END >/dev/null 2>&1spawn ssh root@$ipexpect {"yes/no" { send "yes\r";exp_continue }"password:" { send "$pass\r" }}expect "#" { send "useradd yy1;rm -rf /tmp/*;exit\r" }expect eofEND
done < ip.txt
[root@web ~]# chmod +x expect4.sh
您在 /var/spool/mail/root 中有邮件
[root@web ~]# ./expect4.sh
./expect4.sh:行13: 警告:立即文档在第 4 行被文件结束符分隔 (需要 `-END')
./expect4.sh:行14: 语法错误: 未预期的文件结尾
您在 /var/spool/mail/root 中有邮件
[root@web ~]# vim expect4.sh
您在 /var/spool/mail/root 中有邮件
[root@web ~]# cat expect4.sh
#!/bin/bash
while read ip pass
do/usr/bin/expect << -END >/dev/null 2>&1spawn ssh root@$ipexpect {"yes/no" { send "yes\r";exp_continue }"password:" { send "$pass\r" }}expect "#" { send "useradd yy1;rm -rf /tmp/*;exit\r" }expect eof
END
done < ip.txt
[root@web ~]# ./expect4.sh
./expect4.sh:行13: 警告:立即文档在第 4 行被文件结束符分隔 (需要 `-END')
./expect4.sh:行14: 语法错误: 未预期的文件结尾
[root@web ~]# vim expect4.sh
您在 /var/spool/mail/root 中有邮件
[root@web ~]# cat expect4.sh
#!/bin/bash
while read ip pass
do/usr/bin/expect <<-END >/dev/null 2>&1spawn ssh root@$ipexpect {"yes/no" { send "yes\r";exp_continue }"password:" { send "$pass\r" }}expect "#" { send "useradd yy1;rm -rf /tmp/*;exit\r" }expect eof
END
done < ip.txt
[root@web ~]# ./expect4.sh
[root@web ~]# vim expect5.sh
您在 /var/spool/mail/root 中有邮件
[root@web ~]# cat expect5.sh
cat ip.txt|while read ip pass
do{/usr/bin/expect <<-Hspawn ssh root@$ipexpect {"yes/no"{ send "yes\r";exp_continue }"password:"{ send "$pass\r" }}expect "#"send "hostname\r"send "exit\r"expect eofH}&
done
wait
echo "user is ok...."
[root@web ~]# chmod +x expect5.sh
您在 /var/spool/mail/root 中有邮件
[root@web ~]# ./expect5.sh
user is ok....
[root@web ~]# spawn ssh root@192.168.235.100
spawn ssh root@192.168.235.200
root@192.168.235.200's password: root@192.168.235.100's password: 123456
bash: 123456: 未找到命令...
[root@web ~]#Permission denied, please try again.
root@192.168.235.100's password: Permission denied, please try again.
root@192.168.235.200's password: 123456
bash: 123456: 未找到命令...
[root@web ~]#caozx26@192.168.235.200's password:
▒▒▒ʱ▒▒ܾ▒
caozx26@192.168.235.200's password:┌────────────────────────────────────────────────────────────────────┐│ • MobaXterm 20.0 • ││ (SSH client, X-server and networking tools) ││ ││ ➤ SSH session to caozx26@192.168.235.200 ││ • SSH compression : ✘ ││ • SSH-browser : ✔ ││ • X11-forwarding : ✔ (remote display is forwarded through SSH) ││ • DISPLAY : ✔ (automatically set on remote server) ││ ││ ➤ For more info, ctrl+click on help or visit our website │└────────────────────────────────────────────────────────────────────┘Last failed login: Fri Aug 22 22:16:52 CST 2025 from 192.168.235.1 on ssh:notty
There was 1 failed login attempt since the last successful login.
Last login: Thu Aug 21 20:38:44 2025 from 192.168.235.1
[caozx26@client ~]$ ls
1828.txt 1.java 2.java 3.java 5.java app1 inotify-tools-3.13 公共 视频 文档 音乐
1837.txt 2041 35.txt 4.java app file22.txt inotify-tools-3.13.tar.gz 模板 图片 下载 桌面
[caozx26@client ~]$ cat /etc/ssh/sshd_config
cat: /etc/ssh/sshd_config: 权限不够
[caozx26@client ~]$ sudo su
[sudo] caozx26 的密码:
[root@client caozx26]# cat /etc/ssh/sshd_config
# $OpenBSD: sshd_config,v 1.100 2016/08/15 12:32:04 naddy Exp $# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.# This sshd was compiled with PATH=/usr/local/bin:/usr/bin# The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options override the
# default value.# If you want to change the port on a SELinux system, you have to tell
# SELinux about this change.
# semanage port -a -t ssh_port_t -p tcp #PORTNUMBER
#
#Port 22
#AddressFamily any
#ListenAddress 0.0.0.0
#ListenAddress ::HostKey /etc/ssh/ssh_host_rsa_key
#HostKey /etc/ssh/ssh_host_dsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_key# Ciphers and keying
#RekeyLimit default none# Logging
#SyslogFacility AUTH
SyslogFacility AUTHPRIV
#LogLevel INFO# Authentication:#LoginGraceTime 2m
#PermitRootLogin yes
#StrictModes yes
#MaxAuthTries 6
#MaxSessions 10#PubkeyAuthentication yes# The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2
# but this is overridden so installations will only check .ssh/authorized_keys
AuthorizedKeysFile .ssh/authorized_keys#AuthorizedPrincipalsFile none#AuthorizedKeysCommand none
#AuthorizedKeysCommandUser nobody# For this to work you will also need host keys in /etc/ssh/ssh_known_hosts
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes# To disable tunneled clear text passwords, change to no here!
#PasswordAuthentication yes
#PermitEmptyPasswords no
PasswordAuthentication yes# Change to no to disable s/key passwords
#ChallengeResponseAuthentication yes
ChallengeResponseAuthentication no# Kerberos options
#KerberosAuthentication no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
#KerberosGetAFSToken no
#KerberosUseKuserok yes# GSSAPI options
GSSAPIAuthentication yes
GSSAPICleanupCredentials no
#GSSAPIStrictAcceptorCheck yes
#GSSAPIKeyExchange no
#GSSAPIEnablek5users no# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the ChallengeResponseAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via ChallengeResponseAuthentication may bypass
# the setting of "PermitRootLogin without-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and ChallengeResponseAuthentication to 'no'.
# WARNING: 'UsePAM no' is not supported in Red Hat Enterprise Linux and may cause several
# problems.
UsePAM yes#AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
X11Forwarding yes
#X11DisplayOffset 10
#X11UseLocalhost yes
#PermitTTY yes
#PrintMotd yes
#PrintLastLog yes
#TCPKeepAlive yes
#UseLogin no
#UsePrivilegeSeparation sandbox
#PermitUserEnvironment no
#Compression delayed
#ClientAliveInterval 0
#ClientAliveCountMax 3
#ShowPatchLevel no
#UseDNS yes
#PidFile /var/run/sshd.pid
#MaxStartups 10:30:100
#PermitTunnel no
#ChrootDirectory none
#VersionAddendum none# no default banner path
#Banner none# Accept locale-related environment variables
AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES
AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
AcceptEnv XMODIFIERS# override default of no subsystems
Subsystem sftp /usr/libexec/openssh/sftp-server# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
[root@client caozx26]# tail -3 /etc/passwd
xiaocao:x:1001:1001::/home/xiaocao:/bin/bash
kefu:x:1002:1002::/home/kefu:/bin/bash
yy1:x:1003:1003::/home/yy1:/bin/bash
[root@client caozx26]# ls /tmp
vmware-root_714-2965382611
[root@client caozx26]# ls /tmp
[root@client caozx26]# tail -4 /etc/passwd
apache:x:48:48:Apache:/usr/share/httpd:/sbin/nologin
xiaocao:x:1001:1001::/home/xiaocao:/bin/bash
kefu:x:1002:1002::/home/kefu:/bin/bash
yy1:x:1003:1003::/home/yy1:/bin/bash
[root@client caozx26]#root@192.168.235.100's password:┌────────────────────────────────────────────────────────────────────┐│ • MobaXterm 20.0 • ││ (SSH client, X-server and networking tools) ││ ││ ➤ SSH session to root@192.168.235.100 ││ • SSH compression : ✘ ││ • SSH-browser : ✔ ││ • X11-forwarding : ✔ (remote display is forwarded through SSH) ││ • DISPLAY : ✔ (automatically set on remote server) ││ ││ ➤ For more info, ctrl+click on help or visit our website │└────────────────────────────────────────────────────────────────────┘Last login: Thu Aug 21 20:37:39 2025 from 192.168.235.1
[root@dns ~]# ls
ab.txt anaconda-ks.cfg bb.conf initial-setup-ks.cfg kk.txt ok sun.conf sun.txt
[root@dns ~]# cat /etc/ssh/sshd_config
# $OpenBSD: sshd_config,v 1.100 2016/08/15 12:32:04 naddy Exp $# This is the sshd server system-wide configuration file. See
# sshd_config(5) for more information.# This sshd was compiled with PATH=/usr/local/bin:/usr/bin# The strategy used for options in the default sshd_config shipped with
# OpenSSH is to specify options with their default value where
# possible, but leave them commented. Uncommented options override the
# default value.# If you want to change the port on a SELinux system, you have to tell
# SELinux about this change.
# semanage port -a -t ssh_port_t -p tcp #PORTNUMBER
#
Port 3333
#AddressFamily any
#ListenAddress 0.0.0.0
#ListenAddress ::HostKey /etc/ssh/ssh_host_rsa_key
#HostKey /etc/ssh/ssh_host_dsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_key# Ciphers and keying
#RekeyLimit default none# Logging
#SyslogFacility AUTH
SyslogFacility AUTHPRIV
#LogLevel INFO# Authentication:#LoginGraceTime 2m
PermitRootLogin yes
#StrictModes yes
#MaxAuthTries 6
#MaxSessions 10#PubkeyAuthentication yes# The default is to check both .ssh/authorized_keys and .ssh/authorized_keys2
# but this is overridden so installations will only check .ssh/authorized_keys
AuthorizedKeysFile .ssh/authorized_keys#AuthorizedPrincipalsFile none#AuthorizedKeysCommand none
#AuthorizedKeysCommandUser nobody# For this to work you will also need host keys in /etc/ssh/ssh_known_hosts
#HostbasedAuthentication no
# Change to yes if you don't trust ~/.ssh/known_hosts for
# HostbasedAuthentication
#IgnoreUserKnownHosts no
# Don't read the user's ~/.rhosts and ~/.shosts files
#IgnoreRhosts yes# To disable tunneled clear text passwords, change to no here!
#PasswordAuthentication yes
#PermitEmptyPasswords no
PasswordAuthentication yes# Change to no to disable s/key passwords
#ChallengeResponseAuthentication yes
ChallengeResponseAuthentication no# Kerberos options
#KerberosAuthentication no
#KerberosOrLocalPasswd yes
#KerberosTicketCleanup yes
#KerberosGetAFSToken no
#KerberosUseKuserok yes# GSSAPI options
GSSAPIAuthentication yes
GSSAPICleanupCredentials no
#GSSAPIStrictAcceptorCheck yes
#GSSAPIKeyExchange no
#GSSAPIEnablek5users no# Set this to 'yes' to enable PAM authentication, account processing,
# and session processing. If this is enabled, PAM authentication will
# be allowed through the ChallengeResponseAuthentication and
# PasswordAuthentication. Depending on your PAM configuration,
# PAM authentication via ChallengeResponseAuthentication may bypass
# the setting of "PermitRootLogin without-password".
# If you just want the PAM account and session checks to run without
# PAM authentication, then enable this but set PasswordAuthentication
# and ChallengeResponseAuthentication to 'no'.
# WARNING: 'UsePAM no' is not supported in Red Hat Enterprise Linux and may cause several
# problems.
UsePAM yes#AllowAgentForwarding yes
#AllowTcpForwarding yes
#GatewayPorts no
X11Forwarding yes
#X11DisplayOffset 10
#X11UseLocalhost yes
#PermitTTY yes
#PrintMotd yes
#PrintLastLog yes
#TCPKeepAlive yes
#UseLogin no
#UsePrivilegeSeparation sandbox
#PermitUserEnvironment no
#Compression delayed
#ClientAliveInterval 0
#ClientAliveCountMax 3
#ShowPatchLevel no
#UseDNS yes
#PidFile /var/run/sshd.pid
#MaxStartups 10:30:100
#PermitTunnel no
#ChrootDirectory none
#VersionAddendum none# no default banner path
#Banner none# Accept locale-related environment variables
AcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES
AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
AcceptEnv XMODIFIERS# override default of no subsystems
Subsystem sftp /usr/libexec/openssh/sftp-server# Example of overriding settings on a per-user basis
#Match User anoncvs
# X11Forwarding no
# AllowTcpForwarding no
# PermitTTY no
# ForceCommand cvs server
[root@dns ~]# vim /etc/ssh/sshd_config
[root@dns ~]# grep -v ^# /etc/ssh/sshd_configPort 22HostKey /etc/ssh/ssh_host_rsa_key
HostKey /etc/ssh/ssh_host_ecdsa_key
HostKey /etc/ssh/ssh_host_ed25519_keySyslogFacility AUTHPRIVPermitRootLogin yesAuthorizedKeysFile .ssh/authorized_keysPasswordAuthentication yesChallengeResponseAuthentication noGSSAPIAuthentication yes
GSSAPICleanupCredentials noUsePAM yesX11Forwarding yesAcceptEnv LANG LC_CTYPE LC_NUMERIC LC_TIME LC_COLLATE LC_MONETARY LC_MESSAGES
AcceptEnv LC_PAPER LC_NAME LC_ADDRESS LC_TELEPHONE LC_MEASUREMENT
AcceptEnv LC_IDENTIFICATION LC_ALL LANGUAGE
AcceptEnv XMODIFIERSSubsystem sftp /usr/libexec/openssh/sftp-server[root@dns ~]# systemctl status ssh
Unit ssh.service could not be found.
[root@dns ~]# systemctl status openssh
Unit openssh.service could not be found.
[root@dns ~]# systemctl start sshd
[root@dns ~]# systemctl restart sshd
[root@dns ~]# ss -naltp |grep 22
LISTEN 0 128 *:22 *:* users:(("sshd",pid=17124,fd=3))
LISTEN 0 128 [::]:22 [::]:* users:(("sshd",pid=17124,fd=4))
[root@dns ~]# cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
polkitd:x:999:998:User for polkitd:/:/sbin/nologin
libstoragemgmt:x:998:995:daemon account for libstoragemgmt:/var/run/lsm:/sbin/nologin
colord:x:997:994:User for colord:/var/lib/colord:/sbin/nologin
rpc:x:32:32:Rpcbind Daemon:/var/lib/rpcbind:/sbin/nologin
saned:x:996:993:SANE scanner daemon user:/usr/share/sane:/sbin/nologin
gluster:x:995:992:GlusterFS daemons:/run/gluster:/sbin/nologin
saslauth:x:994:76:Saslauthd user:/run/saslauthd:/sbin/nologin
abrt:x:173:173::/etc/abrt:/sbin/nologin
setroubleshoot:x:993:990::/var/lib/setroubleshoot:/sbin/nologin
rtkit:x:172:172:RealtimeKit:/proc:/sbin/nologin
pulse:x:171:171:PulseAudio System Daemon:/var/run/pulse:/sbin/nologin
radvd:x:75:75:radvd user:/:/sbin/nologin
chrony:x:992:987::/var/lib/chrony:/sbin/nologin
unbound:x:991:986:Unbound DNS resolver:/etc/unbound:/sbin/nologin
qemu:x:107:107:qemu user:/:/sbin/nologin
tss:x:59:59:Account used by the trousers package to sandbox the tcsd daemon:/dev/null:/sbin/nologin
sssd:x:990:984:User for sssd:/:/sbin/nologin
usbmuxd:x:113:113:usbmuxd user:/:/sbin/nologin
geoclue:x:989:983:User for geoclue:/var/lib/geoclue:/sbin/nologin
ntp:x:38:38::/etc/ntp:/sbin/nologin
gdm:x:42:42::/var/lib/gdm:/sbin/nologin
rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin
nfsnobody:x:65534:65534:Anonymous NFS User:/var/lib/nfs:/sbin/nologin
gnome-initial-setup:x:988:982::/run/gnome-initial-setup/:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
avahi:x:70:70:Avahi mDNS/DNS-SD Stack:/var/run/avahi-daemon:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
tcpdump:x:72:72::/:/sbin/nologin
caozx26420:x:1000:1000:caozx26420:/home/caozx26420:/bin/bash
code:x:1001:1001::/home/code:/bin/bash
kefu:x:1002:1002::/home/kefu:/bin/bash
named:x:25:25:Named:/var/named:/sbin/nologin
[root@dns ~]# ls /tmp
ssh-9XuwiEsQ8XgO
systemd-private-3093ea58db594d8c84bcdf66911b2976-named.service-xvHwkL
systemd-private-4d77a2b81dad41e48bc3a5551955fa34-bolt.service-TXcuup
systemd-private-4d77a2b81dad41e48bc3a5551955fa34-chronyd.service-LgpulR
systemd-private-4d77a2b81dad41e48bc3a5551955fa34-colord.service-EcaN9o
systemd-private-4d77a2b81dad41e48bc3a5551955fa34-cups.service-axA2Kv
systemd-private-4d77a2b81dad41e48bc3a5551955fa34-fwupd.service-7okaXo
systemd-private-4d77a2b81dad41e48bc3a5551955fa34-rtkit-daemon.service-xhmOd5
systemd-private-9fe5775469c34f02816f374db9334d7b-bolt.service-e6DZRF
systemd-private-9fe5775469c34f02816f374db9334d7b-chronyd.service-iOFQRY
systemd-private-9fe5775469c34f02816f374db9334d7b-colord.service-LFJLfJ
systemd-private-9fe5775469c34f02816f374db9334d7b-cups.service-gIckzr
systemd-private-9fe5775469c34f02816f374db9334d7b-named.service-yt4AED
systemd-private-9fe5775469c34f02816f374db9334d7b-rtkit-daemon.service-HFecgJ
tracker-extract-files.1001
vmware-root_728-2991137345
vmware-root_736-2991268455
[root@dns ~]# ls /tmp
[root@dns ~]# tail -3 /etc/passwd
kefu:x:1002:1002::/home/kefu:/bin/bash
named:x:25:25:Named:/var/named:/sbin/nologin
yy1:x:1003:1003::/home/yy1:/bin/bash
[root@dns ~]#