kong网关集成Safeline WAF 插件
kong网关集成Safeline WAF 插件
Kong是一款轻量级、快速且灵活的开源API网关,提供了强大的插件系统。Safeline WAF(Web应用防火墙)是雷池社区版提供的一款开源Web应用防火墙,能够防护SQL注入、XSS攻击、恶意爬虫等常见Web攻击。
部署环境规划
主机清单:
| 主机名 | IP地址 | 操作系统 |
|---|---|---|
| kong | 192.168.73.12 | Ubuntu 24.04 |
| safeline | 192.168.73.11 | Ubuntu 24.04 |
| http-https-echo | 192.168.73.11 | Ubuntu 24.04 |
整体架构示意图
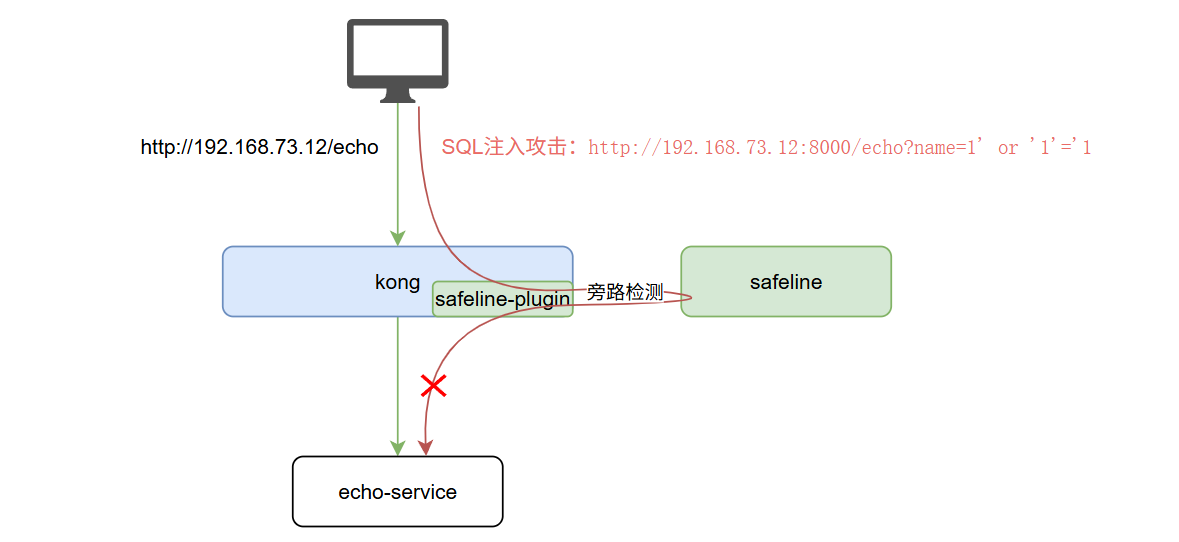
前置要求:
- 每台机器已安装docker及docker compose环境
- 已部署kong网关(基于APT源部署)
部署示例后端服务
http-https-echo 是一个非常实用的用于调试的 Docker 镜像,它可以将接收到的 HTTP 请求的各种详细信息(如请求头、请求体、查询参数等)以 JSON 格式返回给客户端。
docker run -d --name http-https-echo -p 8080:8080 mendhak/http-https-echo:31
这会在本地 8080 端口运行一个服务,用于接收 HTTP 请求并返回请求详情(包括头和正文)。您可以通过以下命令验证服务是否正常运行:
curl http://192.168.73.11:8080
预期返回 JSON 格式的响应,包含请求的头、方法和正文等信息。
注册服务到kong
将 http-https-echo 注册为 Kong 的服务 (Service)
curl -i -X POST http://192.168.73.12:8001/services \--data name=echo-service \--data url='http://192.168.73.11:8080'
为服务创建路由 (Route)
curl -i -X POST http://192.168.73.12:8001/services/echo-service/routes \--data 'name=echo-route' \--data 'paths[]=/echo' \--data "methods[]=GET" \--data "methods[]=POST" \--data 'strip_path=true'
通过 Kong 代理访问服务并验证,会看到一个 HTTP 200 OK 的响应,并且响应体是一个 JSON 对象,其中包含了您发送的请求的详细信息,例如:
root@http-https-echo:~# curl -i -X GET http://192.168.73.12:8000/echo
HTTP/1.1 200 OK
Content-Type: application/json; charset=utf-8
Content-Length: 751
Connection: keep-alive
X-Powered-By: Express
ETag: W/"2ef-+dzq6+Pv75IqQzbh/OyiSyNvank"
Date: Wed, 23 Jul 2025 16:35:21 GMT
Server: kong/3.9.1
X-Kong-Upstream-Latency: 4
X-Kong-Proxy-Latency: 0
Via: 1.1 kong/3.9.1
X-Kong-Request-Id: 13c8ae66ff702e6f93710d2bf307a315{"path": "/","headers": {"via": "1.1 kong/3.9.1","host": "192.168.73.11:8080","connection": "keep-alive","x-forwarded-for": "127.0.0.1","x-forwarded-proto": "http","x-forwarded-host": "localhost","x-forwarded-port": "8000","x-forwarded-path": "/echo","x-forwarded-prefix": "/echo","x-real-ip": "127.0.0.1","x-kong-request-id": "13c8ae66ff702e6f93710d2bf307a315","user-agent": "curl/8.5.0","accept": "*/*"},"method": "GET","body": "","fresh": false,"hostname": "localhost","ip": "127.0.0.1","ips": ["127.0.0.1"],"protocol": "http","query": {},"subdomains": [],"xhr": false,"os": {"hostname": "8e1197a87aeb"},"connection": {}
}
部署Safeline
一键安装:3 分钟即可完成自动安装。在http-https-echo节点执行
bash -c "$(curl -fsSLk https://waf-ce.chaitin.cn/release/latest/manager.sh)"
命令执行成功则代表雷池安装成功,现在你可以访问雷池控制台了
......
[INFO 10:55:45]: 正在启动 Docker 容器
[INFO 10:55:56]: 雷池 WAF 安装完成
[INFO 10:55:56]: 等待 mgt 启动
[INFO 10:56:01]: 等待 mgt 启动
[INFO 10:56:06]: 等待 mgt 启动
[INFO 10:56:11]: 等待 mgt 启动
[INFO 10:56:16]: 等待 mgt 启动
[INFO 10:56:21]: 等待 mgt 启动
[INFO 10:56:27]: 等待 mgt 启动
[INFO 10:56:32]: 设置 admin
[INFO 10:56:33]:
[INFO] Initial username:admin
[INFO] Initial password:82dOMjk7
[INFO] Done
[INFO 10:56:33]: 雷池 WAF 管理面板: https://192.168.73.11:9443/
[INFO 10:56:33]: 雷池 WAF 管理面板: https://0.0.0.0:9443/
查看安装目录
root@http-https-echo:~# ls /data/safeline/
docker-compose.yaml logs resources
访问管理面板
配置SafeLine 插件检测引擎地址和端口
要为特定服务启用 SafeLine 插件,需配置 detector_host 和 safeline_port 参数,这两个参数分别对应 SafeLine 检测引擎的地址和端口,与初始设置时的配置一致。
调整saveline配置,暴露检测引擎地址和端口,增加 8000:8000 端口映射
root@http-https-echo:~# cat /data/safeline/docker-compose.yaml
services:detect:container_name: safeline-detectorrestart: alwaysimage: ${IMAGE_PREFIX}/safeline-detector${REGION}${ARCH_SUFFIX}:${IMAGE_TAG}volumes:- ${SAFELINE_DIR}/resources/detector:/resources/detector- ${SAFELINE_DIR}/logs/detector:/logs/detector- /etc/localtime:/etc/localtime:roenvironment:- LOG_DIR=/logs/detectorports:- 8000:8000networks:safeline-ce:ipv4_address: ${SUBNET_PREFIX}.5
调整配置文件
root@http-https-echo:~# cat /data/safeline/resources/detector/detector.yml
bind_addr: 0.0.0.0
listen_port: 8000
启用Safeline插件
可通过 LuaRocks 安装自定义插件。Lua 插件以 .rock 格式包分发,这些包自成一体,支持从本地或远程服务器进行安装。
如果您通过官方软件包安装了 Kong,系统中应该已包含 LuaRocks 工具。
项目地址:https://github.com/chaitin/kong-safeline
在kong网关节点,安装 SafeLine 插件请按以下步骤操作:
root@kong:~# luarocks install kong-safeline
查看插件源文件
root@kong:~# ls /usr/local/share/lua/5.1/kong/plugins/safeline
handler.lua schema.lua
接着在 kong.conf 配置文件中添加以下内容以启用 SafeLine 插件:
root@kong:~# cat /etc/kong/kong.conf
plugins = bundled,safeline
该配置行将 SafeLine 添加至已启用插件列表,与官方发行版中捆绑的插件共同生效。
最后,重启 Kong 网关:
systemctl restart kong
检查插件是否加载成功,确认返回的插件列表存在safeline
root@kong:~# curl -s http://192.168.73.12:8001/plugins/enabled | jq |grep safeline
{"enabled_plugins": ["grpc-gateway","grpc-web","pre-function","post-function","azure-functions","zipkin","opentelemetry","ai-proxy","ai-prompt-decorator","ai-prompt-template","ai-prompt-guard","ai-request-transformer","ai-response-transformer","standard-webhooks","modify-headers-and-body","safeline","redirect","jwt","acl","correlation-id","cors","oauth2","tcp-log","udp-log","file-log","http-log","key-auth","hmac-auth","basic-auth","ip-restriction","request-transformer","response-transformer","request-size-limiting","rate-limiting","response-ratelimiting","syslog","loggly","datadog","ldap-auth","statsd","bot-detection","aws-lambda","request-termination","prometheus","proxy-cache","session","acme"]
}
在echo-service服务上启用SafeLine
curl -X POST http://192.168.73.12:8001/services/echo-service/plugins \--data "name=safeline" \--data "config.host=192.168.73.11" \--data "config.port=8000" \--data "config.mode=block"
测试防护效果
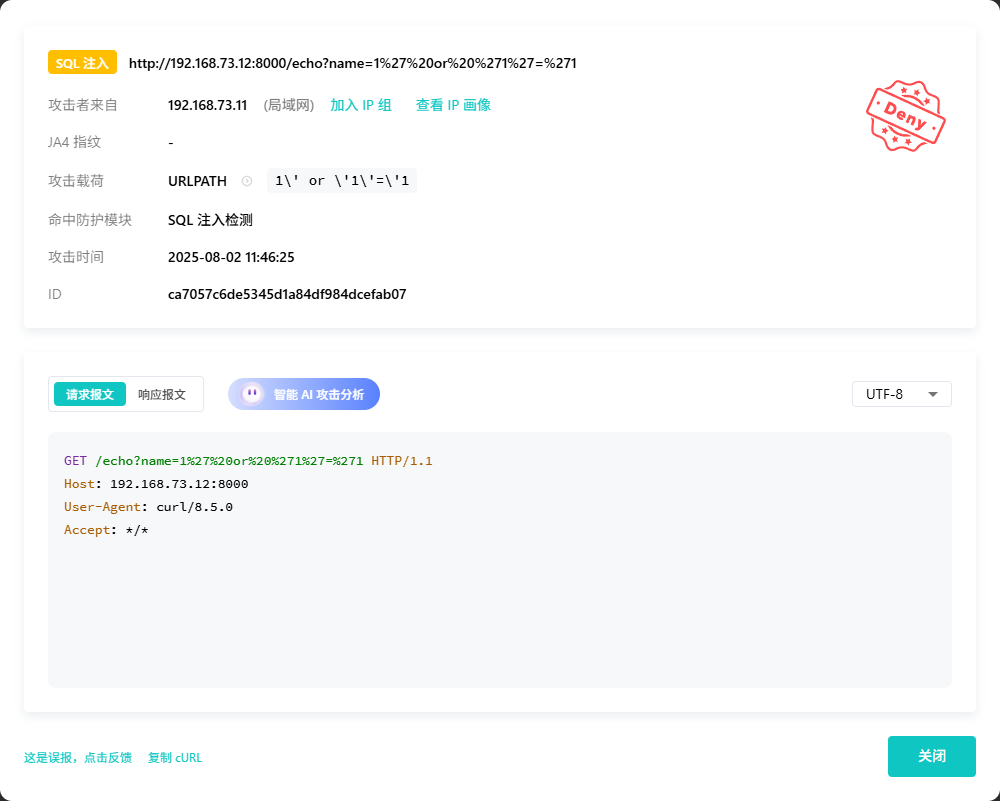
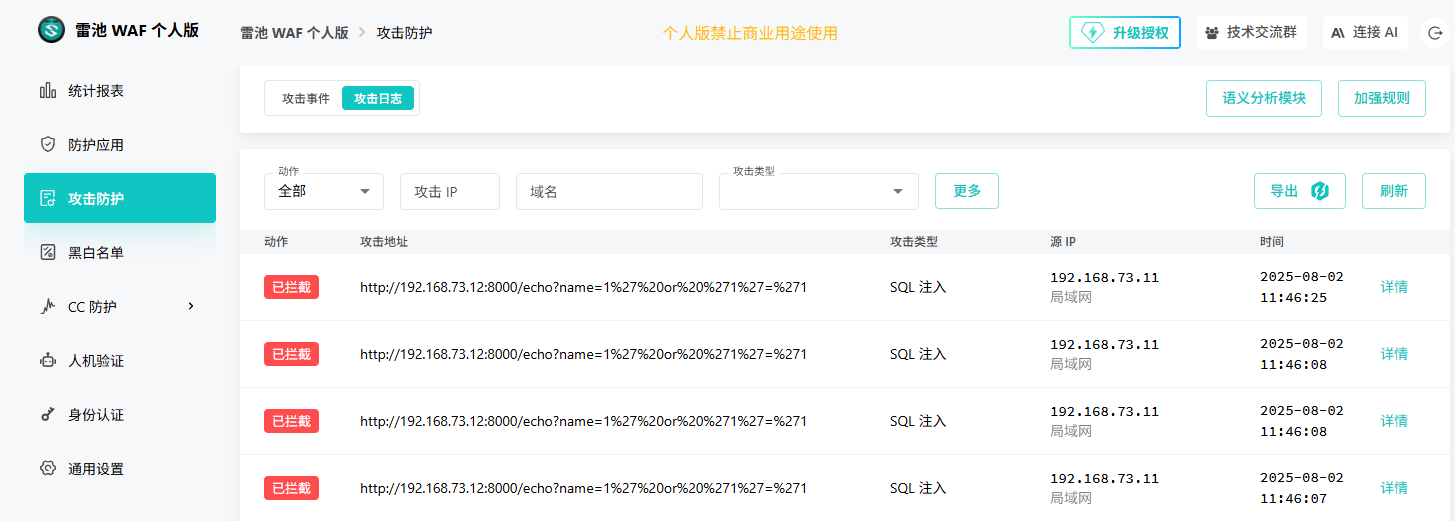
验证 SafeLine 是否生效时,可通过向 Kong 发送模拟 SQL 注入攻击的请求进行测试。若 SafeLine 已成功保护您的服务,您将收到 403 Forbidden 响应。
原始请求路径
curl -X GET "http://192.168.73.12:8000/echo?name=1' or '1'='1"
对 URL 中的参数进行 URL 编码
curl -X GET "http://192.168.73.12:8000/echo?name=1%27%20or%20%271%27=%271"
解释:
'=>%27- 空格 =>
%20 - 整个 payload
1' or '1'='1被编码为1%27%20or%20%271%27=%271
如果被雷池 WAF 成功拦截,你将看到返回 HTTP 403 和如下 JSON:
root@http-https-echo:~# curl -s -X GET "http://192.168.73.12:8000/echo?name=1%27%20or%20%271%27=%271" | jq
{"code": 403,"success": false,"message": "blocked by Chaitin SafeLine Web Application Firewall","event_id": "ca7057c6de5345d1a84df984dcefab07"
}
此外,还可以查看 [SafeLine 控制面板]以查看被拦截攻击的完整记录。
详情信息